A successful SIEM strategy is an investment—and sometimes costly. Managing SIEM is a resource-intensive process, requiring ongoing evaluations and adjustments to establish and maintain optimal performance. Despite this, going without a SIEM solution isn’t the answer, because this can leave you vulnerable to attack.
Open-source SIEM and free SIEM tools can seem like the solution. Open-source SIEM tools are available for the public to modify and the best tools enjoy a community of loyal supporters. IT experts across the globe share their knowledge and experience to tweak open-source SIEM code, meaning the tool itself is constantly evolving. For admins who have the time and resources to maintain and adjust open-source tools, this customizability and flexibility could be useful.
To help you decide between the countless free and open-source SIEM tools on the market, I’ve put together a list of my favorite open-source SIEM and free SIEM software. I’ve also included in this list a couple of paid tools that offer free trials. Free tools simply aren’t capable of offering a full, enterprise-level SIEM solution. In contrast, SolarWinds® Security and Event Manager (SEM) offers a 30-day free trial and is the most suitable SIEM tool for business use, in my opinion. Before giving you my product list, I’ll first go through a quick rundown of the main features and functionalities of SIEM.

Feel free to jump ahead to chosen product review:
What to Know About Free and Open-Source SIEM Solutions
The problem with open-source tools is they can be hit and miss. These programs usually have a small budget behind their creation, so they tend to be less user-friendly and sophisticated than their paid counterparts. They do tend to require more effort and time to maintain. Open-source SIEM tools tend to be too labor-intensive for full-fledged IT departments, so most inevitably migrate to enterprise-grade tools. What’s more, open-source tools don’t come with customer service—you can’t pick up the phone and get answers to your questions.
SolarWinds Security Event Manager
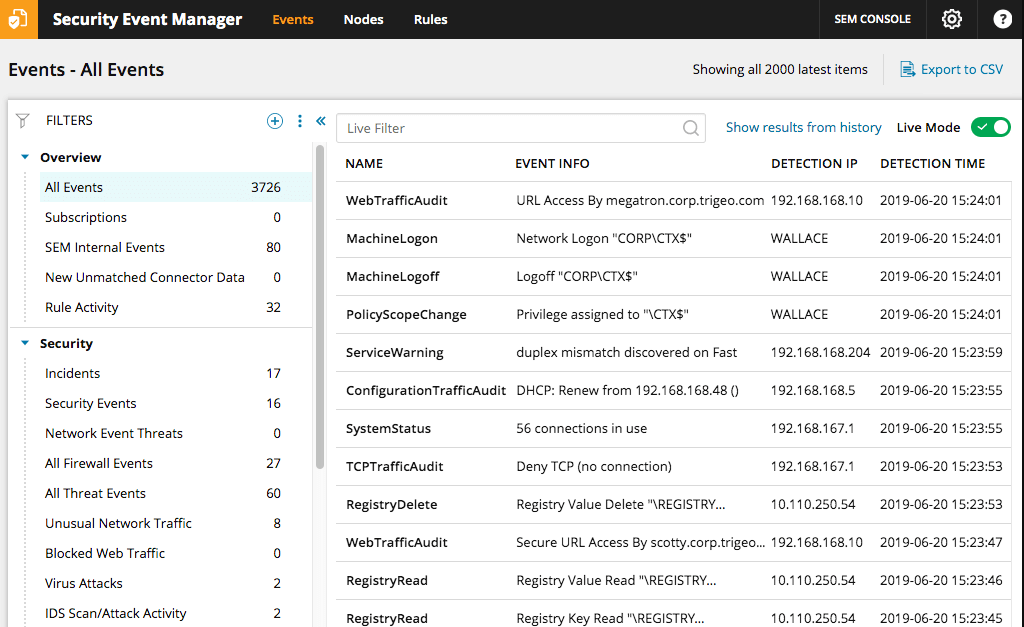
SolarWinds Security Event Manager (SEM), though neither free nor open-source, does offer a 30-day free trial and it has been included in this list because it’s the obvious choice for enterprise-level requirements. This tool covers the above-mentioned features and functionalities and it has dynamic data visualization, with a range of graphs and charts available. The dashboard itself is visually appealing, as it is clean, colorful, and easy to navigate. This SIEM tool is also great for compliance and supports HIPAA, SOX, PCI DSS, and much more.
SEM is full of useful features, which are proof of how much consideration was given to its design and user friendliness. For example, it comes with out-of-the-box functionality, which means getting started is super easy because you don’t have to spend time messing with the settings. This is particularly useful for those of you who aren’t convinced by a paid tool yet, but who want to go for the 30-day free trial. You can rest assured you won’t lose any money and little time in the process.
SEM is a highly automated solution. It automatically blocks hundreds of threat types, has a built-in alerts system keeping you informed of threats on a constant basis, and features advanced search utilities to make navigating your logs much faster. This program works on a 24/7 basis, so there aren’t any cracks for suspicious events to slip through. It responds in real time, features audit-proven reports, and features virtual appliance deployment.
Another reason I’ve given SEM priority in this particular list of products is because it’s so cost-effective. The pricing model is based on the number of log-emitting sources, rather than log volume, which contributes to this SIEM tool offering fantastic value for money. If you need a cost-effective, sophisticated, and easy-to-use enterprise-grade solution, then give SEM’s free trial a go.
Top Free SIEM Software
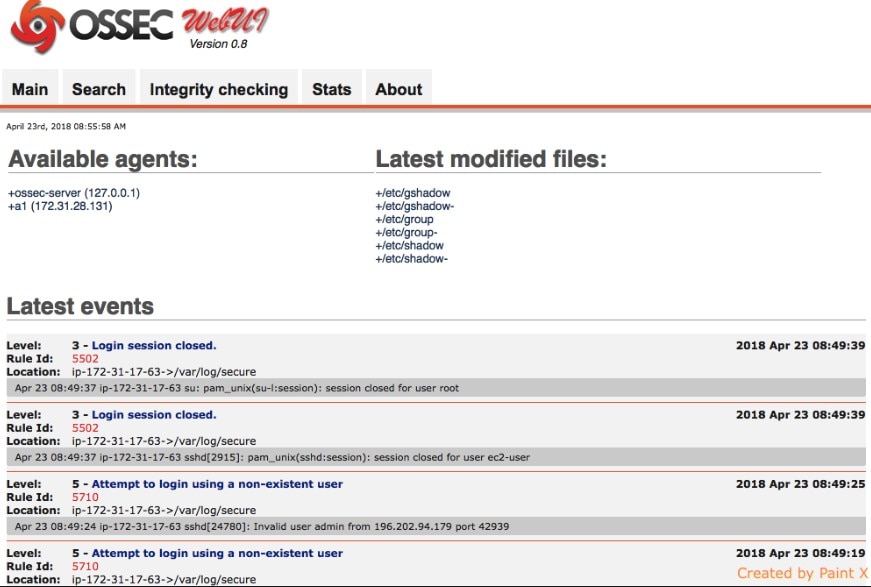
OSSIM, by AlienVault, is one of the most popular open-source SIEM tools available. This is a highly feature-rich program with event collection, normalization, and correlation utilities. It boasts short-term logging and monitoring capabilities, as well as long-term threat assessment and built-in automated responses, data analysis, and data archiving.
There are many reasons to choose OSSIM, including invaluable tools like asset discovery and behavioral monitoring. You can contribute and receive real-time info about potentially malicious hosts, helping to make security a priority. The pitfall of this free SIEM tool is it can be a bit inflexible. The setup is labor intensive, particularly for Windows, and customizing the program to your needs requires a hefty time investment.
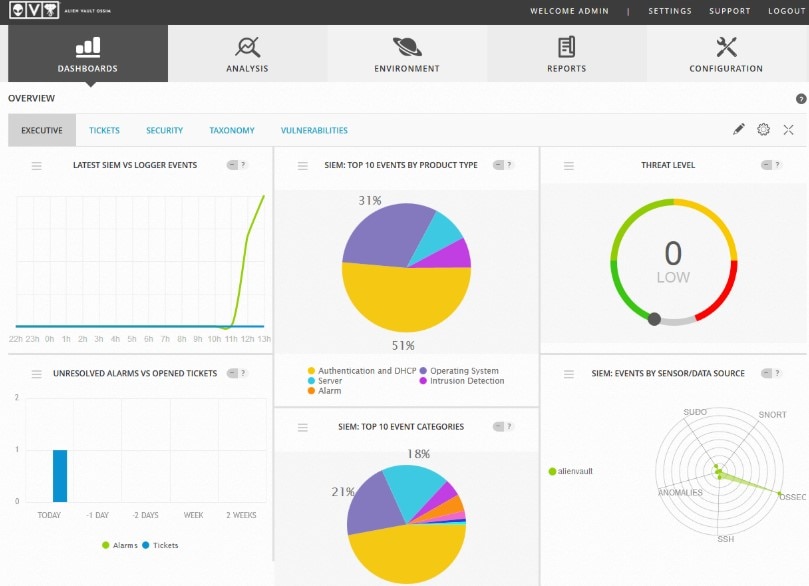
Of the free SIEM software available, OSSEC is a strong choice. This program is known as an open-source intrusion detection solution and is popular among macOS, Linux, BSD, and Solaris users. The best thing about this program is it features both server-agent and serverless modes. Its log analysis utilities are proficient, covering numerous sources including mail servers, FTP, and databases.
If you want to monitor multiple networks from a single point, then OSSEC is a viable option. The community behind OSSEC is supportive and well structured. You can join the mailing list or even join the Slack channel, which makes collaborating with other users easier. The only issue is software updates can be a bit disruptive with this tool.
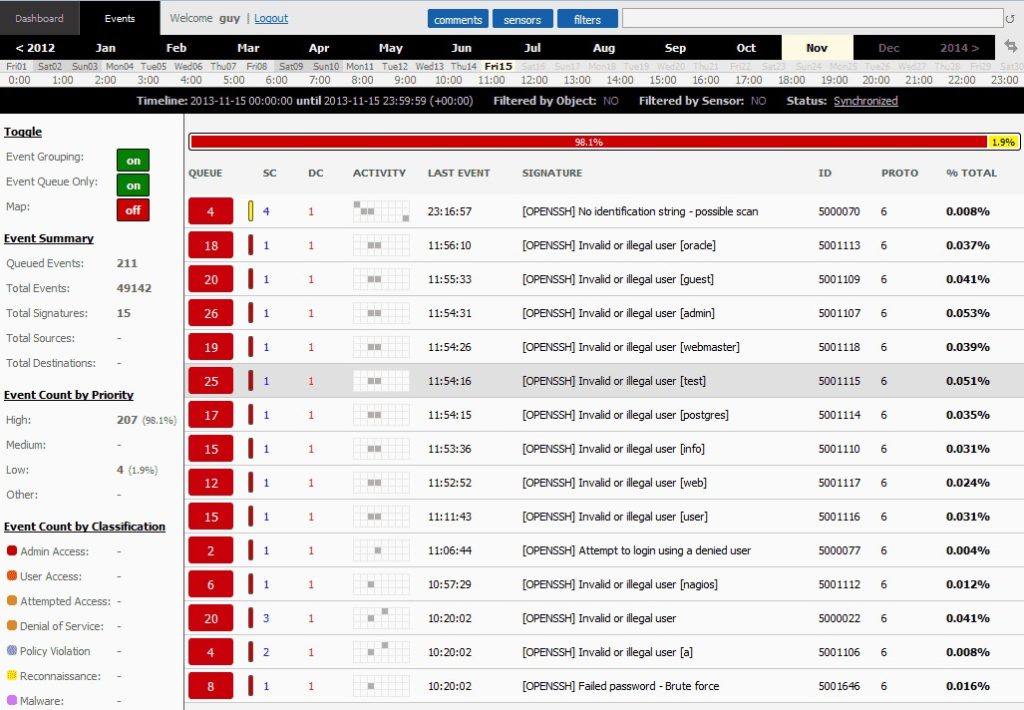
Sagan is a free SIEM tool featuring real-time log analysis and correlation. It’s also useful for log normalization, script execution on event detection, real-time alerting, multi-line log support, and automatic firewall monitoring. This is a lightweight tool with multi-threaded architecture, which allows it to utilize all CPUs/cores for log processing in real time. It’s compatible with several graphic security consoles like BASE, Snorby, and EveBox. The main disadvantage of Sagan is it isn’t especially user friendly.
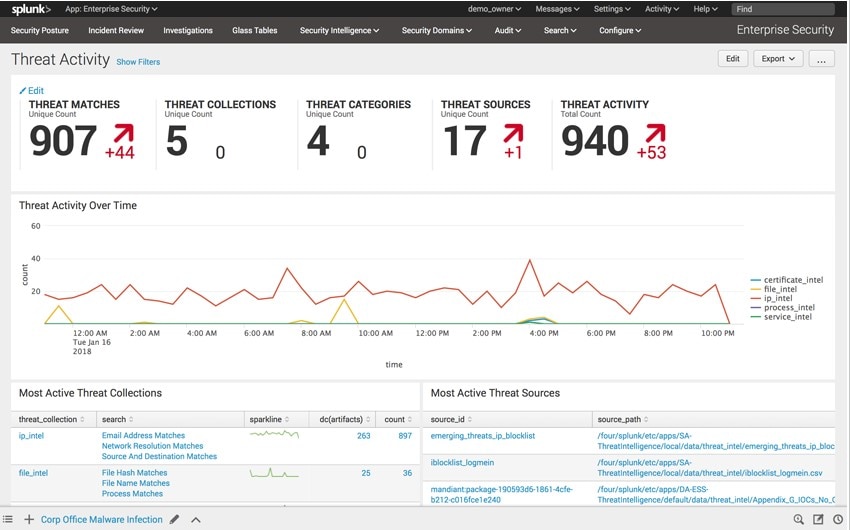
Splunk Free, as its name suggests, is the free version of Splunk. This free SIEM software allows you to index up to 500 MB every day and it won’t expire. This limit refers to the amount of new data you can add. The benefit of this system is you can continue adding 500 MB per day, forever, meaning you could eventually have multiple terabytes of data. If you need to upload more than 500 MB a day, however, you’ll need the Enterprise version. Splunk Enterprise gives you real-time visibility, letting you automate the collection, indexing, and alerting of data. It features AI and machine learning, meaning your solution becomes more intelligent with every passing day. Splunk Enterprise is a comprehensive SIEM program. Though Splunk Free shares many of its features, it’s limited in many ways, so it isn’t a viable long-term solution. It doesn’t feature alerting or indexer clustering, for example, among other Enterprise utilities.
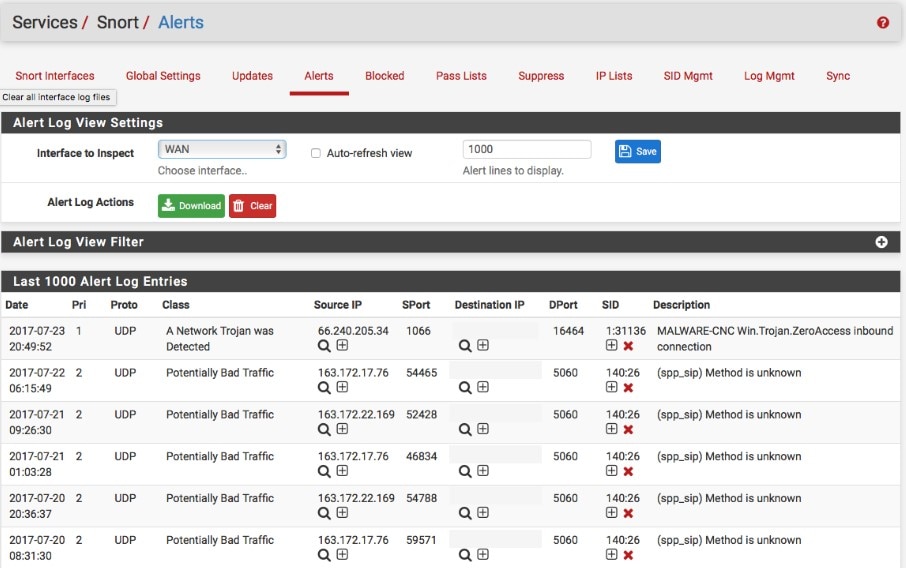
This free open-source intrusion detection solution offers some surprisingly sophisticated features. It can analyze network traffic in real time, provides log analysis utilities, and displays traffic or dump streams of packets to log files. Though the installation process isn’t especially intuitive and can be a bit confusing, the tool itself is well supported by online Snort resources. Official documentation includes a Snort user manual, Snort FAQ file, and guides on how to find and use your Oinkcode. Despite these helpful resources, this tool is probably only suitable for experienced IT professionals. Bear in mind, Snort doesn’t offer a full SIEM solution.
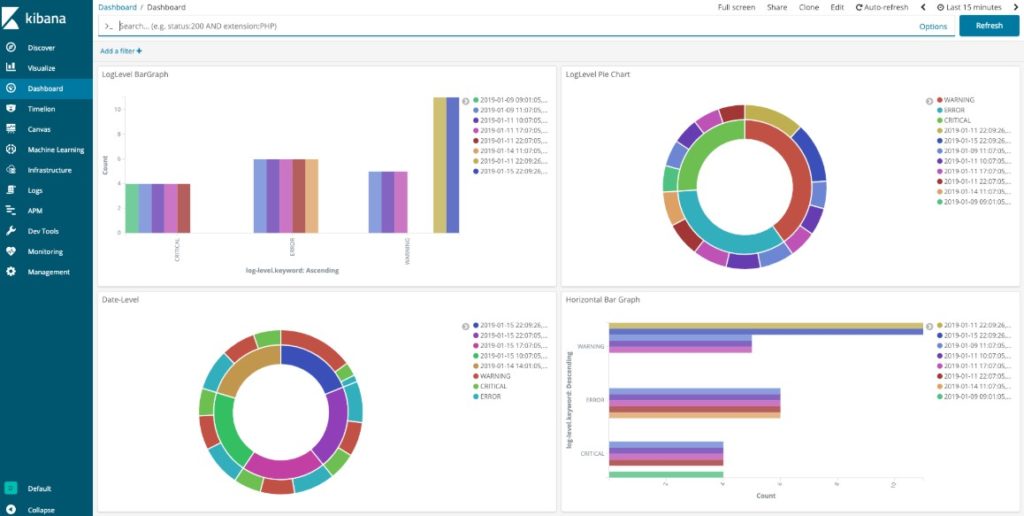
Elasticsearch is essentially a powerful search and analytics engine. It stores your data centrally, letting you query it by combining search types (geo, metric, structured, unstructured) in any way you want. This tool is fantastic for zooming in and out of large volumes of log lines, so you can see the big picture and the details. Unfortunately, this tool isn’t great for correlation and doesn’t supply any out-of-the-box alert functionalities.
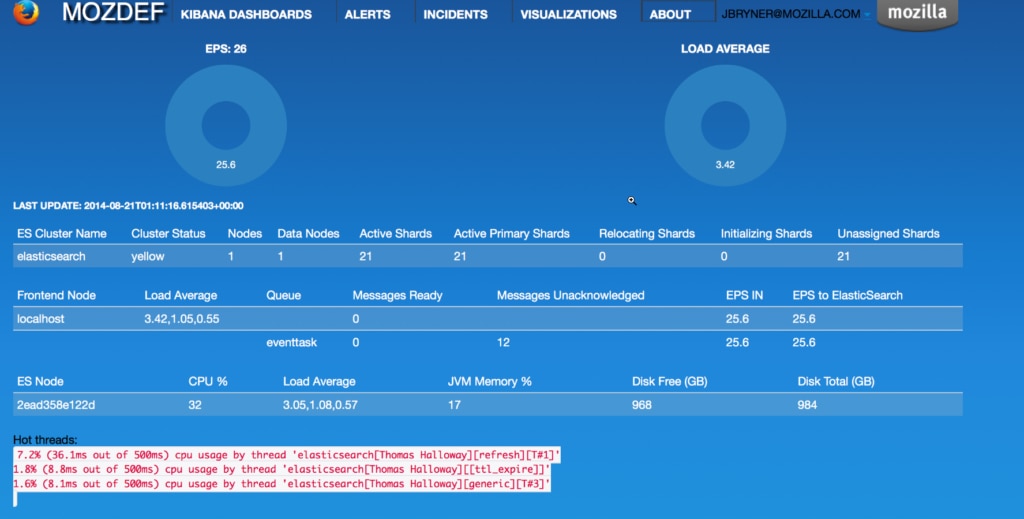
I’ve included MozDef in this list because it’s a super scalable and resilient tool. It’s an open-source solution using a microservices-based architecture. It can be integrated with numerous third parties, boasts event correlation and security alerts to keep you informed. MozDef was produced by Mozilla and it’s without a doubt a powerful tool, but setting it up and learning how to use it is a time investment for most.
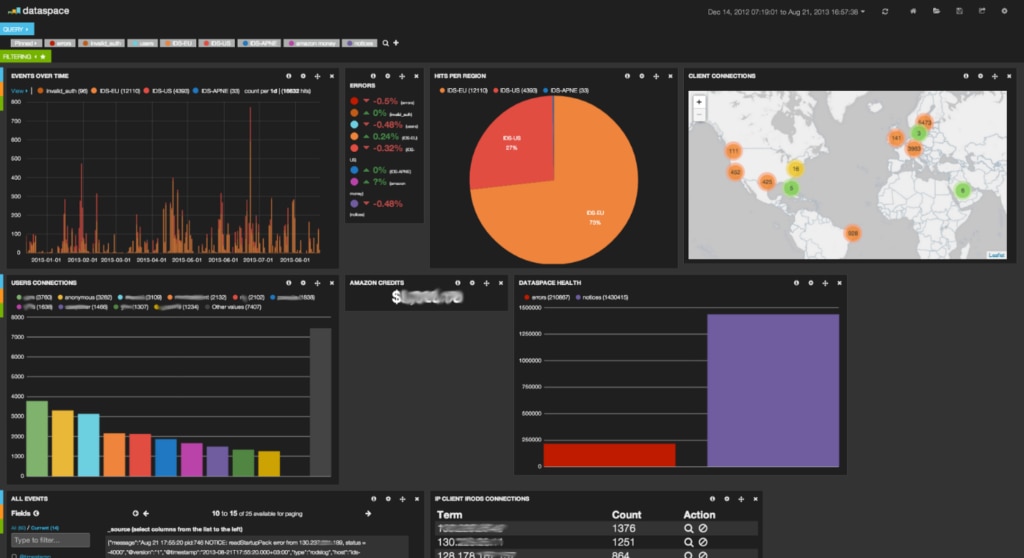
Elastic Stack, also known as ELK, is comprised of several free SIEM tools. Elasticsearch, which has already been mentioned in this guide, is the distributed, JSON-based search and analytics engine. Kibana, another tool included in the stack, is a window into the Elastic Stack. Beats is the platform responsible for lightweight shippers sending data from edge machines, while Logstash is the data collection pipeline. In combination, these tools offers a more comprehensive SIEM solution than Elasticsearch alone. Although this suite of tools is impressive, Elasticsearch is at the heart of the suite and offers the most notable of the stack’s utilities.
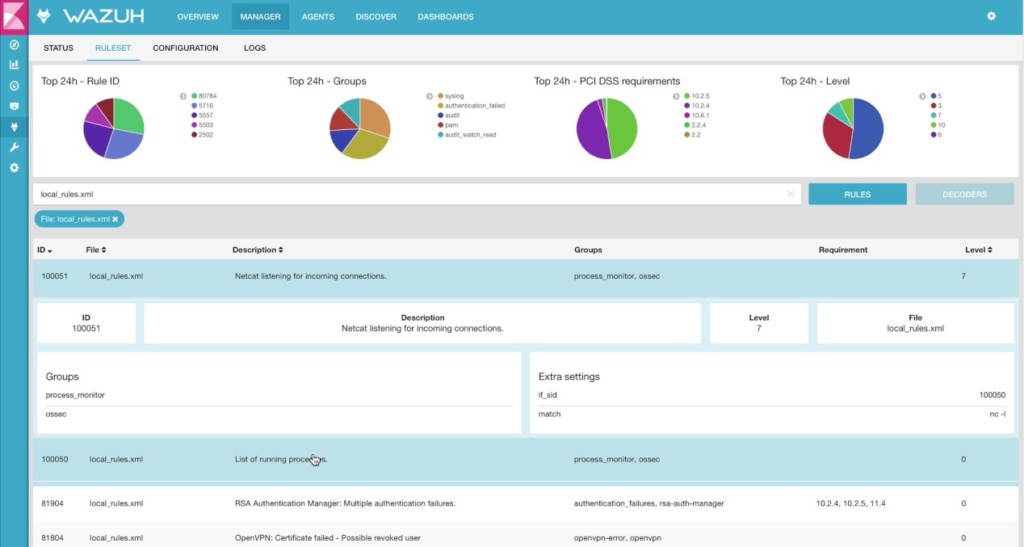
Wazuh is a free SIEM software prioritizing threat detection, incident response, integrity monitoring, and compliance. A cloud-based version is available, which is a big advantage, although this isn’t free. With cloud security, containers security, log data analysis, intrusion detection, security analytics, vulnerability detection, and configuration assessments, this is a versatile tool. It’s not, however, as powerful as some alternatives.
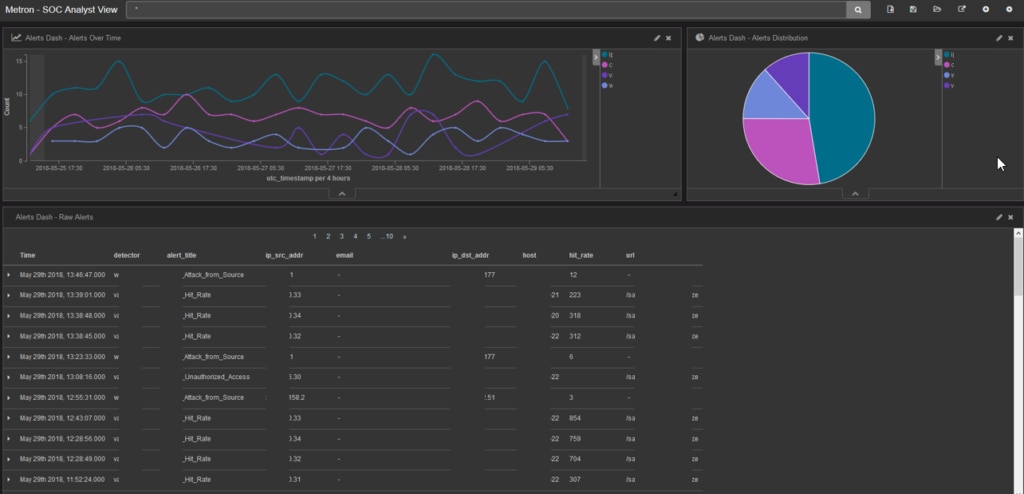
Lastly, we have Apache Metron, an open-source SIEM tool combining multiple open-source solutions into one centralized console. Apache Metron has six main components: SOC analyst, SOC investigator, SOC manager, forensic investigator, security platform engineer, and security data scientist. The platform itself is highly visual and dynamic, but the interface could be more intuitive.
SIEM Features and Functionality
SIEM, otherwise known as Security Information and Event Management, is a fundamental element of successful cybersecurity. SIEM software provides you with the utilities required for effective log management, intrusion detection, event correlation, threat intelligence gathering, incident management, compliance standard fulfillment, and vulnerability assessment processes.
Of course, different SIEM tools will prioritize certain features and functionalities. It’s important you understand SIEM basics before choosing the tool you’d like to deploy. Whether you decide to go for a free, paid, or open-source SIEM program, you should always look out for the following features:
- Intrusion Detection: An effective intrusion detection approach is of critical importance. Your tool should be able to differentiate between innocuous failed login attempts and intensive, system-wide attempts symptomatic of an attack. Near-real-time data analysis is key.
- Automated Notifications and Alerts: SIEM solutions should alert you when an unusual or concerning event occurs.
- Event Logging: Event logging assists in detecting real-time unusual activity, and allows you to thoroughly investigate any issues.
- AI/Intelligent Detection of Threats: A successful SIEM solution should be able to predict potential threats, which requires information on the latest threats to be compared against archival data and current threats.
- Data Storage and Filtering: Data should be stored in an archive, so it can be referred to when necessary, informing future threat detection and resolution. This data should be searchable and should allow you to filter through it, so you can target certain info easily and quickly.
- Visualization: Data visualization can be extremely helpful for data interpretation. Graphs, dials, and color coding can give you an awareness of what is happening within your system with little more than a glance.
- Compliance: It’s always useful to have SIEM software to helps ensure regulatory compliance.
- Compatibility: SIEM software should be compatible with your existing network, so it can afford you a comprehensive view of your events.
Getting Started With SIEM Tools
Hopefully this list of open-source SIEM tools and free SIEM software has given you some idea of which program is best suited to your needs. I have to say while OSSIM comes out on top as the best open-source tool, if you’re looking for an enterprise-grade solution then none of these free and open-source programs can really cut it. A cost-effective, powerful, and flexible enterprise-grade solution is offered by SolarWinds SEM, and I couldn’t recommend it more highly. Ultimately, the sophistication of this program pays for itself.
