When you make a credit card transaction, the last thing you want to think about is your data getting stolen. Fortunately, credit card companies put several measures in place to make sure this doesn’t happen. For businesses dealing with customer payments, PCI DSS compliance measures are a simple and necessary step in making sure customer credit card data is well protected.
Ensuring PCI compliance can be a complex undertaking. In this guide, I’ll review the requirements of PCI DSS, review the best tools on the market to help your organization comply with PCI DSS standards, and discuss why I strongly recommend investing in and using tools to help you set up and manage security and PCI compliance audit processes.
What Is PCI DSS Compliance?
PCI DSS Compliance Checklist
Best PCI Compliance Software
How to Demonstrate PCI DSS Compliance
What Is PCI DSS Compliance?
PCI DSS stands for “Payment Card Industry Data Security Standard.” These policies and protections were set in place by the Payment Card Industry Security Standards Council, which was created by the major credit card companies. Before the council was formed, each credit card company had its own security system. Now, through the PCI Security Standards Council, they work together to ensure security by administering the PCI DSS.
PCI DSS Compliance Checklist
PCI DSS is divided into six “control objectives,” which further break down into twelve requirements for compliance. All merchants need to follow these requirements, no matter their customer or transaction volume: if you deal with cardholder data, you must follow the PCI DSS requirements.

The six control objectives are:
- Secure Network and Systems
- Safety of Cardholder Data
- Vulnerability Management Program
- Access Control
- Monitoring and Testing Practices
- Information Security Policy
You can meet these objectives by setting up certain security, access, and monitoring processes. The following practices are required to meet the PCI DSS compliance control objectives:
-
Secure Network and Systems
Install and maintain a firewall. Firewalls scan all network traffic and block unauthorized access to the system. The purpose of this firewall is to protect cardholder data, so it should be configured to be completely secure and private.
Don’t use vendor-supplied passwords or security. Information supplied by the vendor is widely spread (because it comes with every piece of software) and can be easily discovered. Update your system passwords to a secure version only used in your company.
-
Safety of Cardholder Data
Protect stored cardholder data. This applies only to companies storing customer data; if your company doesn’t automatically store it, you’re already addressing the issue. If you’re a PCI-compliant hosting provider, there should be multiple layers of defense for your stored cardholder data. This includes authorization and authentication methods, as well as restricted access to servers, storage, and networks.
Encrypt transmission. If data is transmitted over open, public networks, you need to use trusted keys and certifications, and never store validation codes or PINs after the data is transferred.
-
Vulnerability Protection
Use malware and virus protection. Install and use antivirus and anti-malware software, and keep it regularly updated. Viruses and malware can enter your systems at numerous points, and if your software needs patching or isn’t functioning correctly, it can miss malicious entries.
Develop secure systems and applications. Ensure your systems are designed with security in mind and keep automatic patching and security scanning systems current. This helps prevent access to secure customer data in the first place.
-
Access Control
Limit user access. The only people who have access to cardholder data should be those who need it to do their jobs. Systems and processes in your business should be designed to limit access only to those for whom the information is strictly necessary.
Identify access. Keep a register of people who have access. Each person should have a unique identification number or code to hold them accountable for their access to cardholder data.
Restrict physical access. Ensure all servers, networks, and data centers are protected with locks, codes, and security measures.
-
Monitoring and Testing Processes
Implement tracking and monitoring. All access to cardholder data and the networks it’s stored on should be regularly and continuously monitored and tracked. Make sure you have event logging mechanisms in place to track user activities as well as to detect and prevent access to data.
Test systems and processes regularly. Vulnerabilities and problems with software can be discovered at any moment, and the sooner you find a vulnerability the better. The longer a problem goes undiscovered, the higher the likelihood for someone to use this to access cardholder data. By testing regularly, you can make sure issues are discovered as soon as they arise.
-
Information Security
Implement a security policy. Clear policies and processes need to be communicated to all staff, personnel, and external contractors who work with your business. It’s important for everyone to understand how sensitive cardholder data is, and how important it is to protect it.
There are no direct penalties or fines if you don’t comply with the PCI DSS, but the credit cards will fine your bank, which will then come after you to pay the fine. Fines can range from $5,000 to $100,000 per month for PCI noncompliance, depending on the severity of the breach.
Best PCI Compliance Software
Here is my list of the best PCI compliance software on the market, many of which offer free trials to help you make your decision. Here’s a look at the top offerings based on critical features of PCI DSS compliance.
-
Security Tracking
For multiple aspects of the PCI compliance checklist above, you need a tool capable of monitoring and tracking security events to protect against security issues. SolarWinds® Security Event Manager (SEM) can help you demonstrate compliance, as it collects an audit trail for all PCI events, and uses real-time event correlations to help you quickly discover security issues or breaches.
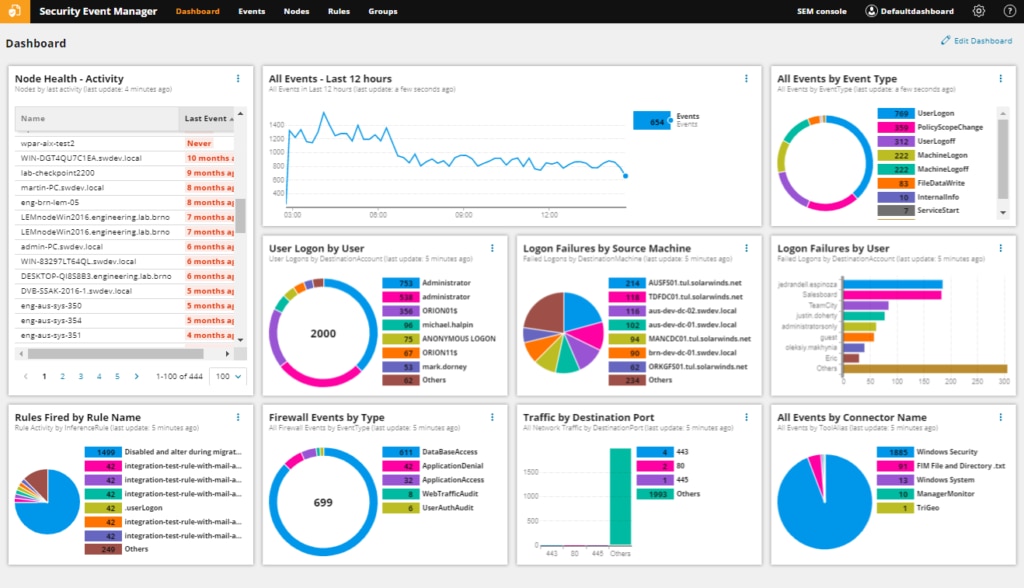
SEM also uses automatic incident responses to block malicious IPs, change user access privileges, disable accounts, block USB devices, and kill applications.
-
Network and System Configurations
Using a tool to configure and monitor your network is also vital for setting up your systems to prevent issues in the first place. SolarWinds Network Configuration Manager (NCM) is one of my favorite tools for managing this process, as it has a wide range of network automation features, freeing you up to focus on other things.
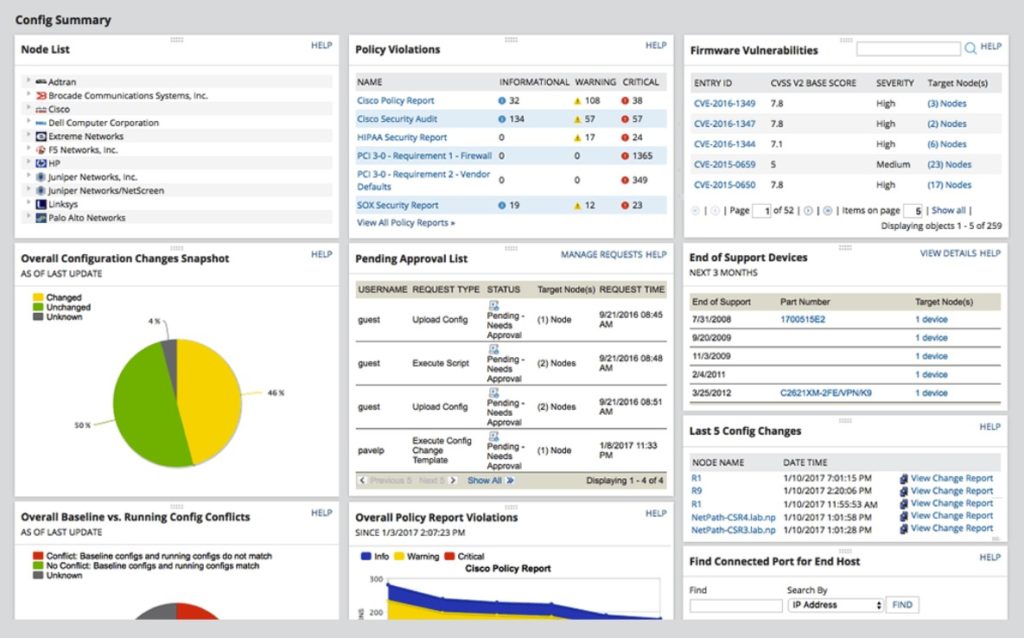
NCM is designed to manage and adapt to rapid changes across complex networks, take over the hassle of repetitive tasks, and maintain standards and service levels for uninterrupted services. It also integrates with the National Vulnerability Database to help ensure your network is protected from issues as they come up. Its network compliance tools allow for standardized configs, detection of out-of-process or unusual changes, the ability to set up audit configurations, and in some cases the correction of violations.
However, network devices are only half of the equation. It’s vital to be able to monitor for configuration changes to servers and applications as well due to their high propensity to cause performance issues, outages, and new vulnerabilities. For this, I turn to SolarWinds Server Configuration Monitor (SCM).
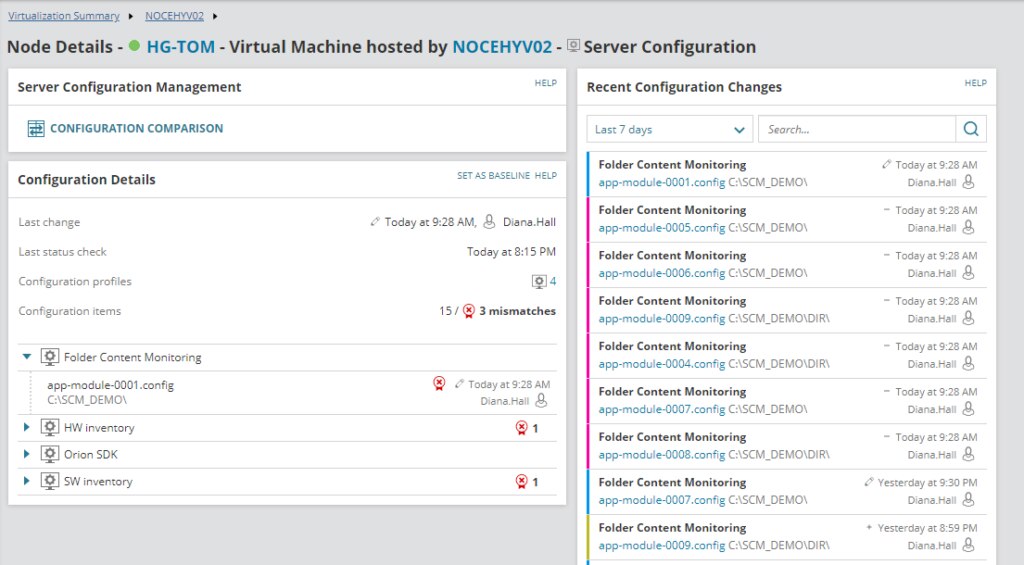
SCM is designed to quickly reveal when server or application configurations change, who’s changing them, how they were changed, and if a change affected performance. This gives you the ability to not only improve security but troubleshoot faster, keep teams accountable, and easily demonstrate compliance.
-
Patches and Updates
Tools like Patch Manager help you keep an eye on whether your software and monitoring processes, as well as all your usual software and applications, are up to date.
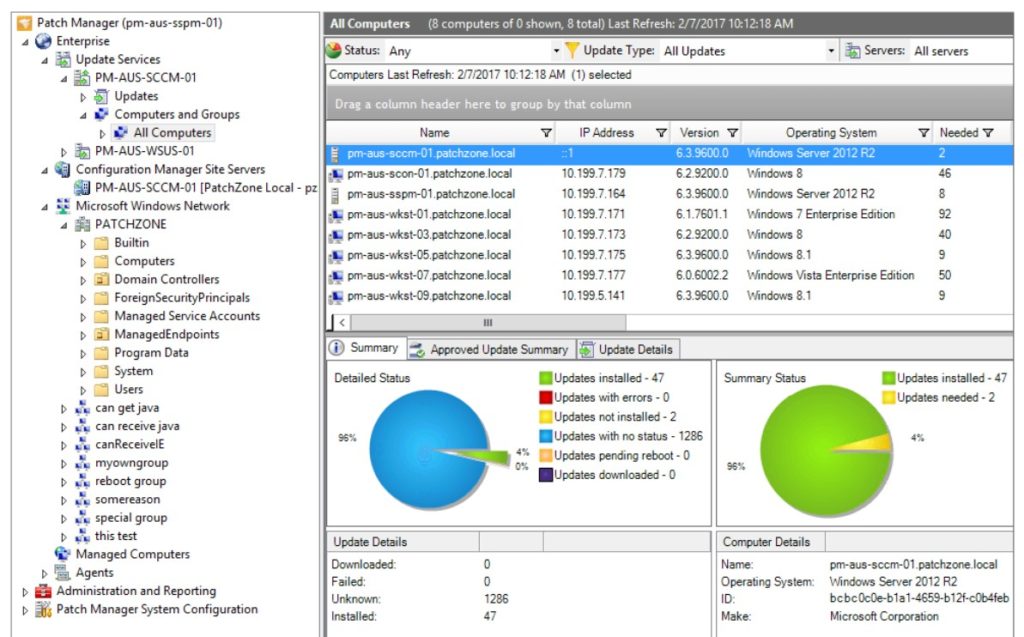
Patch Manager can automate the patching and reporting process, finding vulnerabilities in your common applications and applying patches and updates before security problems become a major issue.
-
Secure Transfers
A secure transfer tool like Serv-U® Managed File Transfer (MFT) Server can help ensure your customer data is protected. This software allows you to make file transfers supported by FTP, FTPS, SFTP, and HTTP/S over IPv4 and IPv6.
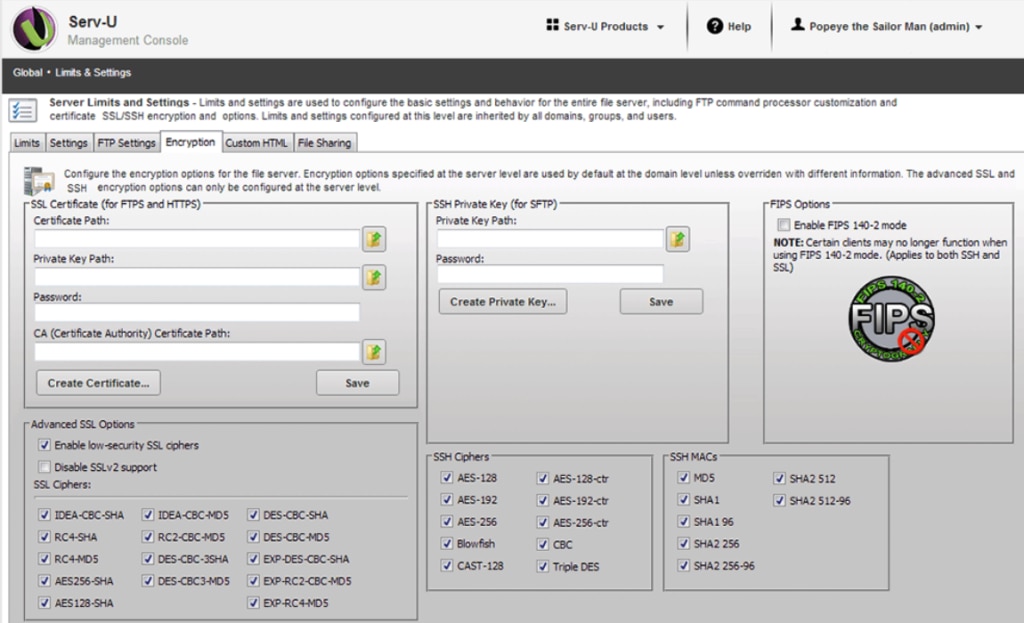
Serv-U MFT can also help you to maintain PCI DSS compliance by ensuring no data is stored in the DMZ after transfer is complete.
-
Access Rights Management
Access Rights Manager (ARM) protects your system by keeping tabs on who has access to what. In addition to giving you the ability to discover insecure accounts or access patterns indicative of malicious activity, it creates audit trails and records of access identities and patterns.
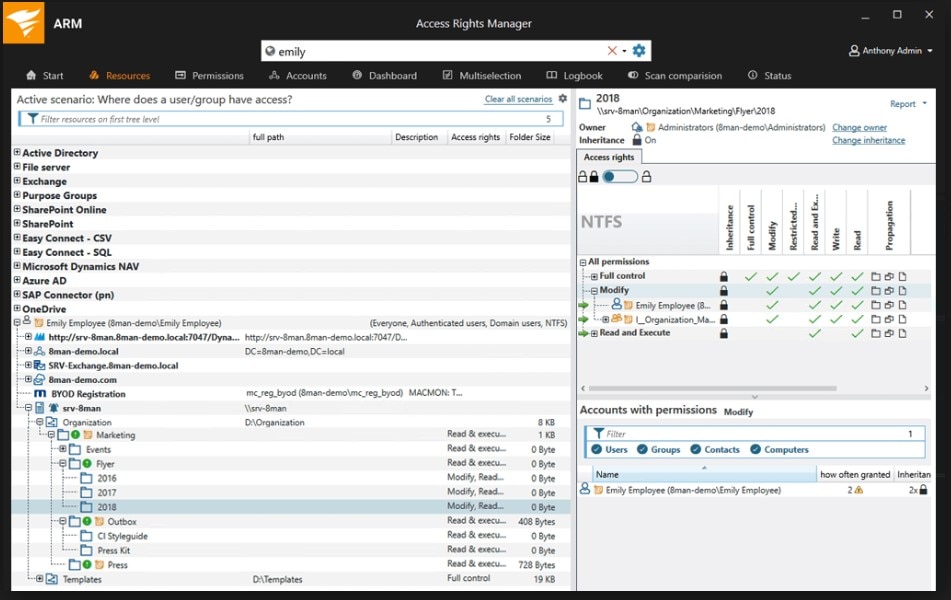
ARM records the time data was accessed, and from where, and minimizes insider threats by controlling access to customer data on a “need-to-know” basis.
-
Complex Network Management
As a managed services provider (MSP), it’s vitally important to provide PCI DSS-compliant services to your clients. For many businesses in different fields (such as finance and e-commerce), this may be mandatory.
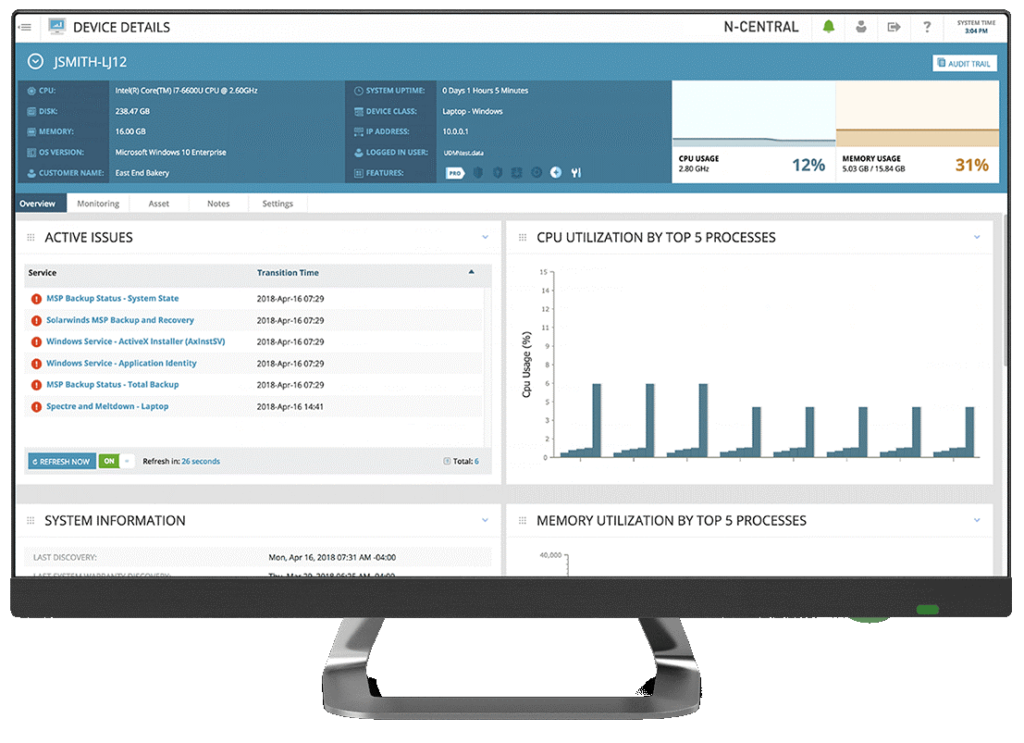
The SolarWinds N-central solution enables you to manage hundreds of client devices and help improve their performance and security. This helps demonstrate PCI DSS compliance—hassle-free.
-
Remote Monitoring and Management
Remotely monitoring client IT systems is challenging enough. Throw compliance into the mix as a vital concern, and you’ll be hard pressed to keep up without some specialized help.
N-able RMM is another tool designed purposefully for MSPs. It provides a full suite of tools for maintaining your clients’ networks, while still making security a top priority.
How to Demonstrate PCI DSS Compliance
The more transactions your business deals with, the higher its level of classification for PCI DSS compliance auditing purposes. However, achieving PCI DSS compliance requires investment in vital, complex processes to make sure every part of your system is configured and functioning correctly.
All businesses need to have tools and systems in place to ensure they meet the PCI security and auditing requirements. I recommend starting with a comprehensive solution like Security Event Manager to help your organization comply with the above PCI DSS checklist and be well on your way to demonstrating compliance.
