In any enterprise there are a large number of users, including employees, managers, and clients. All these users need to have appropriate access to resources on the network, so they can do their jobs effectively and not be held back by needing to request access each time they need something. On the flipside, enterprises need to take care to protect private or personal data, sensitive resources, and vital security information—both from internal threats and from cyberhackers.
This process should be managed by appropriate user provisioning, which for accuracy and efficiency requires an automatic user provisioning tool. This can streamline your user provisioning tasks and reduce security risks, help you to meet compliance obligations, and simply reduce the time you need to spend managing user accounts and permissions. This article will cover the question “What is user access provisioning?” so you can build a fuller understanding of how it works, why it’s so important, and how to manage it in an effective way reducing overheads for administrators.
What Is User Provisioning and Deprovisioning?
Why Is User Provisioning Important?
Best User Provisioning Software
Key Takeaways about User Provisioning
What Is User Provisioning and Deprovisioning?
User provisioning is the process of allocating privileges and permissions to users, so as to protect security in the enterprise, while allowing users access to everything they need to do their jobs. This is also called user account provisioning. Deprovisioning is the act of removing privileges or access from an account or deleting an account.
The process of user management and account provisioning involves creating user accounts, giving permissions, and changing accounts or privileges as necessary, disabling accounts, and deleting accounts.
There are four main kinds of user provisioning:
- Self-service account provisioning: This is when users are permitted to participate in some parts of the provisioning process, so the administrator doesn’t have to do everything. For example, one aspect of this might be the user’s ability to change and manage their own passwords.
- Discretionary account provisioning: Discretionary account provisioning is when the administrator alone decides which applications or files a user may have access to. This is common in smaller companies but becomes unwieldy in large enterprises if handled manually.
- Workflow-based account provisioning: This is a process in which required approvals (such as from the Chief Technology Officer or Chief Finance Officer) are gathered before permission is granted for access to files or applications. Access is based on workflow needs and requirements.
- Automated account provisioning: A centralized application or software manages every account and rules can be created to set up each account in a particular way. This can streamline the process for new users and allows the administrator to more easily keep track of who has access to what. Administrators will still need to engage in some of the other kinds of provisioning, but their workloads in those respects are much reduced.
There are also five common situations in which you need to provision new user accounts or change privileges include:
- A new employee: When someone new starts, they’ll need a user account set up with appropriate permissions, so they can perform their required tasks. They’ll also need an email account, access to files, and membership of various relevant groups.
- Promotion: If someone is promoted or moves into a different role, their permissions and access rights might change. These will need to be updated smoothly and quickly, so the employee can begin performing their new role as soon as they move into it.
- An employee leaving: When an employee leaves the organization, all their accounts and access should be immediately removed, for security reasons. Having former employees with access to the system is a big security risk.
- One-off access: There are some situations in which someone or a team might need one-off access to particular files or directories or may need temporary emails and access set up for a contractor. One-off user access provisioning should be handled quickly and have clear processes for removing access when the one-off event is finished.
- Support or problems: In some cases, new users will need to be provisioned or changed if an employee forgets a password or has a problem with their account. In these cases, any old accounts should be promptly removed. In general, unused accounts should be deleted.
Access rights are important for managing security and compliance issues and can also make a big difference in how efficiently employees can work. I’ll go into more detail below on the importance of user provisioning and deprovisioning.
For Windows systems, most enterprises will be working with Active Directory to provision user accounts and allocate access rights, including setting up the accounts of administrators. Manually provisioning and deprovisioning user accounts with Active Directory can be manageable for smaller businesses, but for large enterprises it quickly becomes a huge burden. Setting up access rights for each account or each group takes a long time, and administrators are more likely to make mistakes or get confused when they’re dealing with a large number of accounts in the user access management process.
Why Is User Provisioning Important?
Appropriate user provisioning and deprovisioning is important for several reasons, including work efficiency and organization productivity, security, and compliance and auditing purposes. As organizations grow, proper user account provisioning processes become even more important. The large volume of users alone can make it hard to keep track of who has access to what, who needs access and why, and users needing to be removed. Having a well-planned user provisioning approach can ensure the problem doesn’t become unmanageable.
Work Efficiency
In many cases, enterprises without effective user account provisioning tools in place may be losing valuable productivity by spending work time fixing permissions problems. Imagine the scenario where an entire team is working on a major project but finds at the last minute they don’t have access to important applications or files they need to complete their work. This would become an urgent priority for the enterprise admin, and without a tool to help, this could take time to set up a new access group and allocate each person in the group the required permissions. Meanwhile, the team is unable to continue their work, other issues are piling up for the admin, and productivity is reduced. In some cases, you can set up users to use single sign-on, which can allow them to sign on to many applications with one set of credentials. By having a well-formulated user-provisioning plan, clear protocols, and efficient and user-friendly provisioning software, these hiccups can be avoided.
Security
The next important issue is security. The focus of security in user access management and user provisioning is two-fold, as security issues, in this case, can come from both outside and inside the organization.
Regarding outside threats, if users have excess permissions, this can leave your entire system vulnerable. If an intruder accessed your system, they would only need to do so through one compromised account with a lot of permissions and access, such as an administrator account. Intruders are constantly searching for weak points in organizations, and over-zealous user permissions can be a major weak point. That’s why it’s important to follow the principle of least privilege, where permissions are set as tightly as possible for each user while still allowing business function.
In terms of inside threats, there are two main issues: malicious intruders and accidental changes. In some cases, when users accidentally have privileges for files or applications they shouldn’t have, they can mistakenly change settings, move files, or delete data. This can cause major security issues entirely by accident. Ensuring users only have access to parts of the system they need to do their jobs can prevent this from occurring. In addition, it’s also important to protect from the unlikely event an employee is maliciously seeking out sensitive information or access to important files. Using good automated user provisioning processes and permission allocation can prevent users from accessing sensitive files or confidential information.
Auditing and Compliance
Finally, the issue of auditing and compliance also ties into the problem of security when provisioning new user accounts. If your enterprise deals with sensitive information, such as financial or health data, there are compliance measures needing to be followed, including appropriate access to the data. For example, HIPAA privacy requires individually identifiable health information to be highly protected. Allowing many users access to this kind of information would not be in compliance with HIPAA, and could result in major penalties if an audit is performed and this breach is discovered.
These kinds of rules also apply to financial information, confidential business information, and confidential government data. If your enterprise deals with any of these kinds of sensitive data, your user provisioning processes and access management policies are critical.
In most enterprises, automated provisioning is used to make this process simpler, more accurate, and more efficient. When you use an automated user provisioning system, you can make changes occur more quickly, so users won’t need to wait for new privileges to be set up. Efficient provisioning reduces costs and overheads, as IT and administration resources can be used more effectively elsewhere. In addition, automated systems increase security, as they can keep track of accounts out of use, automatically de-provision accounts, and quickly switch or remove permissions as necessary.
Best User Provisioning Software
There are several automated user provisioning tools on the market, and whichever one you choose should match the following criteria. There are also several best practices you should follow when it comes to using provisioning software and access rights management.
First, whatever solution you choose should be comprehensive with respect to its features, should have a good user experience, should be able to work quickly and automatically, and should reduce overheads instead of increasing them. User account management software should be able to automatically provision and deactivate accounts, allow self-service or delegated access requests, and should include the ability to report on user permissions and high-risk accounts while keeping a record of data access.
Next, ensure you have taken a thorough inventory of all your most important and most sensitive applications, directories, and users. It can be hard to allocate the appropriate security risks or permissions if you don’t know which parts of your organization should have limited access or which may be subject to compliance requirements.
Once you begin to implement your user provisioning process, ensure you have clear benchmarks for determining whether it’s effective. For example, measure how much time each week your administrator spends on user provisioning and deprovisioning and then compare this to how much time they spend with a tool. Be clear on the scope of your user provisioning process, including which working groups and teams are included, and start with one or two teams if necessary when you’re testing out new software.
Once you’ve gone through the testing process and you’re happy with your solution, you can roll it out across your entire organization and see whether it’s scaling well. You should then put a monitoring program in place to look at how many user provisioning requests are being made, how many need to be handled manually, what internal audit findings say about security and compliance, and whether end users are satisfied.
One of my favorite tools for account management and user provisioning is SolarWinds® Access Rights Manager (ARM). ARM has several key features making it highly capable of fulfilling user provisioning needs for small- to medium-sized businesses, and large enterprises.
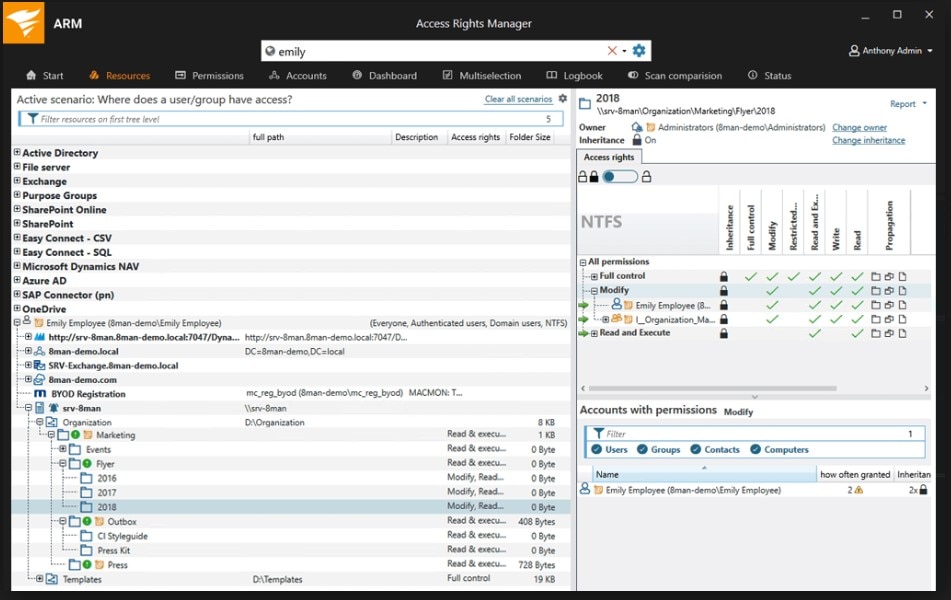
First, ARM monitors and manages Active Directory and Group Policy, so you can be sure your user provisioning practices are secure and nobody has access where they shouldn’t. With SolarWinds ARM, you can see if any user has made changes and when those changes occurred. This can help you to meet compliance obligations by showing all users have appropriate access and no unauthorized changes have been made. ARM also links with SharePoint to show who has authorized access to SharePoint resources.
About provisioning, ARM can set up new accounts quickly and can do so on an individual basis or in a more general way with standardized templates. To reduce administrator overheads, you can also use ARM to set up access rights to be granted by the data owner, rather than the administrator having to do everything. It can then look at how you have provisioned your accounts and what access has been given to determine which accounts are high risk and should be monitored closely.
For audit and compliance purposes, ARM can produce audit-ready reports, so you can show you’re complying with regulations as appropriate.
You can try out a free trial of ARM for 30 days, or request a demo on the SolarWinds website.
What if you’re a managed services provider (MSP), and you need help provisioning hundreds of client devices and/or networks? For these users, and anyone having to worry about multiple endpoints, ARM might not be the best fit.
That’s where N-able Passportal comes in. It’s tailored for the needs of MSPs and comes with time-saving features and a high degree of customization.
With Passportal, you can store, manage, and retrieve passwords as needed. You’ll also be able to configure and control documentation and access rights. Passportal can be a vital addition to your arsenal of tools for managing user provisioning.
Key Takeaways about User Provisioning
User provisioning is the process of setting up user accounts with appropriate permissions, putting them in the right groups, and ensuring they have the right tools at their disposal to complete their jobs. To do this properly you need to be aware of when to provision new accounts and when you should be removing permissions from accounts, while ideally using a tool or software to help you automate parts of this process. Taking a proactive approach to user management and access control ensures you don’t make any compliance blunders and don’t overly expose your business to the risk of data breaches or loss.
Finding a high-quality user provisioning and user access management tool can help you streamline this process and ensure security and compliance issues are reduced as much as possible. SolarWinds ARM is my top pick for going through this process, as it provides high-quality tools and broad features for managing access rights, protecting from internal and external security threats, and is easy to use.
