Access management, sometimes referred to as identity and access management, is the umbrella term for the processes involved in certifying your team members have appropriate access to IT resources. This includes preventing unauthorized personnel from accessing certain resources and information. Access rights management is of critical importance to the security, efficiency, and regulatory compliance of your organization, which is why employing robust and dependable access review tools is so crucial.
This guide provides an overview of the basics of access management, followed by my list of the best access review tools available today. If you don’t have time to read the guide in its entirety, here’s my top recommendation: SolarWinds® Access Rights Manager. This tool combines range of functionality with sophistication and ease of use. In other words, it hits the user experience sweet spot, giving you everything you could possibly need without hassle or complication.
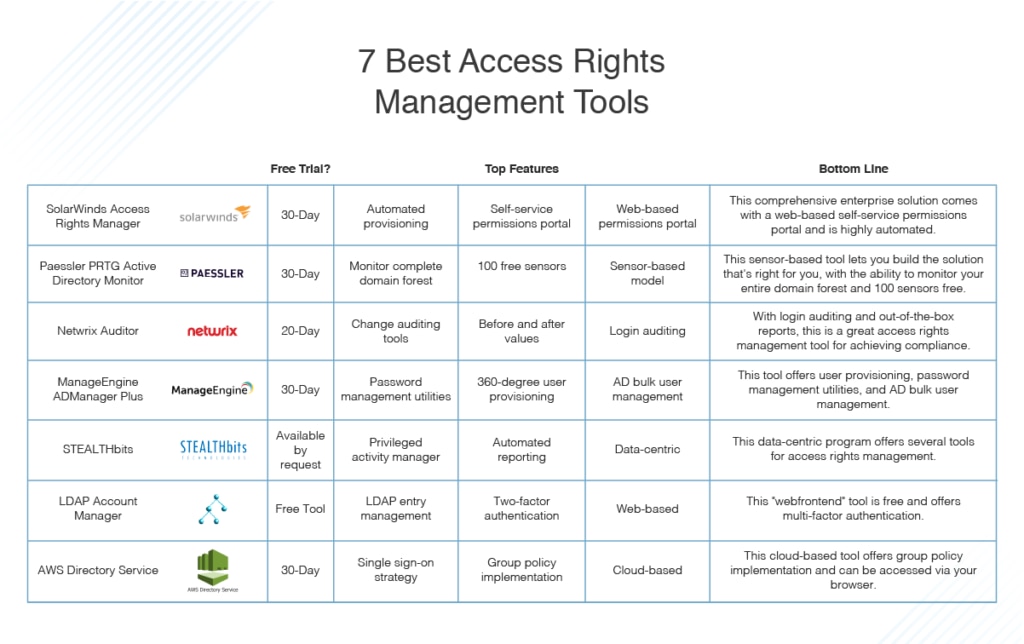
Best Access Rights Management Tools Manager
Here’s my list of the best access rights management tools available. When considering which is right for you, consider which utilities are a priority for your organization. Do you value simplicity over range of functionality? Are you looking for a basic, free tool suitable to minimal requirements? Or do you want a solution geared toward business use, that’s scalable and powerful? There’s something for everyone on this list, so hopefully you’ll come away with a good idea of which access user access control software is best for your business.
SolarWinds is a well-known name among network administrators. This company has a reputation for creating some of the best network monitoring and management tools on the market. SolarWinds stands out from its competitors because it somehow manages to achieve both the optimal quantity and the optimal quality in its products. In other words, SolarWinds tools offer a range of functionalities, without compromising on the sophistication of their technology.
You’d expect the flaw in this offering to be its delivery, but this is where SolarWinds really shines, boasting intelligent and intuitive user interfaces that are easy to use and dynamic. SolarWinds also offers some extremely generous free tools, including a free subnet calculator and TFTP server and a tool to analyze permissions in Active Directory (more on that below).
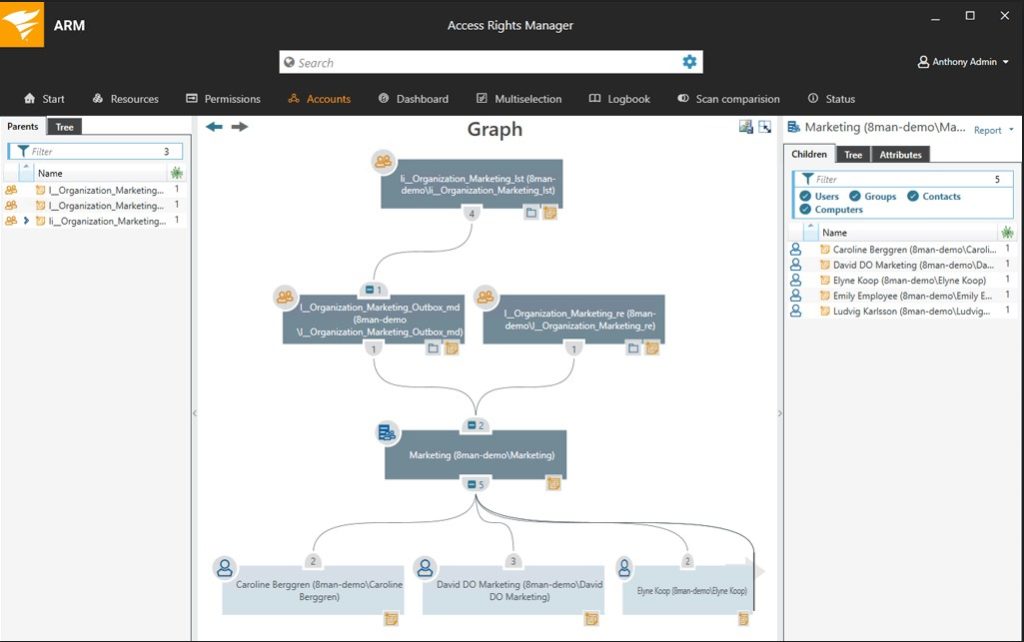
Access Rights Manager (ARM) is no exception to the SolarWinds reputation. This software provides an effortless solution through the lens of a highly intuitive user interface, and it can’t be beat as an enterprise solution. It’s only available for the Windows Server environment, but it can access AD directories for a range of services, including NTFS and Microsoft Exchange Server.
If you’re looking for enterprise access management capability, the ARM solution prioritizes the most critical elements of user access, while providing detailed reports. The program has been designed to simplify the experience of managing access rights, letting you examine and respond to security incidents rapidly and giving you the ability to address insecure account configurations in a proactive way. This tool takes the stress out of management by providing automated account provisioning, and even deprovisioning, so meeting SLAs feels easy and you can keep user credentials secure simultaneously.
ARM even comes with a self-service permissions portal, for enabling delegation to data owners in a secure way, saving you time, effort, and resources by enforcing efficient security and eradicating overhead. This user access control software includes alert features, which sends you instant notifications if anything unusual happens—for example, unauthorized activity or a misconfigured account. By maximizing visibility in this way, it lets you investigate any potential privilege abuses and validate enforcement of security policy. The self-service permissions portal, which is web-based and can be accessed from any device, allows for secure delegation of rights management to the data owner, facilitating improved accountability.
Access Rights Manager automates processes wherever possible, which means minimal manual intervention is required. User account creation, modification, and deletion are all automated by role-specific templates. The program also provides audit trails of all access level alterations and account activity, making compliance audits much simpler.
I really like the layout of Access Rights Manager, which makes navigating between areas easy. Many monitoring and management programs take some time to get used to, because there’s so much going on, finding your way around feels impossible at first. With Access Rights Manager, there’s no learning curve, so you can get started right away. If you run into issues, you can contact the SolarWinds support technicians, who are always available to answer any questions. You can access a free 30-day trial of Access Rights Manager here.
If you’re looking for free user access control software, I recommend starting out with SolarWinds Permissions Analyzer for Active Directory. This is a simple tool, but its useful utilities make it worth noting here. Permissions Analyzer allows you to rapidly identify how user permissions have been inherited and browse permissions by user or group. User permissions can also be analyzed based on permissions and group membership.
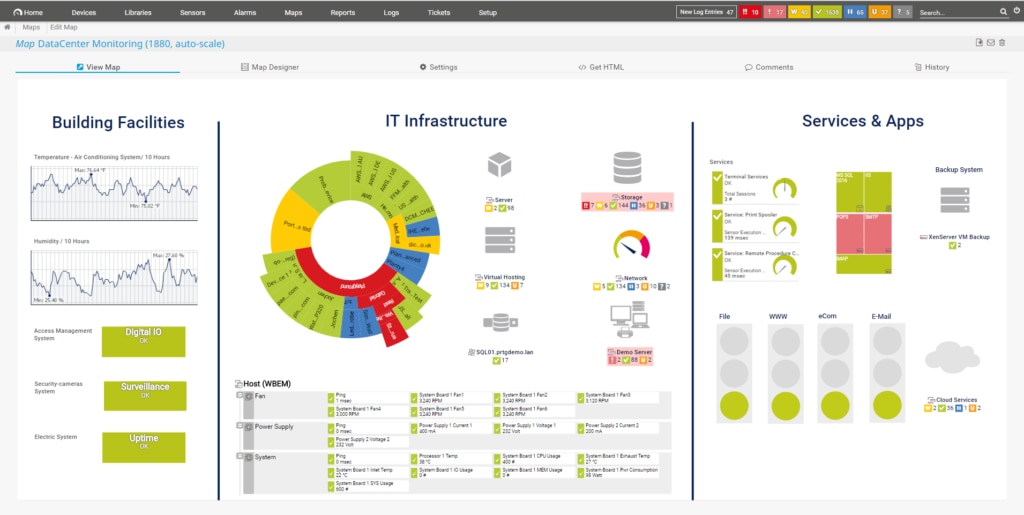
PRTG, by Paessler, is another popular network monitoring product with a massive following. This tool is what you make of it, with the capacity to be extremely comprehensive and serve as a full network monitoring solution. This is because it’s sensor-based, as is the pricing model, which means you don’t use or pay for anything you don’t need. Simply activate the most useful sensors for you.
There are thousands of sensors available, covering almost anything you could imagine, and with the unlimited version of PRTG you can access all of them. Alternatively, if you use fewer than 100 sensors, you won’t have to pay a thing. So, if you’re solely interested in an access rights management tool, you could activate the PRTG Active Directory monitor sensor for free.
The sensor-based system comes with its advantages and disadvantages. On the one hand, it allows you to create a solution exactly suited to your specific purposes, with only the functionalities—in theory—you need. On the other hand, the unlimited version doesn’t necessarily feel like especially good value. If you’re using more than 100 sensors, you’ll have to pay a premium, which means you could end up paying for access to sensors you don’t need.
PRTG is, nonetheless, a robust and well-designed tool. The sensor-based model is unique and offers cost-efficiency for some organizations. The Active Directory monitoring sensor is efficient and fully integrated with the program. It lets you recognize replication errors and identifies any logged-out users and group memberships, as well as monitoring your complete domain forest. It also allows you to see:
- If a source has been deleted
- The number of consecutive synchronization errors or failures
- If scheduled synchronization has been disabled
- The time of the last attempt to synchronize
- The result of the most recent synchronization
- The last time a successful synchronization was executed
- The number of aligned synchronization sequences
- The number of pending replication operations
If you want to try the complete PRTG solution, a 30-day free trial is available. At the end of the trial period, the program reverts to the free edition, so you don’t have to worry about missing the deadline and getting billed.
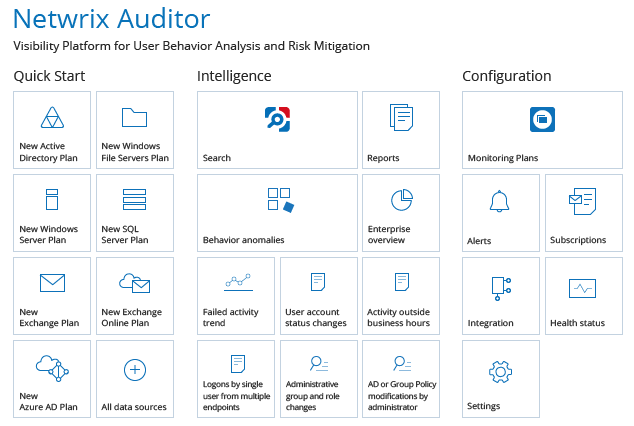
One of the main functions of user access management software is to afford you complete visibility into everything happening in your Active Directory and Group Policy. Netwrix Auditor excels in this area, delivering maximum security intelligence and allowing you to audit any changes and logins to minimize the risk of any privilege abuse occurring. The tool’s auditing utilities also help with proving IT compliance and streamline the troubleshooting process, reducing the time and effort needed to manage user access.
The change auditing feature detects any and all alterations made in your Group Policy and Active Directory, providing critical insight into who made the change, what the change was, when it occurred, and where. It also provides before and after values, so you can get a clear view of what impact the change had.
Login auditing is another valuable feature of Netwrix, which reports on any failed and successful login attempts to critical systems. This facilitates optimal control of access. The tool also tracks ADFS login attempts and can show you the complete login history and activity of any user.
Reporting functionalities are a key part of any successful tool. Netwrix can show you the current status of your groups and users, as well as their permissions, their settings, your GPOs, and much more. By reporting on these current configurations, the tool makes comparisons much easier, and you can establish a baseline for future reference. Netwrix gives you access to out-of-the-box reports aligned with the controls established by a range of standards. This includes GLBA, GDPR, SOX, HIPAA, CJIS, FISMA/NIST, and PCI DSS.
The ability to monitor Group Policy is one of Netwrix’s strengths. The tool’s Group Policy monitoring capabilities allow you to report on any changes to audit policy settings and any other modifications to Group Policy, with in-depth insight into the details of the changes and visibility into before and after values.
It’s fair to say a monitoring system is only as good as its alerts capacity. The Netwrix alerts features keep you informed in real time, enabling you to respond to critical changes or repeated login failures within minutes, which reduces the number of threats to your environment. Alerts can be threshold-based or, alternatively, based on interactive search.
Another notable Netwrix feature is its flexibility—you can download it on-premises for Windows Server, or as a virtual appliance. If you want to give Netwrix a try, a free 20-day trial is available.
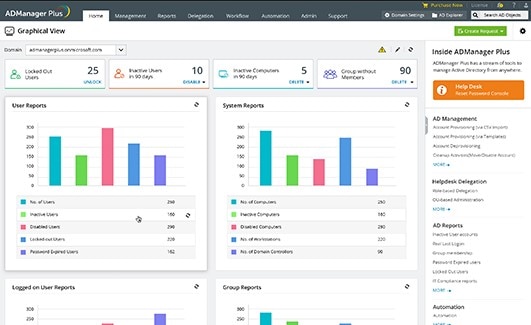
The ManageEngine ADManager Plus solution unifies Office 365, Active Directory, and Exchange management and reporting. It offers a broader approach to Active Directory management than many other access review tools, covering AD objects in general, with instant reporting capability. ADManager Plus boasts 360-degree user provisioning, which lets you provision users in Exchange Server, Office 365, Skype for Business, G Suite, and AD simultaneously. It also accommodates AD bulk user management, so you can create and manage multiple AD user accounts at once by using customizable templates and CSV files.
The password management utilities included with ADManager Plus are impressive, allowing you to reset user passwords and configure password settings. These settings let you determine expiration dates for passwords and when a user must change their password. You can reset multiple user account passwords at the same time; enable, disable, and delete users if their passwords have expired; and tweak settings so users can’t change passwords set by the administrator. Managing passwords can be difficult and time-consuming, with a high likelihood of errors, and the password reports component of ADManager Plus mitigates these issues.
AD group management functionalities are a welcome aspect of this tool, letting you create numerous distribution and security groups. You can do this via smart templates. You can also modify AD groups by selecting the group and importing members, altering group attributes of users in bulk, adding or removing members, and establishing primary groups.
One of my favorite things about ADManager Plus is the file server permissions features. You can set, modify, or revoke NTFS permissions and delegate Windows file server management. You can add, modify, or remove share permissions. ADManager Plus can do more than native AD tools. In addition to the above features, it includes the following capabilities:
- Built-in report library and customizable reports
- Modification templates and rule-based account creation
- Multi-approval workflow
- OU- and group-based delegation
- Automated stale account cleanup
- Time-bound access management
ADManager Plus also includes customizable dashboards, though the user interface could be improved to reduce the amount of time needed to learn how to navigate between views and utilities.
There are three editions of ADManager Plus available. The free edition is for 100 domain objects, offers over 150 Active Directory reports, and includes Active Directory user management and Active Directory computer management. The Standard edition offers all this, plus multiple-domain management, help desk delegation, and Office 365 and Exchange Server management and reporting. Lastly, the Professional version includes everything in the Standard edition, plus file server management, Active Directory OU management, reports scheduling, contact management, OU-based administration, workflow automation, and GPO management.
A 30-day free trial is available for the Standard and Professional editions. You can also register for free technical support.
STEALTHbits Technologies produces several products to support access rights management. These include:
- StealthAUDIT, which automates reporting and governance across multiple platforms
- StealthDEFEND, which detects and responds to any unusual file access and suspicious activity that could be indicative of an insider threat
- STEALTHbits Privileged Activity Manager, which secures, controls, monitors, manages, and removes privileged access rights according to a task-based approach with just-in-time and just-enough privileges
For the purposes of this article, I’ll focus on StealthAUDIT, which allows you to load modules to create a solution tailored to your needs.
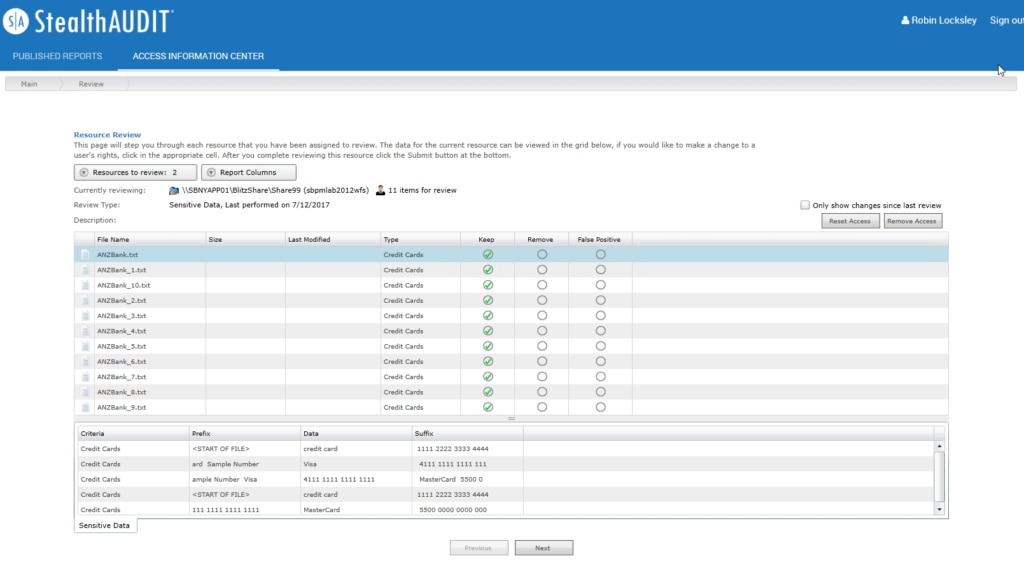
Access Rights Reporter for Office 365 Tenant Roles is a free extension for StealthAUDIT. With this module, you can collect information regarding Office 365 access rights, which is then displayed within the StealthAUDIT Access Information Center. The data is also accessible via custom reporting from within the program.
One of the reasons I like StealthAUDIT so much is because it puts data at the center of its approach to security. While limiting access to data appropriately is important, the tool also recognizes the importance of Active Directory, which depends on the security of the server infrastructure and desktop. StealthAUDIT addresses every single layer of the stack to create a seriously comprehensive, data-centric audit and protection solution. It manages the security of your structured and unstructured data, no matter its location.
StealthAUDIT provides a highly efficient data access governance and privileged access management solution. It can discover where your data is located and then monitor, classify, and remediate the conditions making data access management so tricky. It uses a five-step process to make data access governance secure, compliant, and operationally efficient:
- Discover where the data lives to give you a clear view of your data footprint.
- Collect and analyze data points to answer key questions regarding access, ownership, age, sensitivity, etc.
- Monitor activity to gain an understanding of user interactions with data.
- Restructure access to ensure the Principle of Least Privilege is complied with.
- Govern access on an ongoing basis to facilitate security, compliance, and achievement of operational standards.
This is an effective approach, which is executed extremely well by the program.
Free trials of the STEALTHbits range of programs are available and can be requested on each product page.
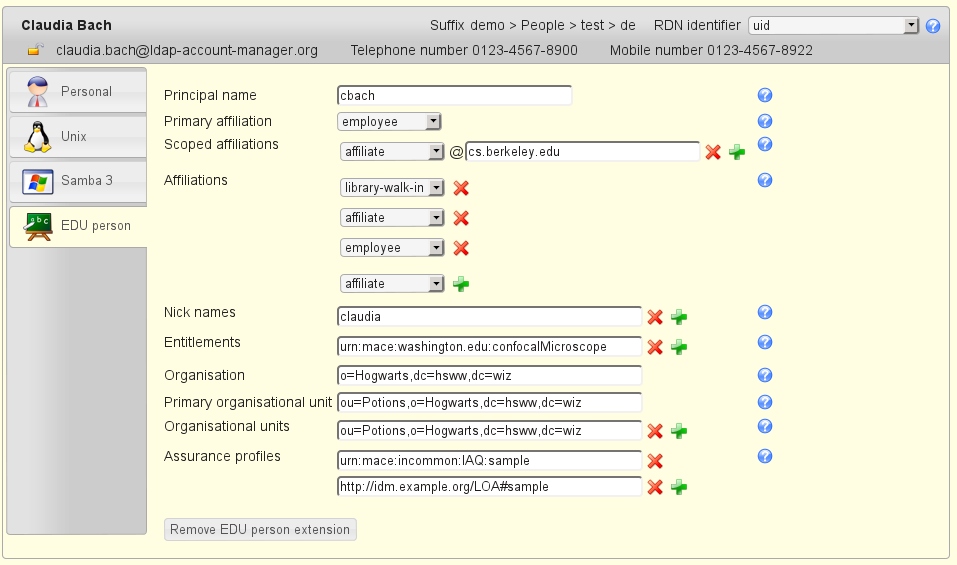
LDAP Account Manager is a web front-end tool for managing entries—including users, groups, and DHCP settings—stored in an LDAP (Lightweight Directory Access Protocol) directory. It can manage Unix, Kolab 3, Kopano, SSH keys, and more. It offers two-factor authentication, CSV file upload capabilities, automatic creation and deletion of home directories, and PDF output for all accounts.
Though LDAP Account Manager is a free access management tool, a paid edition called LDAP Account Manager Pro is also available. Both can run on Fedora, Suse Linux, and Debian. The free edition features a server to safeguard the database of permissions, acting as a domain controller. A client program is also included in the package and serves as an interface through which administrators can add, edit, or delete access rights.
With the paid edition, you can manage multi-factor authentication and access a self-service system with lost password reset utilities. Unfortunately, this tool doesn’t include audit functions, which means it’s not in itself a complete identity and access management solution.
AWS, or Amazon Web Services, is a cloud provider offering web hosting, storage space, and an array of other services. This includes a cloud-based Active Directory manager. AWS Directory Service achieves compliance with PCI DSS and HIPAA requirements through its useful auditing capabilities, which assist with safeguarding the integrity of your data. The tool takes snapshots of your system daily, giving you regular insight, but can also take snapshots on demand. This functionality is especially useful at critical points, like before an application is updated.
Group Policy implementation is a great feature of this program. You can also establish and manage a single sign-on strategy. In addition, you can merge server subscriptions into one forest or separate domain controllers.
As a cloud-based tool, the AWS Directory Service platform can be accessed via your browser. I appreciate this feature because it lets you access the platform from anywhere, provided you have a computer and an internet connection. The disadvantage of this is internet connections are not always entirely dependable. Moreover, some IT professionals argue cloud-based programs are less secure and more vulnerable to attack.
A 30-day limited free trial of AWS Directory Service is available.
Basics of Access Management
Data breaches are becoming increasingly common. Hackers and cybercriminals are in a constant race against IT security software developers to get ahead of the curve, so they can achieve their hacks. The competition is always evolving, which means IT security tool developers have to be vigilant. This is one of the reasons the IT security software market is so saturated, and why choosing between the products available is so difficult.
However, as most individuals in the IT community will know, malicious hackers aren’t the only threat to our IT systems. Many threats come from the inside. These inside threats are perhaps even more dangerous, because we often don’t see them coming. It’s all too easy to assume your personnel are well intentioned, but there have been many instances in which an unscrupulous employee has sold confidential data to competitors for a quick buck. And then there are the well-meaning but ill-informed individuals within a company who are accidentally responsible for data breaches. This may be because they’re unaware of security policies, or perhaps because they have too much access to corporate-grade and highly sensitive information and resources.
The main factors contributing to insider attacks are over-the-top access privileges, the increasing number of devices with access to sensitive data, and the exponential complexity of IT systems in general. Effective access rights management tools are designed to combat these issues by restricting access to file shares, Active Directory (AD), and other business resources in an appropriate way. Access rights management tools ensure access is limited to absolute necessity, which is the most successful way of reducing both malicious and accidental data breaches, attacks, and losses.
What to Look For in User Access Management Software
The function of user access management software is to effectively keep certain areas off-limits to specific individuals, and to ensure the areas that should be accessible remain so. Preventing data theft and accidental data destruction also contributes to the function of user access management software.
There are a lot of access rights management tools on the market, each with a different approach. In some cases, access rights management tools are bundled in with other utilities to create a wider IT management and monitoring solution. Other user access control software will be standalone and entirely devoted to access rights management processes. Some access review tools are free, some are paid for as a subscription, and others ask for a one-time payment. Understanding what makes the most sense for you and your business is key.
Modern networks can be vast and scattered widely across geographical areas, with hundreds or even thousands of devices connected. This scope makes rights management laborious, which means the access review tools you choose have to be powerful enough to contend with the workload. I’d recommend considering this carefully when choosing among access rights management tools. Free tools aren’t necessarily able to cope with enterprise-level requirements.
You also need to consider your business’ needs, and how the software will be used. For instance, a single user or business has very different requirements from a Managed Service Provider (MSP) with dozens or hundreds of clients. If you fall into the latter category, generic software may not be robust or feature-rich enough to help you keep your clients’ data safe.
If this is a concern for you, we suggest taking a look at SolarWinds Passportal. This solution is designed for MSPs, and provides customizable access management that’s fully integrated with its password and documentation management features. This makes it a handy all-in-one tool for handling user access as well as helping to keep passwords secure.
How to Choose an Access Rights Review Tool
Of all the access rights management tools out there, my top ranking goes to SolarWinds Access Rights Manager. It’s rich in features, versatile, comprehensive, and intuitively designed. There’s no learning curve and, therefore, no experience or training required to get started. SolarWinds ARM works for small and large companies alike and is extremely scalable, which means you won’t have to shift to a new program as your organization grows. This software is advanced but user-friendly, which is a rare and valuable combination. You can try it risk-free for 30 days.
Alternatively, if you are looking for a 100% free simple tool, SolarWinds Permissions Analyzer for Active Directory provides instant visibility into both user and group permissions.
