Network security predominantly falls into two different categories: on-premises and cloud-based. Enterprises choose which one they use to protect their system by considering several factors including individual needs and operational costs. Both approaches are concerned with keeping a network as secure as possible, but cloud security measures get the most scrutiny.
So, which is it? Is the cloud more secure than on-premises security? I’ll answer that with another question. Is the cloud vs. network security debate as necessary as we think it is? In this article, I’ll unpack this issue and recommend a tool capable of helping you monitor your network security, no matter which camp you belong to.
Cloud vs. On-Premises: Understanding the Security Differences
Cloud or cloud computing security refers to the set of procedures, technologies, policies, and controls that come together to protect information on cloud-based servers. It’s a centralized approach to security capable of protecting sensitive data, supporting compliance efforts, and setting authentication rules.
Since the cloud is responsible for negotiating a bunch of different endpoints which may or may not be close to one another, cloud security boasts a centralized core. With everything in one place traffic analysis is much easier and network monitoring takes a fraction of the time. Cloud security is also typically cheaper because you don’t have to spend money on dedicated hardware, plus you don’t have to constantly monitor security.
On-premises security, on the other hand, is exactly what it sounds like—security measures physically on the premises of a business. On-premises security refers to both the rules and tools in place to protect the security and accessibility of computer networks, including both hardware and software. Some examples include firewalls, VPNs, and antivirus software—along with physical security measures.
Indeed, security threats can happen anywhere in your organization and at any level, so if you choose on-premises security you must install a range of sufficient measures. For example, your first line of defense might be biometric locks in certain rooms. But what if a disgruntled former employee who still has access privileges bypasses the lock and gets into the server room? Then you need a separate layer of security to protect the inner workings of your network. Clearly, ensuring top-notch, on-premises security can get complicated, as it involves both physical security and traditional IT security measures.
Cloud vs. On-Premises Comparison
Still confused about the security benefits and issues for each type of IT environment? Here’s a straightforward look at cloud security vs. on-premises security side by side.
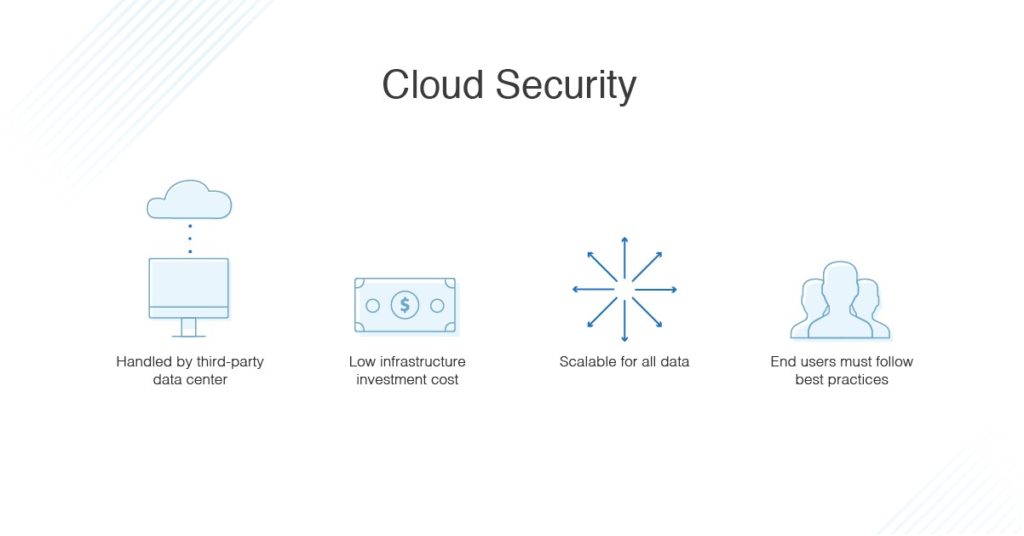
Cloud-based security:
- Security is the responsibility of both the enterprise and the vendor providing the software, meaning there’s less of a burden on IT teams
- Cloud security is highly automated thanks to APIs, which can mean less work for IT staff members
- Since you can access your files anywhere, your security goes everywhere with you, too
- Since everything in the cloud is located in a centralized platform security, boundaries are no obstacle
- Cloud security may offer specialized options otherwise out of reach because of cost
- Public cloud-based services involves trusting a third-party with your most precious data—but on the other hand, they’re experts
- You should ensure your cloud provider allows for compliance with necessary regulations
- Some cloud-based security services are pre-configured, so if you don’t like the way the system is set up, you may not have options
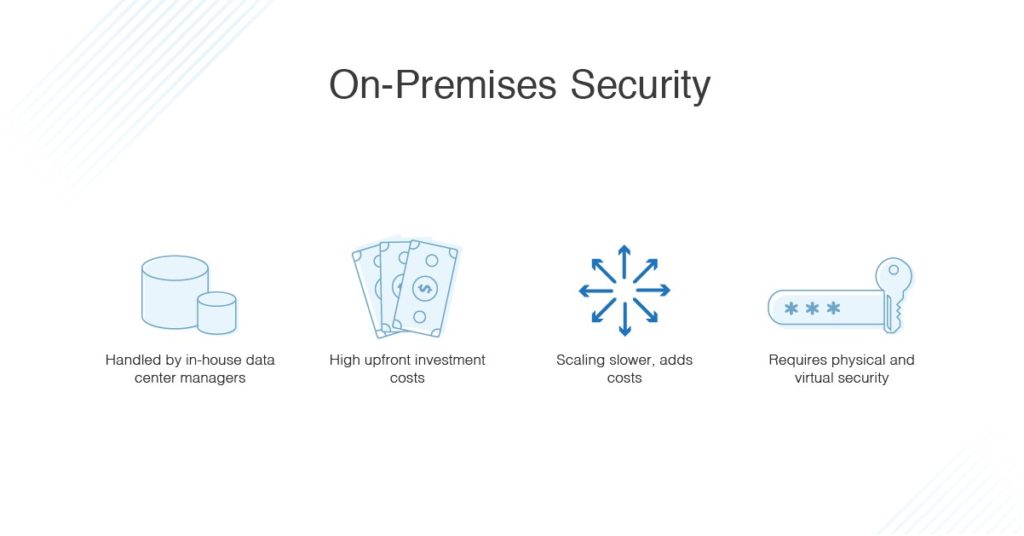
On-premises security:
- On-premises security might as well be a synonym for “hands-on security.” With this approach, security is your responsibility and yours alone. This means constant monitoring and maintenance.
- You get to retain all of your data and remain in control of what happens to it.
- Complete on-premises security includes both physical and network security measures, especially if you need to stay within compliance.
- On-premises allows you to configure your system the way you like it, but this means you need a high level of expertise.
- Separate and sometimes costly security tools are needed to protect each layer of an enterprise.
- Security measures and resources are limited by location.
Is Cloud More Secure Than On-Premises?
Answering the question posed above is complicated because the major arguments in the great cloud versus network security debate could apply to either side.
Let’s take the number one security concern out there: “I want my information to be protected in case of a data security breach.” Many people are nervous about storing their sensitive information in the cloud because they don’t fully understand it or the thought of having your stuff floating up there in the ether can be a little unnerving. One of the benefits of on-premises security is it’s tangible and requires human maintenance. Some people might feel more secure knowing there’s a human person tinkering away in the basement, making sure the enterprise’s security measures don’t spontaneously combust.
Also, on-premises doesn’t necessarily mean more secure or error-free just because it doesn’t rely on automation. In fact, the very opposite could easily be true. Human error can just as easily affect on-premises security as it could cloud-based security.
Basically, the cloud is no more or less secure than on-premises security because people on both sides can make mistakes and compromise security. If you employ cybersecurity best practices, barring outside tampering, your network will be as secure as it can be. A better question would be, “Which of these options makes the most sense for my security needs?”—thereby shifting the focus from good vs. bad to pros vs. cons.
Secure Cloud and On-Premises Security Tools
It’s up to you whether or not you choose cloud-based security measures over on-premise. With the right security management tool, either approach can give you everything you need to protect your network. My favorite cybersecurity tool at the moment is SolarWinds Security Event Manager (SEM). This tool is built to track security issues based on log data from across on-premise, cloud, and even hybrid environments.
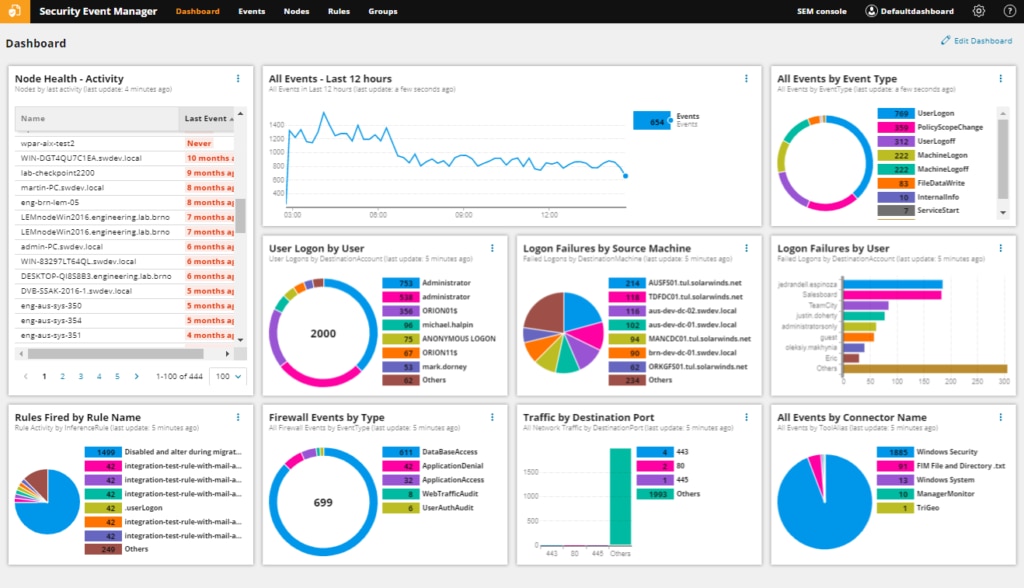
SEM’s comprehensive cyber threat intelligence tool is designed to make it easy to manage cybersecurity threats before they happen. Live threat intelligence feeds consolidate and analyze all your data in one place, so it’s easier to see when something is amiss. SEM keeps a database of known threats, cross-references incoming potential threats against the list, and lets you know when the threat threshold has been met. This functionality helps you keep an eye out for threats before they do damage. Built-in automated responses can also automatically block IPs, disable accounts, block USB devices, and take other security measures in response to a threat.