Email protection isn’t something to be taken lightly. Email can put users at risk of scams, malware, phishing, stolen devices, and stolen passwords. Without effective email protection tools, you could be giving hackers a direct route into your data and resources.
But finding the best email protection software isn’t easy. The IT security software market has become increasingly saturated, with every email protection program claiming to be the best. I’ve created this list of the best available email protection software to help you choose between the biggest players in email data protection.
Feel free to jump ahead to each tool review:
- SolarWinds Identity Monitor
- SolarWinds Server & Application Monitor
- Proofpoint Email Protection
- Mimecast
- Barracuda Total Email Protection
In ranking these products, I’ve considered user-friendliness, range of functionality, sophistication of features, and the trustworthiness of the vendor. Overall, SolarWinds® Identity Monitor ranks the highest. This email protection program balances range, ease of use, and sophistication. To find out more about Identity Monitor and how the other products compare, check out my list below.
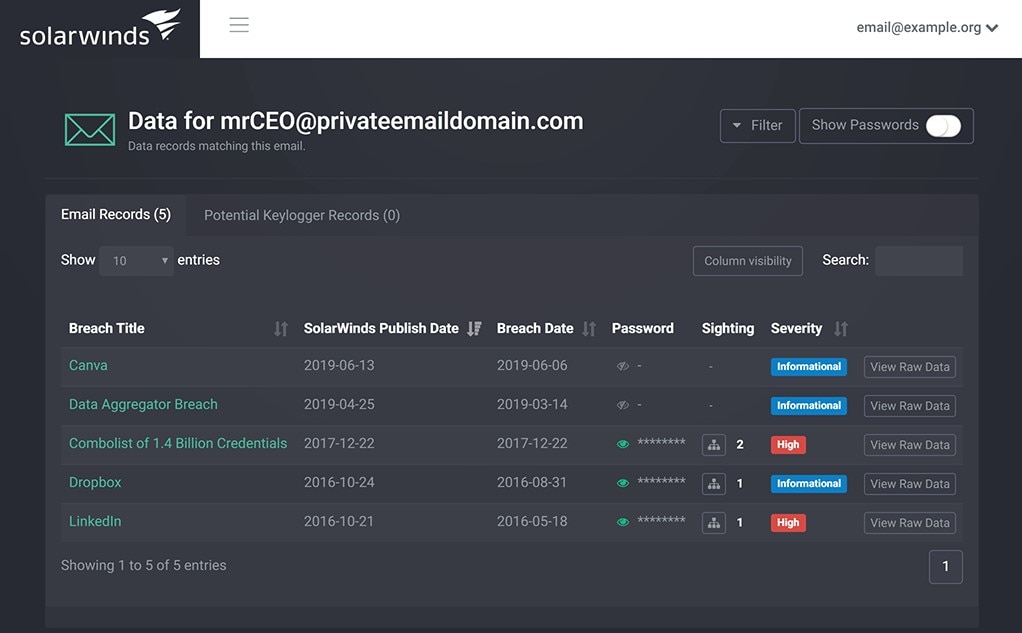
SolarWinds Identity Monitor is a comprehensive and dynamic email protection program. It’s first on this list because its features combine scope, genuine usefulness, and sophistication to deliver a truly enterprise-grade email protection tool. This program employs an attractive user interface designed to be simple and easy to navigate. And unlike many tools on the market, it’s scalable and doesn’t compromise on value as your company grows.
Identity Monitor offers three main capabilities to prevent account takeover:
- Monitoring your email domains for any signs of exposure
- Notifying you of any leaked data
- Resetting passwords before they’re compromised
This tool allows you to establish a domain watch list, which is viewable in a table format. Alongside the domain name, you’ll see when the domain was last discovered, the number of corporate records associated with it, its status, and whether it’s verified. You can perform actions on each of the domains within this page, edit the number of entries you can see, adjust column visibility, and conduct searches. You can also sort information to reflect your priorities.
As soon as a leak is identified, Identity Monitor notifies you, so you can take immediate action. This might include interrogating recent logins or resetting passwords. You can also force password resets for impacted accounts. The program gives you recommendations to keep your team informed on email protection best practices, like maintaining a password manager and using unique credentials.
Identity Monitor is always analyzing new data leaks, alerting you to how many of your corporate records have been discovered in a breach and how sensitive the source is. All collected data is accompanied by contextual details revealing the severity of the breach and the primary concern associated with it (e.g., password reuse).
This email data protection tool lets you add IPv4 CIDR or IPv4 addresses to your watch list, monitoring them for breaches and botnets. You can also monitor the private email credentials of key employees as well as multiple domains.
You can try Identity Monitor for free by entering your credentials into the site, which will show your current level of exposure. A free trial is also available.
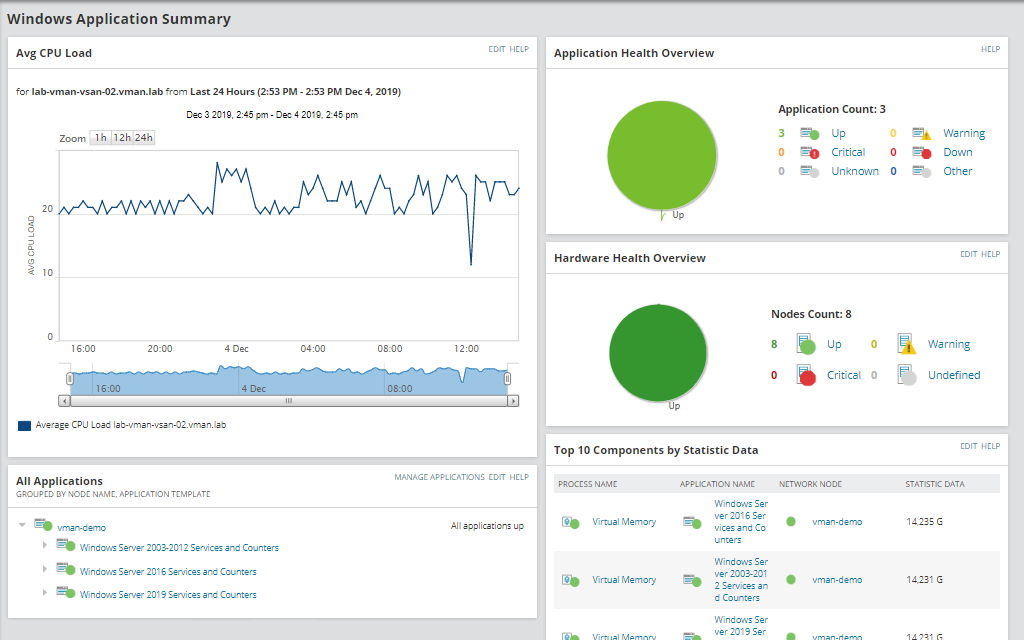
SolarWinds Server & Application Monitor (SAM) isn’t strictly a security solution. It’s an email monitoring tool and an essential part of wider monitoring processes. It’s also highly effective because it consolidates all your email monitoring into a single dashboard. This streamlines your email security and oversight, so you’re always informed.
SAM comes with out-of-the-box mail Exchange server monitoring capabilities, giving you detailed insight into patterns of behavior possibly resulting in poor performance. This includes testing round-trip time and email delivery success for MAPI, POP3, and IMAP4 mail protocols. You can monitor email servers from the end user’s perspective and gain visibility across all top web email clients, including Microsoft Outlook Web Access. This program is powerful enough to manage high email rates, POP3 requests, and MAPI operations, so it can meet the requirements of growing enterprises.
SAM identifies CPU bottlenecks in email servers and unusual spikes in email traffic. It’s able to diagnose issues related to storage, replication, database capacity, and RPC requests in a matter of minutes, and it can troubleshoot in real time. Troubleshooting is supported by historical performance-related data. You can use SAM to view the size of a database, the amount of space currently in use, the total number of mailboxes, and the average size of a mailbox.
SAM is a great tool for investigating potential email issues. It enables you to drill down into key information, search for users, and troubleshoot user problems in Exchange. You can view the size and number of mailbox attachments, patterns in sent and received emails, and synchronized devices, which can assist with the identification of spam issues associated with a user’s account.
Because email protection cannot be achieved without effective email monitoring capabilities, SAM is a valuable addition to any IT monitoring solution. The level of insight this tool provides is unrivaled, affording you rare visibility into your email servers capable of directly informing the actions you take to protect them. You can try a fully functional free trial of SAM for 30 days.
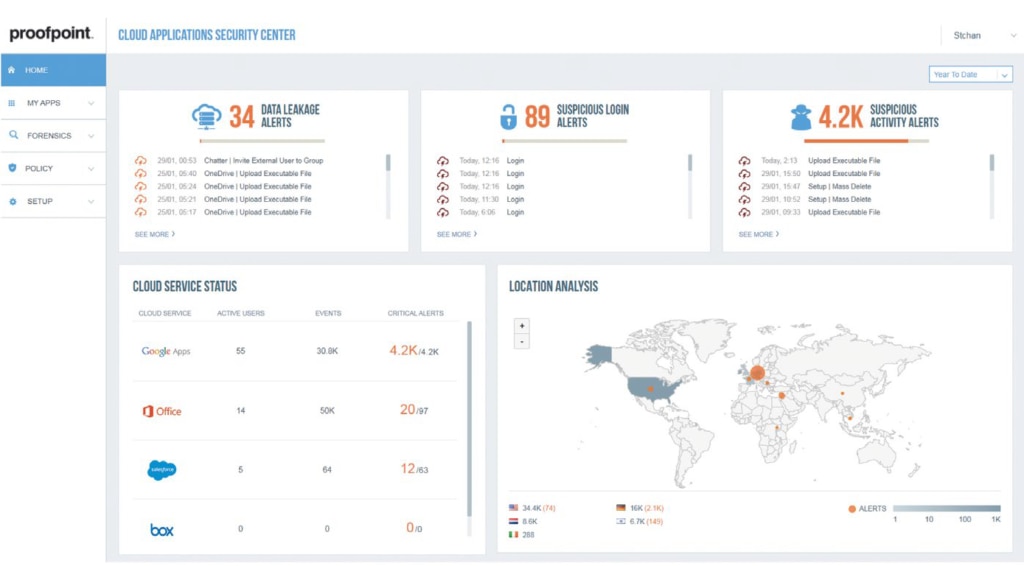
Proofpoint provides many IT security products, including Advanced Threat Protection, Security Awareness Training, Cloud App Security, Information Protection, and Digital Risk Protection. As a security-focused vendor, it’s no surprise the company’s email protection solution is effective. Proofpoint Email Protection establishes numerous security layers to make it as difficult as possible for malware and non-malware threats to infiltrate your email.
This program controls every component of outbound and inbound email, identifying and blocking threats before they deal damage. It also prevents private information from being compromised, shared, or accessed by the wrong people. Email Protection lets you establish email filtering policies as well as complex firewall rules and antivirus policies.
Email Protection leverages everything at its disposal, including user bulk mail actions, to improve future detection accuracy. The program uses a Stateful Composite Scoring Service (SCSS)—a machine learning operation—to recognize and prevent impostor attacks. SCSS learns from your environment and uses Proofpoint customer data to continuously improve its email fraud blocking capacity.
However, Proofpoint Email Protection isn’t as user-friendly as it could be, and it has a steep initial learning curve. You can watch a demo here.
Mimecast offers a cloud-based approach to email protection software. Cloud-based programs can be accessed from anywhere, provided you have an internet connection. The Mimecast solution is intelligent and continuously evolving to keep pace with increasingly insidious and sophisticated threats.
Mimecast is a comprehensive program providing advanced threat protection against spear phishing, email compromise attacks, malicious URLs, weaponized attachments, fraud, social engineering, and much more. It also offers data leak protection, secure messaging, and secure transfer for large files.
There’s zero capital outlay associated with this program, and because it’s cloud-based, Mimecast lets you conveniently deploy company-wide security policies from a single web-based console. However, there is some disagreement about how secure cloud-based solutions are, and some IT administrators will prefer on-premises programs. You can schedule a demo of Mimecast.
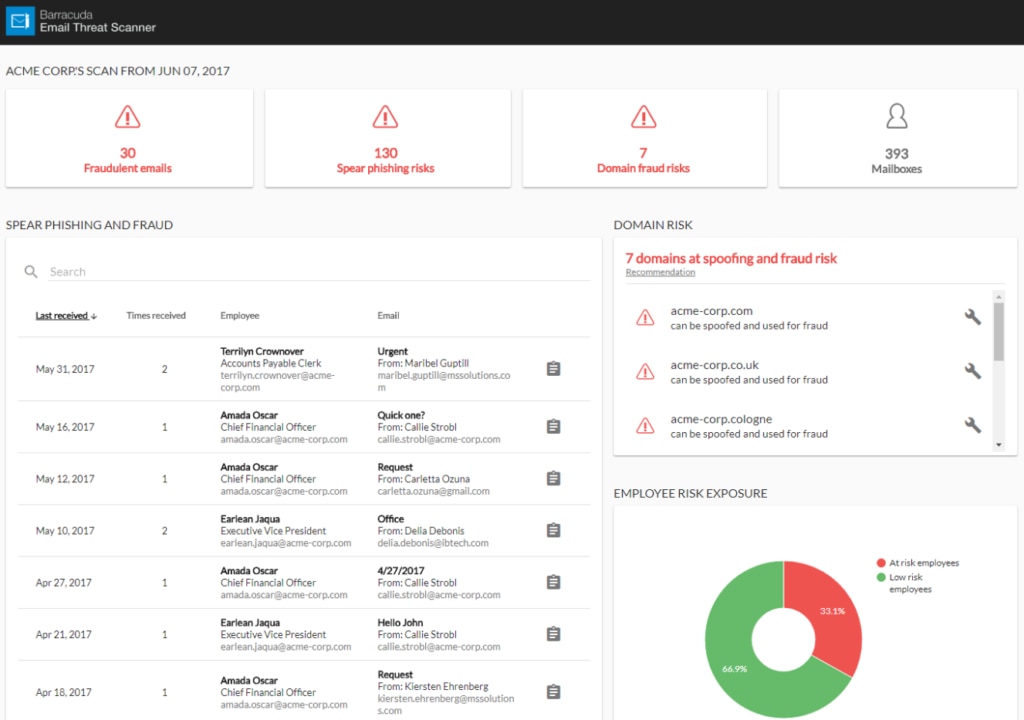
Barracuda Total Email Protection is a bundled solution combining Barracuda’s full range of email protection tools. This bundle is easy to implement and combines basic email protection utilities—like spam blocking, encryption, backup, archiving, and email filtering—with spear phishing simulations, full training, and much more. This bundle is a one-stop solution for email protection, which simplifies due diligence and post-purchase evaluation and eradicates the need to integrate with other products.
Barracuda Sentinel, one of the products included in the bundle, uses a powerful AI engine to detect advanced threats, including targeted spear phishing attacks and account takeover. Barracuda PhishLine, another included product, offers email protection training in the form of a spear phishing simulation platform. With this tool, you can learn to identify email threats, even on devices outside corporate email gateways. Lastly, Barracuda Forensics and Incident Response automates incident response operations, proposing remediation options so you can manage attacks rapidly and effectively.
Barracuda Total Email Protection is an enterprise-grade email protection program, but it may not be suitable or cost-effective for smaller organizations. It could also be more beginner-friendly, as learning to navigate the user interface takes some time. You can request a free evaluation at the bottom of this page.
Choosing the Best Email Protection Software
SolarWinds Identity Monitor stands out as the best email protection tool. The software’s range of functionality is impressive, and its user interface is easy to navigate. This beginner-friendly program offers an enterprise-grade experience at a fair price.
A provider’s reputation is always important to consider, as many vendors provide top-quality tools but can’t be relied upon to maintain prices. SolarWinds has a consistent track record of producing some of the best enterprise-grade IT tools available. Its product range is dependable and well supported. If you’re looking for the best email protection software available, Identity Monitor is the tool for you. Also, if you are a service provider and looking for a cloud-based email security solution, check the email protection software for MSPs.
