Whether you’re running an instance of open-source MySQL or Microsoft SQL Server, you need to be certain you have robust, high-quality security measures in place. This is extremely important for preventing malicious access to your database, particularly if sensitive or personal data is stored on your servers.
In this article, I cover the essential SQL Server security best practices you need to follow. I will also go over why using a SQL security monitoring tool like Security Event Manager is key to any effective sever threat management solution and the importance of having a SQL Server security strategy.
Here you can find a short list of topics covered in this article:
SQL Server Security Best Practices Checklist
- Isolate your server
- Keep it lean
- Regularly update
- Apply restrictions and a solid security policy
- Manage logins
- Secure backups
- Protect against injection
- Continuously monitor
Best SQL Server Security Monitoring Tools
Why SQL Server Security Is Important
8 SQL Server Security Best Practices Checklist
Data breaches from vulnerable SQL servers can lead to huge amounts of lost revenue and lost trust, as well as fines or penalties for not keeping customer data safe. Luckily, SQL Server has features to encrypt data, as well as limit access and authorization. Let’s look at best practices for using these integrated features to help keep your SQL Servers secure. You can also follow the checklist below to ensure proper setup.
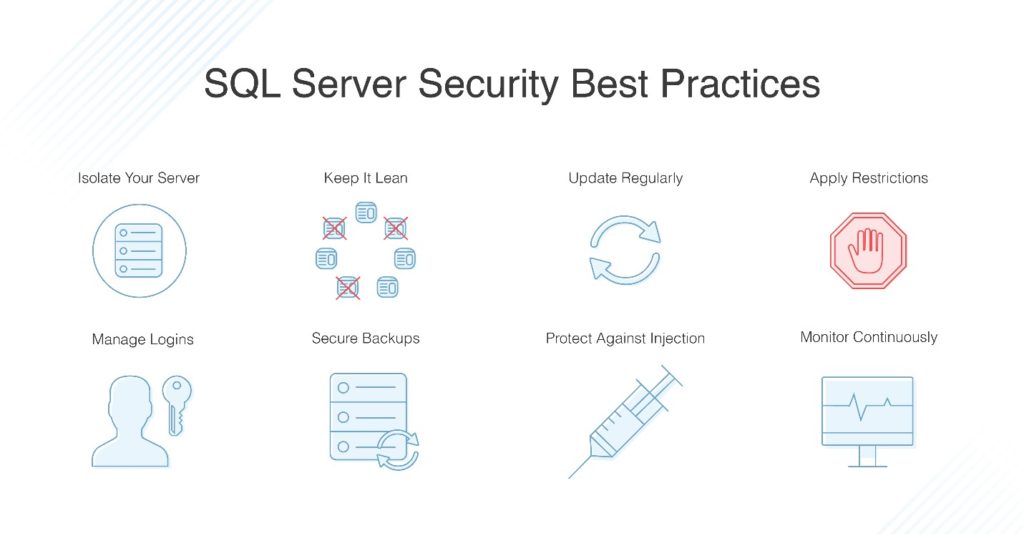
-
Isolate your server
By keeping your server isolated, you help ensure it’s protected from other applications and services that might get compromised. Consider putting your SQL Server in a restricted network segment and allow access only to authorized traffic. The application server or web server should be the only thing communicating directly with the database, and malicious or unexpected connections can be prevented through isolation and restrictive access.
-
Keep it lean
All your systems should be kept lean. This means you should only install the necessary software and services and avoid turning on additional features or installing extra applications. By staying away from software or features you don’t need, you reduce the opportunities for attackers to exploit your server. If you’re testing a feature, do so in a test or development environment, not in the production environment. Also, make sure you turn off the SQL Server Browser when running a default instance of SQL Server. The Server Browser allows admins and authorized users to discover database instances over the network, but if you leave it turned on, it also allows attackers to gain knowledge of your SQL Server resources.
-
Regularly update
Make sure all your SQL Server tools and applications are updated regularly, so security patches can be applied immediately, before it’s too late. Sticking to a regular patching schedule can help with implementing and testing updates in a development environment, so you don’t need to disrupt production until the patch or update is functioning correctly.
-
Apply restrictions and a solid security policy
The user who runs the database service can also access the filesystem, execute programs, and undertake other important tasks. MySQL runs under a dedicated user account with minimal permissions for accessing or dealing with the rest of the server. But on Windows installations, SQL Server is often run as an administrator account, which can allow full access when this isn’t necessary or ideal. Instead, SQL Server should always be run as a local account—not an administrator—without administrator privileges. Restricting access for database user accounts helps make sure a compromised data server or user account doesn’t compromise the rest of the network. You also want to restrict access to the server itself, by allowing only another server to connect to it and blocking all other database ports. Restrict SQL connections to specific IP addresses requiring access to SQL server. Use antivirus and anti-malware software to prevent SQL attacks.
Follow the principle of least privilege when assigning accounts. This means you shouldn’t allow anyone access beyond what they need to do their job. Steer clear of “ALL” grants in MySQL, and don’t allow SysAdmin roles when using SQL Server unless strictly necessary. Always think about how implementing application accounts will affect the resiliency of your server, and run tasks and procedures as a dedicated user with restricted permissions, rather than as a full-access admin. If a user needs escalated access temporarily to perform a task, remove the additional access once the task is completed.
-
Manage logins
Set a strong password for the system administrator account or root user, especially if you have mixed-mode authorization enabled. You should also perform a regular SQL Server security audit, including login auditing. Repeated failed logins can indicate someone trying to access your server, and you can lock down those accounts before they make their way in. In addition, login auditing creates a record you can use later, to show you did all you could to ensure security. Be diligent about deleting or disabling logins after they no longer need to be used. If a login won’t be used for an extended time, such as a couple of months, you should delete or disable it, and then set it up again later when it’s needed.
-
Secure backups
Your backups have all the same server data as your production databases, and thus need to be protected in the exact same way. This means applying the same protocols to your backups, including restricting access, using security measures, and reviewing and controlling who has access to your backup data.
While controlling access to your backups is important, ensuring the security of your backup storage is also vital. That’s why it’s worth looking for a tool that can help protect your SQL backups effectively. For instance, N-able Backup provides a centralized, easy-to-use dashboard along with cloud-based storage that’s optimized for security and performance. It can be used to back up and recover servers, workstations, documents, and more. Plus, since it’s built for managed service providers, it’s able to handle backup and recovery tasks for hundreds or thousands of client sites, designed to maintain server data safely and securely.
Fortunately, there are tools you can use to make this easier. N-able Backup can protect your SQL Server data, storing it in a safe and protected location in the cloud. Plus, you’ll have multiple easy restoration options. For MSPs in particular, N-able Backup can tighten security while also simplifying the backup process.
-
Protect against injection
Make sure your database applications are set up to prevent SQL injection, and you have security tools in place to scan event logs and systems. One of the primary approaches to setting up your SQL Server to protect it from SQL injection is to use stored procedures. These have specific parameters and only accept certain types of code, so when someone tries to send malicious SQL queries, the queries aren’t accepted by the procedure and don’t return any useful information to the attacker.
-
Continuously monitor
Even if you take all the other steps above, your SQL Server could still be at risk of malicious entry. The best and final security measure involves setting up continuous monitoring software, which will help you ensure problems are discovered and resolved as quickly as possible.
Best SQL Server Security Monitoring Tools
There are several tools on the market that can help companies manage security and performance on their databases. Implementing SQL database security solutions should be a top priority for any admin, as without a secure database your information is at risk.
Most Comprehensive Tool
I highly recommend SolarWinds® Security Event Manager (SEM) as a comprehensive tool to quickly and efficiently help detect security threats. SEM has automated incident responses to kill malicious applications or USBs, block IPs, and change privileges or access rights as soon as an issue arises. It also monitors all your files to ensure registry, file, and folder activity is not malicious, which can help in preventing malicious files from being transferred onto your servers.
In addition, you can use the tool to investigate incidents for SQL Server security audit or compliance purposes, to see where something went wrong or where you might have done something differently. SolarWinds offers a 30-day free trial of SEM, so you can determine whether it’s right for your business.
Best Tool for Scalability
SolarWinds® SQL Sentry is built to be scalable with the ability to monitor 800+
SQL Server instances in one monitoring database. While it can be difficult to troubleshoot the issues after they occur, SQL Sentry can help you tackle performance issues in your SQL clusters by allowing you to review performance at specific times and identify when the issue occurred, so you can start troubleshooting it immediately.
Additionally, SQL Sentry includes the ability to grant read-only access to users, allowing support teams the ability to review dashboards to help you align with broader SQL Server security best practices. You can try SQL Sentry free for 14 days.
Best Targeted Tool
For a more targeted solution, look into SolarWinds Database Performance Analyzer (DPA), which continuously monitors your database and its performance, making sure everything is functioning as it should be. It provides insights as to why performance flagged at a particular point, as well as historical data and performance predictions based on past use.
DPA uses machine learning processes to understand how your database users typically operate and can use this information to detect anomalies in performance or red flags signaling a security issue. You can try it free for 14 days.
Honorable Mention
As a (very) honorable mention, we bring you another offering by SolarWinds: Database Performance Monitor (DPM).
As its name suggests, this tool isn’t a dedicated security tool. Instead, its focus is monitoring database performance. More specifically, DPM is a SaaS monitoring solution focused on open-source and NoSQL databases. However, don’t let the “performance” in its name fool you: DPM’s capabilities go way beyond tracking performance metrics. It also offers essential security features.
For starters, DPM comes with sensitive data protection, including GDPR and SOC2 compliance. Some of its main features include:
- MTTD
- MTR
- Deploy frequency
- Availability
- Reduced failed deploys
You can try DPM for free or request a demo on the SolarWinds website.

Why SQL Server Security Is Important
SQL Server is a large, and growing, enterprise-class database platform. As it’s well known, many companies use it. This means significant amounts of critical and sensitive data are stored on SQL Servers, which are increasingly targeted by hackers. If your access to SQL Servers isn’t secure, you leave them open to data breaches and stolen information. Managing SQL Server security can be one of the most complex tasks you’ll have to deal with, but it’s also one of the most vital.
By isolating your servers and keeping permissions strict, features lean, and security and monitoring processes like Security Event Manager at the forefront of your business, you’ll be taking the necessary steps to keep your SQL Servers safe from malicious entries.

