In a business environment, you may hear colleagues wonder: how does an IT audit differ from a security assessment? These two terms are tossed around interchangeably, along with IT risk assessment, security audit, and so on. However, IT audit vs. IT security assessment mean different things, and it’s important to understand the nuances. If you have a “security assessment” in mind, but you’re actually facing an audit, you could risk being woefully unprepared for what’s expected of you. In addition, assessments and audits can help you identify and prepare for cybersecurity concerns, which is ultimately good for your business and customer trust.
Security Audits and Assessments
What Is the Purpose of an IT Security Audit?
IT Audit vs. IT Security Assessment
How to Ensure Security Audit Success With the Right Tools
Security Audits and Assessments
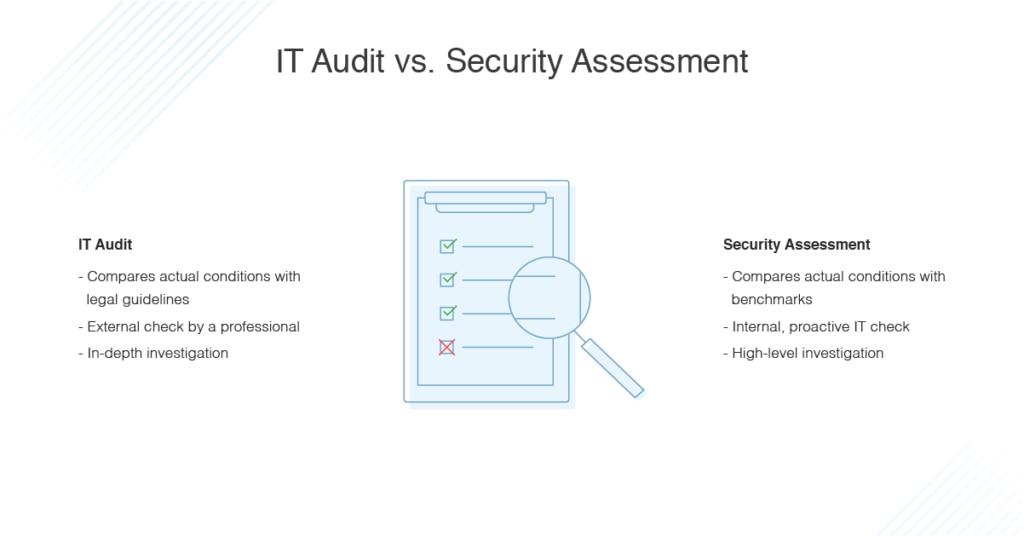
First, let’s look at security audits and assessments. The primary difference between an audit and an assessment is an assessment takes place internally, while an audit is a measurement of how well an organization is meeting a set of external standards.
A security assessment is an internal check typically in advance of, and in preparation for, the security audit. An assessment is essentially looking at how things should be, and then comparing how things actually are with this benchmark. With a preemptive assessment, there’s time and scope to remedy any issues if any clear vulnerabilities or holes exist. Information for a security assessment is usually collected in a few different ways, including surveys, interviews, comparison with external standards, statistics, or reviews of records and reports showing historical information.
These assessments can either be carried out by an internal team tasked with risk analysis and compliance, or you can also hire a third-party organization to perform the check. In general, an assessment is usually a more high-level look at compliance, rather than a deep dive into the details. Assessments should be conducted at least on a yearly basis, if not more frequently (e.g., every six months). In addition, assessments should be undertaken any time there’s a major structural change to the business, to help determine whether any new risk factors have arisen.
What Is the Purpose of an IT Security Audit?
The primary purpose of a security audit is to check whether a business is complying with a set of external legal standards or guidelines. An audit is performed by a third-party, an auditor, who is a qualified or certified professional. An example of a security audit would be something like the PCI Security Standards Council requiring a full PCI Report on Compliance (ROC). Another example would be an audit performed to check whether a health organization is dealing properly with private patient health data for HIPAA purposes.
A security audit goes deeper than a security assessment, and looks at all the technology, controls, and policies and procedures you have in place, to determine whether relevant standards and regulations are being complied with properly. Instead of just checking to see what measures are in place, an audit tests these components to ensure they’re functional, would be effective in a security event, and determine whether they meet the standards you’re being held to.
A security audit involves searching for holes in policies or procedures, while also performing a physical assessment of what hardware and devices you have as part of your infrastructure. Security audits also involve an assessment of access control and vulnerabilities, to ensure permissions and access are correctly configured and there are no software, hardware, or policy vulnerabilities that could lead to a breach or intrusion. Audits will also look at your design processes to examine how you create your services and system setups. Security audits review all your standard operating procedures and your backup disaster recovery and general disaster recovery plans.
Unlike a security assessment, an audit usually has a set timeframe. In general, you can think of an assessment as the check you do inside your business to make sure you have everything in place and working for when an audit is eventually performed.
IT Audit vs. IT Security Assessment
Now let’s look at what happens during an IT audit and an IT security assessment. Risk assessment is something you should have done to prepare for either type of analysis, as you’ll need to have spotted all your risk points and created mitigation plans to close any loopholes and take care of any vulnerabilities.
An IT security assessment covers things like network security, disaster recovery, protections and failovers for data and server functionality, and general data security and protection. It would also assess whether you have firewalls and antivirus software in place, and what processes you have generally in place to protect any sensitive data in your systems.
An IT audit would go through and check compliance at several different levels. For example, if you deal with health data subject to HIPAA, an IT audit would first check what kind of access rights management and access controls you have in place. This would help ensure only the necessary people have access to personal medical data, and no unauthorized users can access it.
In addition, an IT audit risk assessment would check what anti-malware and antivirus software you have in place, and what sort of firewalls exist on your network. If you use monitoring tools, auditing can check your reports to see what kind of security events occurred, how you responded, what preventative measures you have in place, and the alerting systems you use to stay on top of risks.
How to Ensure Security Audit Success With the Right Tools
IT audits and IT security assessments are two different parts of the same process: one internal and preparatory, the other externally-reviewed and rigorously tested. By conducting IT security assessments, you can ensure when your IT audit takes place you’ll meet the required standards and comply with all relevant legislation. Risk management in all forms is vitally important, so make sure to have clear processes in place and use appropriate tools to streamline the process and keep all your assessments accurate and clear.
There are numerous tools you can use to ensure you comply with relevant standards, but one of the best is SolarWinds® Access Rights Manager (ARM). This tool can help you ensure you follow appropriate security policies for detecting data risks. Tools like ARM can centralize user identities and access rights, so when you perform an IT security audit, you can more easily see which users are high risk, and which accounts have high levels of access. It can also automate your user authentication process, which can help to ensure you don’t miss any key users or authentication steps. In addition, SolarWinds ARM can centralize Active Directory resources for risk assessment purposes.
Access rights management tools can help you meet your compliance requirements for IT security audits, and you can use them in your security assessment processes to prepare for audits to come.
