Wondering if your IT infrastructure is secure? You may need to consider an IT security audit, which can provide invaluable information about your security controls.
Risk management audits force us to be vulnerable, exposing all our systems and strategies. They’re uncomfortable, but they’re undeniably worth it. They help us stay ahead of insider threats, security breaches, and other cyberattacks that put our company’s security, reputation, and finances on the line. So, rather than live in fear of audits, let’s get comfortable with them. I’ve outlined everything you need to know about security control audits—what they are, how they work, and more.
Preparing for an IT security audit doesn’t have to be a solo endeavor. I recommend recruiting the help of a third-party software platform to help you aggregate your information and continuously monitor the data security strategies you have in place. My favorite products—both from SolarWinds—are Security Event Manager and Access Rights Manager, which I’ll detail in this article.
What Is the Main Purpose of a Security Audit?
A network security audit is a technical assessment of an organization’s IT infrastructure—their operating systems, applications, and more. But before we dig into the varying types of audits, let’s first discuss who can conduct an audit in the first place.
- Internal Auditors: For smaller companies, the role of an internal auditor may be filled by a senior-level IT manager within the organization. This employee is responsible for building robust audit reports for C-suite executives and external security compliance officers. Larger companies tend to take this one step further, hiring designated Corporate Internal Auditors. These individuals usually have an impressive background as a Certified Information Systems Auditor, Certified Internet Audit Professional, or certified accountant.
- External Auditors: An external auditor takes many forms, depending on the nature of the company and the purpose of the audit being conducted. While some external auditors hail from federal or state government offices (like the Health and Human Services Office for Civil Rights), others belong to third-party auditing companies specializing in technology auditing. These auditors are hired when certain compliance frameworks, like SOX compliance, require it.
- Now that we know who can conduct an audit and for what purpose, let’s look at the two main types of audits.
- Manual Audits: A manual audit can be performed by an internal or external auditor. During this type of audit, the auditor will interview your employees, conduct security and vulnerability scans, evaluate physical access to systems, and analyze your application and operating system access controls.
- Automated Audits: An automated audit is a computer-assisted audit technique, also known as a CAAT. These audits are run by robust software and produce comprehensive, customizable audit reports suitable for internal executives and external auditors. Advanced auditing software will even provide an extra layer of security, continuously monitoring the IT infrastructure and alerting IT technicians when suspicious activity occurs and when predetermined security thresholds have been crossed.
How Often Should Security Audits Be Performed, and Why?
IT auditing and cybersecurity go hand-in-hand. In-depth financial details and other highly sensitive data about employees, clients, and customers are common within your IT infrastructure. Cyberattackers lurk in the shadows, waiting for—and creating—opportunities to strike and access this trove of data. That’s why you put security procedures and practices in place. But what if you missed a recent patch update, or if the new system your team implemented wasn’t installed entirely correctly?
Every system administrator needs to know ASAP if the safety of their IT infrastructure is in jeopardy. Conducting annual audits helps you identify weaknesses early and put proper patches in place to keep attackers at bay. They also empower you to establish a security baseline, one you can use regularly to see how you’ve progressed, and which areas are still in need of improvement.
At the bare minimum, ensure you’re conducting some form of audit annually. Many IT teams choose to audit more regularly, whether for their own security preferences or to demonstrate compliance to a new or prospective client. Certain compliance frameworks may also require audits more or less often.
What Are Common IT Security Audit Standards?
A slew of IT security standards require an audit. While some apply broadly to the IT industry, many are more sector-specific, pertaining directly, for instance, to healthcare or financial institutions. Below is a short list of some of the most-discussed IT security standards in existence today.
- ISO Compliance: The International Organization for Standardization (ISO) develops and publishes an array of guidelines designed to ensure quality, reliability, and safety. The ISO/IEC 27000 family of standards are some of the most relevant to system administrators, as these standards focus on keeping information assets secure. The ISO/IEC 27001 is known for its information security management system requirements.
- HIPAA Security Rule: The HIPAA Security Rule outlines specific guidelines pertaining to exactly how organizations should protect patients’ electronic personal health information.
- PCI DSS Compliance: The PCI DSS compliance standard applies directly to companies dealing with any sort of customer payment. Think of this standard as the requirement responsible for making sure your credit card information is protected every time you conduct a transaction. Conducting PCI DSS compliance is no easy task and I recommend using software like SolarWinds® Security Event Manager to help you navigate the audit processes.
- SOX Compliance: The SOX Act, known more formally as the Sarbanes-Oxley Act after its sponsors Senator Paul Sarbanes (D-MD) and Representative Michael G. Oxley (R-OOH-4), was passed in 2002 following the highly publicized Enron scandal. The goal was to protect investors by requiring all public companies to provide accurate, reliable financial disclosures on an annual basis.
Security Audit Best Practices
Whether conducting your own internal audit or preparing for an external auditor, several best practices can be put in place to help ensure the entire process runs smoothly. While you might not be able to implement every measure immediately, it’s critical for you to work toward IT security across your organization—if you don’t, the consequences could be costly.
- Get Back to Basics: You need to know where you stand and what “normal” operating system behavior looks like before you can monitor growth and pinpoint suspicious activity. This is where establishing a security baseline, as I mentioned previously, comes into play. If you haven’t yet identified your security baseline, I suggest working with at least one external auditor to do so. You can also construct your own baseline with the help of monitoring and reporting software.
- Practice Preparedness: The details you need to gather for a security risk assessment are often scattered across multiple security management consoles. Tracking down all these details is a headache-inducing and time-consuming task, so don’t wait until the last minute. Strive to centralize your user account permissions, event logs, etc., in one easy-to-access platform via a third-party management tool. This helps ensure you’re prepared when compliance auditors come knocking. If you’re hiring an external auditor, it’s also important to practice preparedness by outlining—in detail—all your security objectives. In doing so, your auditor is equipped with a complete picture of exactly what they’re auditing.
- Make It a Team Effort: Protecting internal, highly sensitive data shouldn’t rest solely on the shoulders of the system administrator. Everyone within your organization needs to be on board. So, while hiring a third-party auditing expert or purchasing a robust auditing platform comes at a price—one many C-suite executives may question—they pay for themselves in the value they bring to the table. With the right auditing tool in hand or expert by your side, you can better ensure the safety and security of your entire IT infrastructure. These resources identify system weaknesses before hackers do and help ensure you’re compliant with relevant industry regulations. Build a convincing case and arm yourself with the tools and talent you need to protect your company.
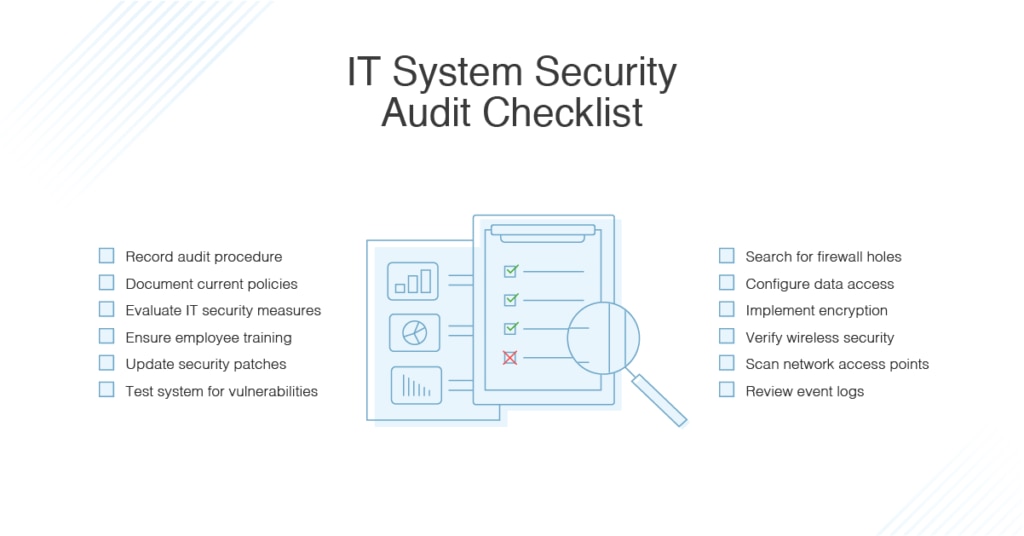
IT System Security Audit Checklist
Assessing the security of your IT infrastructure and preparing for a security audit can be overwhelming. To help streamline the process, I’ve created a simple, straightforward checklist for your use. Not every item may apply to your network, but this should serve as a sound starting point for any system administrator.
- Record all audit details, including who’s performing the audit and what network is being audited, so you have these details on hand.
- Document all current security policies and procedures for easy access.
- Evaluate activity logs to determine if all IT staff have performed the necessary safety policies and procedures.
- Identify which employees have been trained to identify security threats, and which still require training.
- Analyze your security patches to ensure everything is up to date.
- Conduct a self-test on your existing software to identify any vulnerabilities.
- Search for any holes within your existing firewall.
- Double-check exactly who has access to sensitive data and where said data is stored within your network.
- Implement all encryption best practices where appropriate.
- Verify the security of every one of your wireless networks.
- Conduct a scan to identify every network access point.
- Regularly review event logs to keep human error at a minimum.
Best Automated Audit Assessment Tools
A vast array of third-party software tools exist to help you streamline your auditing endeavors and protect your IT infrastructure, but which one is right for you? I’ve outlined a few of my favorites below to help you find the right fit.
SolarWinds Access Rights Manager
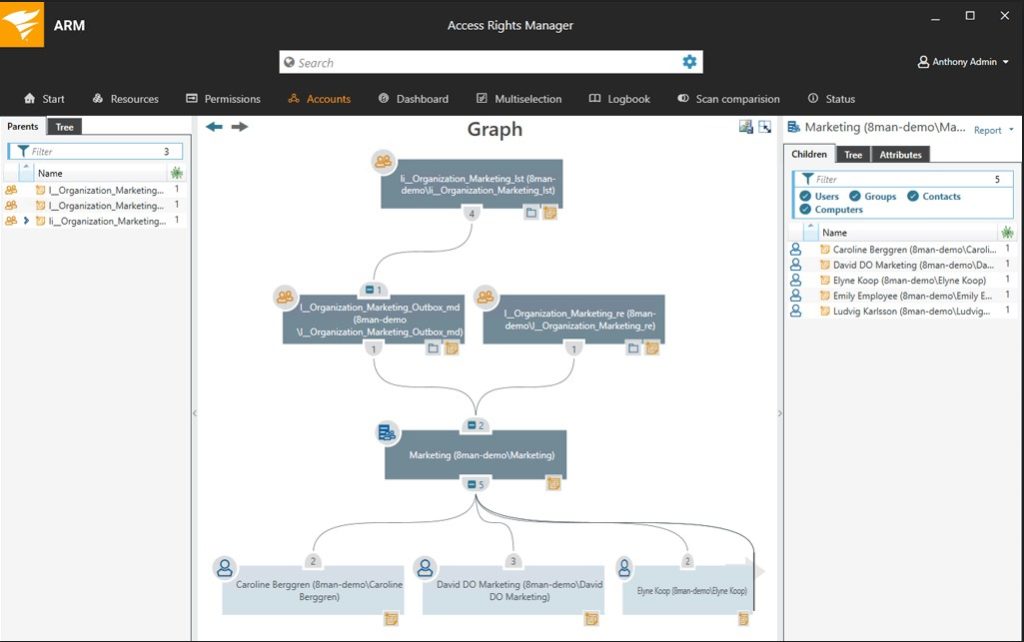
Access Rights Manager (ARM) from SolarWinds provides extensive automation and centralization. To start, this tool aggregates all log files and user account permissions, providing you with in-depth visibility into your IT infrastructure via one easy-to-access dashboard. This allows you to identify and respond to threats more quickly, and helps you gather audit-ready information at a moment’s notice. From an automation standpoint, I love how ARM allows its users to automatically deprovision accounts once predetermined thresholds have been crossed. This helps system administrators mitigate threats and keep attackers at bay. But that’s not all—you can even leverage the tool’s built-in templates to create auditor-ready reports on-demand. Try the free 30-day trial and see for yourself.
SolarWinds Security Event Manager
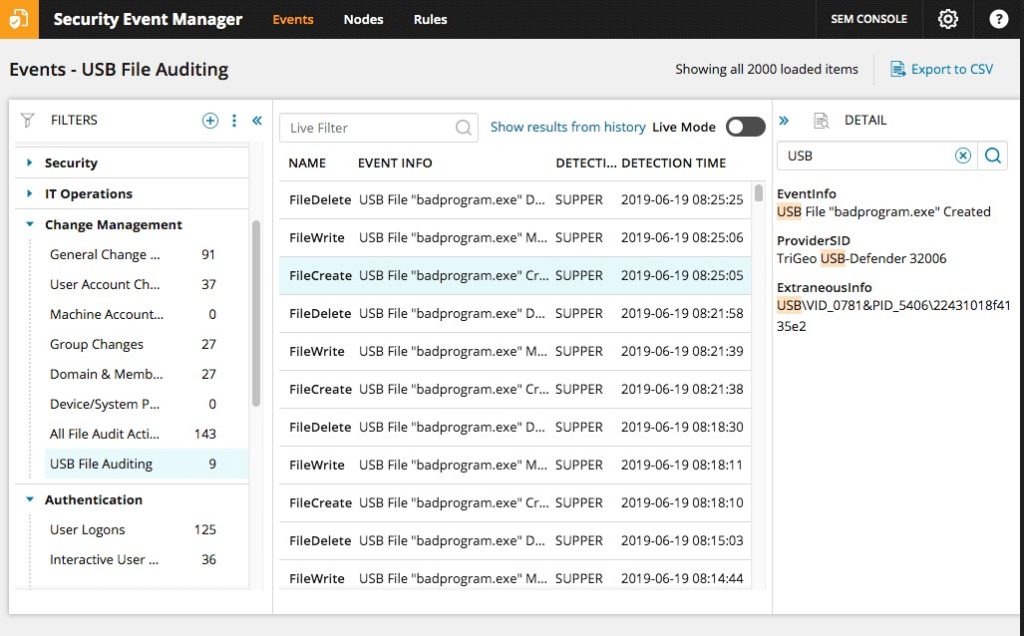
SolarWinds Security Event Manager is a comprehensive security information and event management (SIEM) solution designed to collect and consolidate all logs and events from your firewalls, servers, routers, etc., in real time. This helps you monitor the integrity of your files and folders while identifying attacks and threat patterns the moment they occur. The platform also boasts more than 300 compliance report templates in addition to customizable template options, helping you demonstrate regulatory compliance with a few simple clicks. But don’t take my word for it—try the free trial today.
ManageEngine EventLog Manager
The EventLog Manager from ManageEngine is a log management, auditing, and IT compliance tool. System administrators can leverage this platform to conduct both historic forensic analysis on past events and real-time pattern matching to minimize the occurrence of security breaches. Like Security Event Manager, this tool can also be used to audit network devices and produce IT compliance audit reports. EventLog Manager has a robust service offering but be warned it’s slightly less user-friendly compared to some of the other platforms I’ve mentioned.
How to Choose an IT Auditing and Cybersecurity Solution
We covered a lot of information, but I hope you walk away feeling a little less apprehensive about security audits. When you follow security audit best practices and IT system security audit checklists, audits don’t have to be so scary. These measures keep your finger on the pulse of your entire IT infrastructure and, when used in conjunction with third-party software, help ensure you’re well equipped for any internal or external audit.
While several third-party tools are designed to monitor your infrastructure and consolidate data, my personal favorites are SolarWinds Access Rights Manager and Security Event Manager. These two platforms offer support for hundreds of compliance reports suited to meet the needs of nearly any auditor. Simply select the right report for you and the platform will do the rest. But that’s not all. Outside of building reports, both platforms take threat detection and monitoring to the next level through a comprehensive array of dashboards and alerting systems. That’s the kind of tool you need to ensure successful IT security across your infrastructure.
