What Is File Integrity Monitoring (FIM)?
File Integrity Monitoring (FIM) is a cybersecurity practice employing dedicated FIM tools for monitoring critical system files, directories, OS components, network devices, and more to detect any unauthorized changes. FIM tools rely on different verification methods to compare a current file state with a baseline state and raise alerts in case there’s a suspicious change as per the predefined policies.
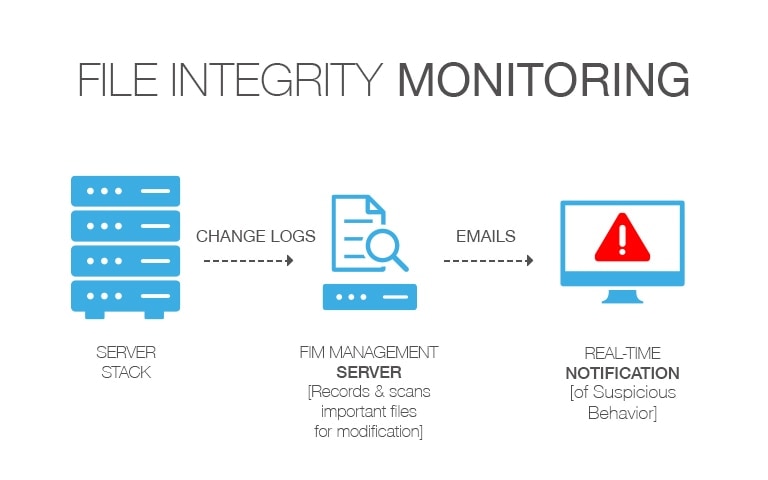
Most security information and event management (SIEM) tools offer file integrity monitoring features, an essential part of intrusion detection. These tools allow administrators to track file changes and provide them with all the logs to ascertain if the changes were authorized or need any remedial action.
Why Is File Integrity Monitoring Important?
Threat actors often employ sophisticated malware to alter registry files and other critical data on enterprise servers and workstations for malicious purposes. With privileged access, they can compromise vital business data and personally identifiable information or disrupt mission-critical applications without being detected. This is the main reason security practitioners and IT teams in enterprises consider file integrity monitoring an important layer of defense against a range of malware and threat vectors. Besides, standards such as PCI-DSS and ISO 17799 require organizations across several industries to implement FIM controls.
Outlined below are some major areas where an FIM tool is helpful:
- IT ecosystem monitoring: IT teams employ FIM tools to monitor their servers, VMs and hypervisor configurations, network devices, databases, Active Directory, PoS solutions, and critical workstations.
- Real-time awareness: File integrity monitoring, sometimes available standalone or as a part of a SIEM product like SolarWinds® Security Event Manager, can help in getting real-time notifications for important changes in files and configurations.
- Compliance reporting: Many industries have stringent compliance and regulatory mandates for businesses to not only secure their data but also to demonstrate how they ensure security. FIM tools help in creating automated reports to meet these complex requirements.
How Do File Integrity Monitoring Tools Work?
To detect changes in files and configurations, FIM tools create an initial baseline including different file attributes and a cryptographic hash signature, which can’t be altered by anyone afterward. Any changes in files, either authorized or unauthorized, lead to changes in their hash values. FIM tools leverage these hash values and easily detect changes in a file, without needing to skim through the entire file to find any edits, deletion, or alteration.
There are many agent-based and agentless cloud-based FIM tools available in the market with proprietary algorithms and technology. While there can be a high overlap in the features offered by all these tools, a major point of difference lies in their method of monitoring the hash values. Some tools perform this monitoring at random intervals, while others perform it a defined polling interval or on a real-time basis. We’ll discuss some of these popular tools in the following section.
Top 5 File Integrity Monitoring tools
1. OSSEC
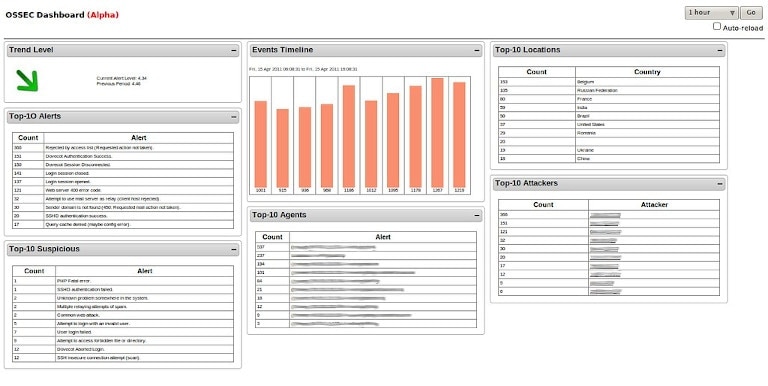
OSSEC is an open-source intrusion detection system offering FIM capabilities with its Syscheck feature. By default, Syscheck runs every six hours to check for hash values of files. IT teams can configure this frequency as per their requirements. OSSEC is known for its scalability and runs on Windows, different Linux distributions, and macOS. It has a server-agent model with reduced CPU usage, which makes it easier to install and manage. However, it lacks root-kit detection on Windows. Further, as it is an open-source tool, teams have to rely on community support for resolving any issues.
2. SolarWinds Security Event Manager (SEM)
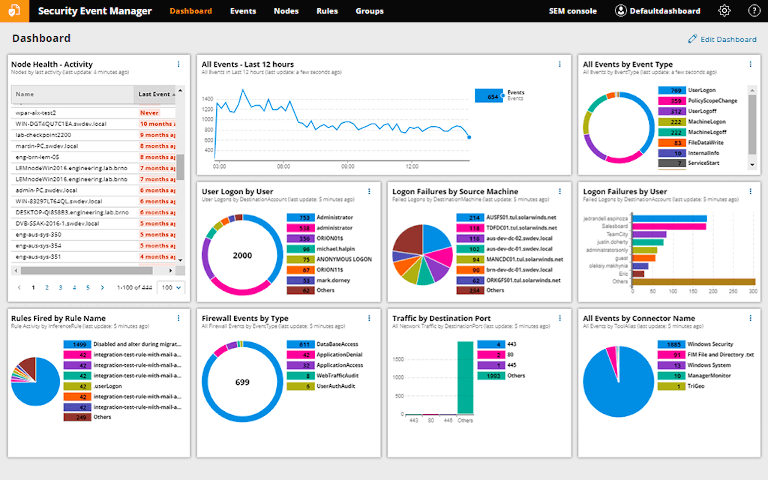
Formerly called Log & Event Manager, SEM is a centralized log management solution. It offers a built-in file integrity monitoring feature to detect unauthorized modifications to configurations, executable files, logs, databases, and more. With SEM, IT teams can also track users’ activities before and after a file change. This information can be crucial in forensic analysis or defining real-time alerts. To add another layer of security, IT teams can also consider using SolarWinds Server & Application Monitor, which includes 1,200-plus application monitoring templates. These templates simplify monitoring across private, public, and hybrid cloud environments.
3. Tripwire
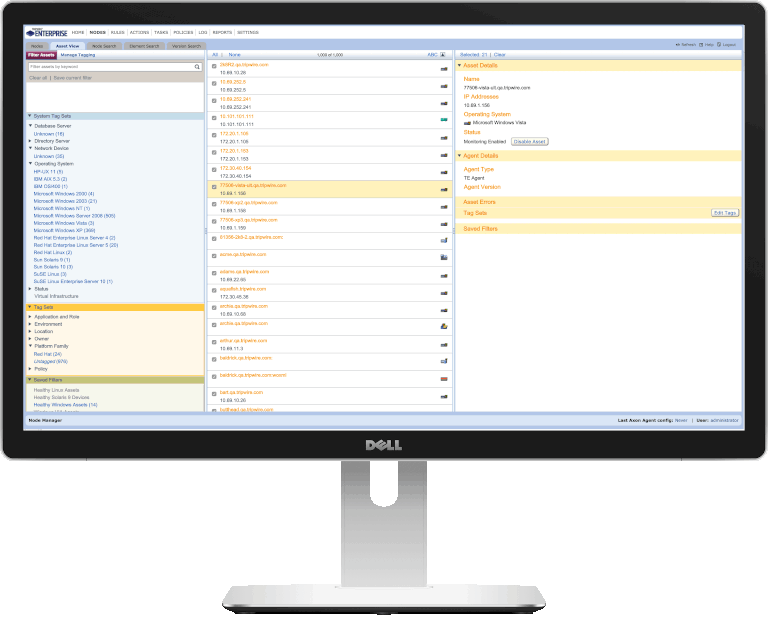
Tripwire is a known name in intrusion detection and file integrity monitoring. It claims to filter random alerts from critical security or compliance risks intelligently. The solution can integrate with different SCM, SIEM, and log management tools. Teams can choose to export their FIM data to the Tripwire log center or their preferred SIEM solution. It also offers automated alerts and remedial actions based on predefined rules.
4. Qualys FIM
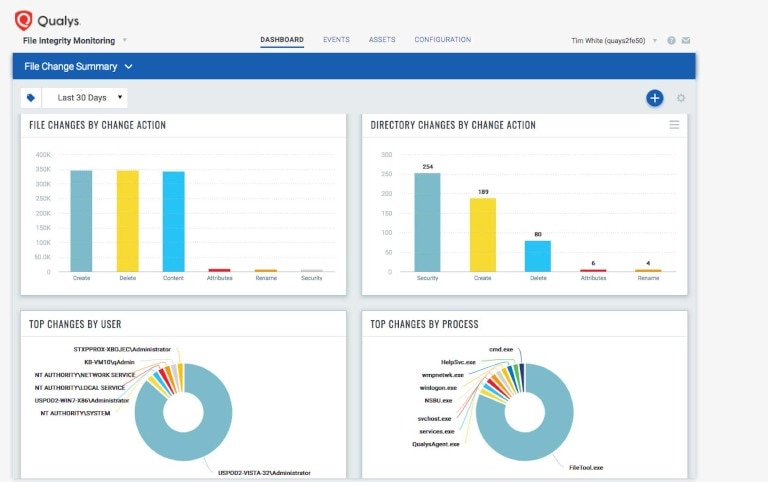
Qualys FIM is a cloud application to centrally log file changes. Its cloud-based setup helps IT teams in getting started quickly without facing any hardware or configuration related challenges. It offers preconfigured file monitoring templates and real-time change detection capabilities. The solution has a limited impact on workstations and other endpoints, as it sends all the data to the cloud for heavy analysis and correlation. It’s a good fit for organizations seeking a scalable and lightweight FIM solution.
5. Trustwave Endpoint Protection
Trustwave offers FIM as part of its Endpoint Protection Suite. This makes it a good option for those willing to implement the entire suite in their organization. Like Qualys FIM, it’s a cloud-based solution with lightweight agent technology. Teams can assign different priorities to file changes to identify critical changes first. For further data analysis, the tool provides FIM data in .csv, Excel, and PDF formats.
File integrity monitoring becomes hectic if IT teams don’t configure their tools properly. Many times, teams have limited means to wade through the noise created due to frequent changes in files. It becomes challenging to differentiate the regular changes from suspicious ones. Also, many tools create arcane logs, lacking sufficient insights and actionable intelligence. Therefore, while selecting an FIM tool, organizations should look to solutions offering easy controls and intelligent insights instead of tools requiring lengthy configuration and manual analysis.
