PCI DSS is an industry security standard existing primarily to minimize the risk of debit and credit card data being lost. This is in the interest of both the customer and the merchant, because if data is lost or misused, the merchant could be subject to legal action. To protect yourself and your customers, you first need to understand the six PCI DSS control objectives and how to meet them. This guide will give you insight into how you can achieve PCI compliance and provide a list of the best PCI compliance software available.
For those who don’t have time to read the full article, SolarWinds® Security Event Manager (SEM) tops my list of PCI compliance tools, because it offers the most comprehensive means of achieving all of the PCI control objectives and their associated requirements. The most notable benefit of this software is it can be combined with SolarWinds Patch Manager and SolarWinds Access Rights Manager (ARM), both of which also rank highly on my list, to create an integrated and versatile PCI DSS toolkit. These tools were designed to work together to help you address the full range of PCI DSS requirements.
Here you can jump ahead to each product review:
- SolarWinds Security Event Manager
- SolarWinds Patch Manager
- Trend Micro Antivirus for Mac
- SolarWinds Access Rights Manager
- ManageEngine ADAudit Plus
- Splunk Enterprise
- ManageEngine EventLog Analyzer
- Paessler PRTG Network Monitor
- Aruba RFProtect
- Password Gorilla
Understanding PCI DSS Compliance
PCI DSS, short for Payment Card Industry Data Security Standard, encompasses a set of regulations, protections, and policies associated with the finance industry and its customers. These standards were established by the Payment Card Industry Security Standards Council. The council was created by the major credit card providers to commission a shared and consistent set of industry standards, so there would no longer be variances between the credit card provider security systems.
Although these standards are not legally enforceable, businesses are required to comply with them by all major credit card providers, including American Express, JCB, Discover, Mastercard, and Visa. Failure to comply with PCI DSS means a business cannot process card payment attempts made by customers of those card providers. Moreover, credit card companies can issue fines to your bank if you fail to meet PCI standards. These fines can range from $5,000 to $100,000 each month, depending on how severe the breach is. So if you accept credit or debit card payments, compliance with PCI DSS is essential.
The Six PCI Control Objectives
If your company is interacting with cardholder data in any way, then it’s essential PCI requirements are complied with. The six “control objectives” are made up of 12 compliance requirements, which specify how to achieve compliance with each of the objectives. The six objectives, and the stipulations associated with each, are as follows:
- Secure Your Network and Systems
There are two requirements associated with securing your network and systems. The first of these is installing and maintaining a firewall. Firewalls regularly scan traffic passing through your network and prevent occurrences of unauthorized access to the system. A firewall protects cardholder data and must be configured appropriately, so it’s both private and secure.
The second requirement of this control objective is you avoid using passwords or security supplied by the vendor. Because vendor-supplied information accompanies every program sold by the vendor, it is widespread and easily found. Make sure your system passwords are updated and secure to prevent hacking.
- Ensure Safety of Cardholder Data
To meet the requirements of this control objective, you must ensure transmissions are encrypted. Data transmitted across public, open networks is vulnerable, which is why it needs to be encrypted with trusted keys and certifications. You must also ensure PINs and validation codes are deleted once the data has been transmitted.
Taking active steps to protect stored cardholder data is another requirement of this control objective, though this only applies to businesses storing customer information. To achieve PCI compliance, you need to establish multiple defensive layers to protect cardholder data. This should include authentication and authorization methods, and restricting access to networks, storage, and servers.
- Protect against Vulnerabilities
Installing antivirus and anti-malware software is a key component of complying with the vulnerability protection control objective. Malware and viruses can infiltrate your systems in several ways, so it’s important to employ and regularly update your security software. If your software is in need of patching or is malfunctioning, then it’s at risk of overlooking malicious entries, which is why employing an effective patch management tool is highly recommended.
Developing secure applications and systems is also a requirement for achieving vulnerability protection. Make sure your security scanning systems are up to date, and system maintenance prioritizes security.
- Implement Access Control
There are three requirements associated with access control. These include limiting user access, so only those who require visibility of data are authorized to view it. If someone has access, it should be strictly necessary.
Identifying access, the second requirement, entails keeping an up-to-date record of who has access to what data. Every person should have a unique identification number, so their access to data is traceable and they can be held accountable if necessary.
Third, you’re required to restrict physical access to data by ensuring all networks, data centers, and servers are protected by codes, locks, and other security measures.
- Undertake Monitoring and Testing
To comply with the fifth control objective, you’re required to implement monitoring and tracking processes. If cardholder data is accessible to your organization or is being stored in any way, then you must monitor how it’s accessed. This includes tracking user activity to ensure if unauthorized access occurs, you can trace it and take measures to prevent it from happening again.
You’ll also need to test your systems and processes on a regular, scheduled basis. Software vulnerabilities can occur at any time, and the longer an issue goes unnoticed, the more likely it is for cardholder data to be compromised. Frequent testing reduces the likelihood of problems going undiscovered, so you can take immediate action to eradicate any vulnerabilities.
- Implement Information Security
A security policy is required for compliance with the information security control objective. A security policy establishes consistency companywide and should be communicated to all personnel and contractors, so everyone understands the importance of cardholder data and their individual responsibility to protect it.
Best PCI Compliance Software
Given the consequences of failing to meet PCI standards, which include the risk of hefty fines and the inability to take credit cards, implementing PCI compliance tools is highly recommended. To help you choose between the many PCI tools currently available, I’ve provided a list of the 10 best.
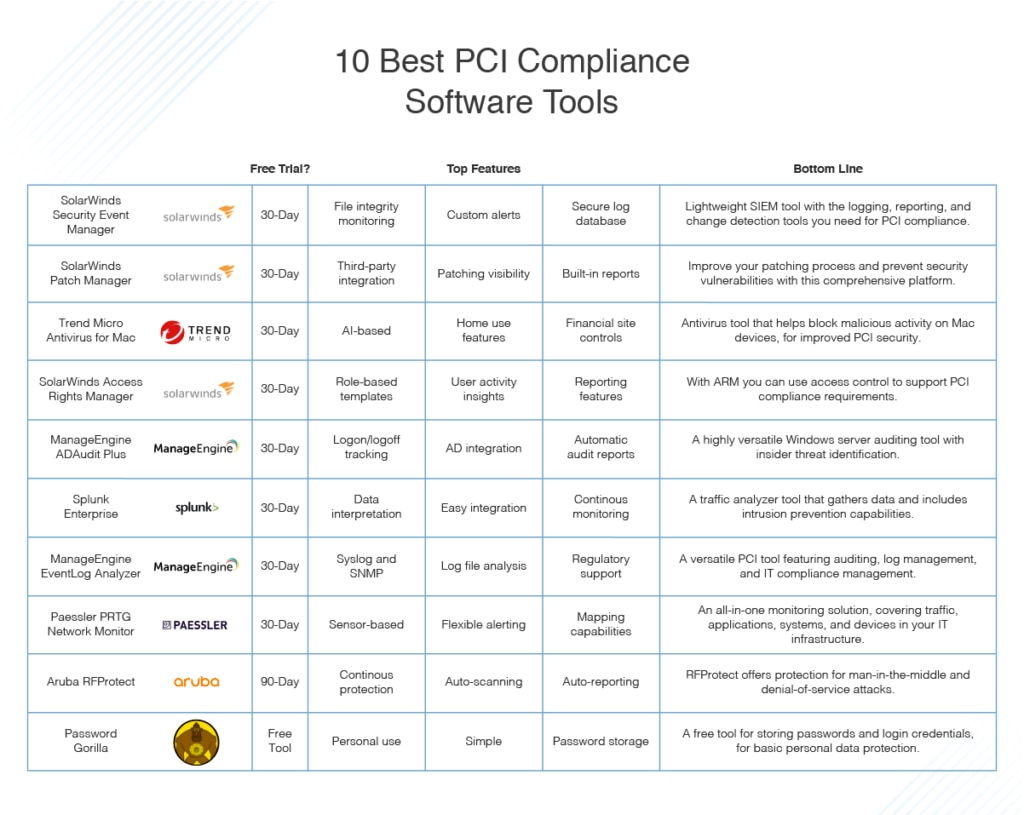
In ranking these PCI compliance tools, I’ve taken into account user friendliness, value for money, suitability for business use, and how advanced and varied the capabilities are, and the dependability and reputation of the provider. Many of these PCI tools offer free trials, so you can experience the tool for yourself before committing to it.
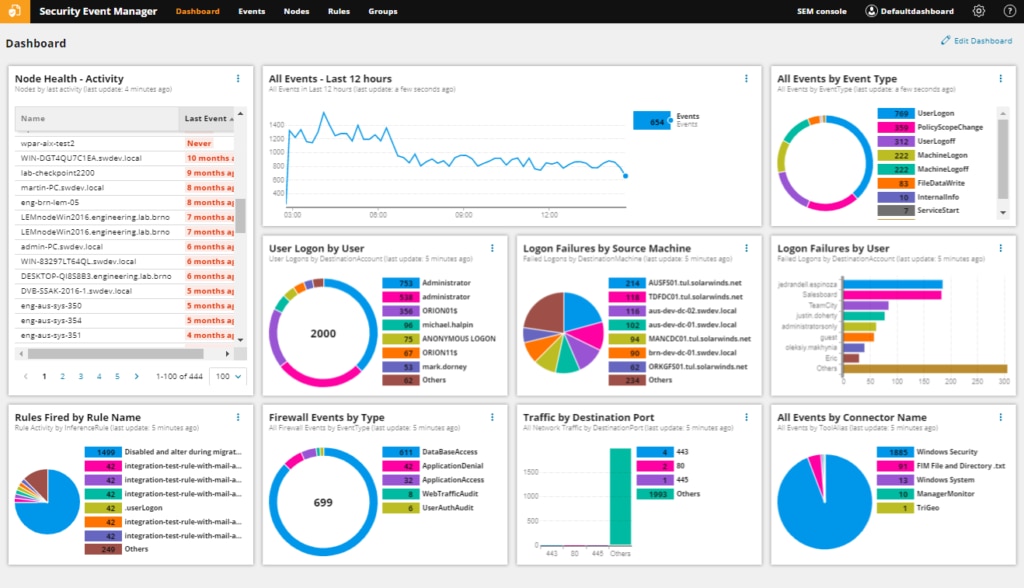
SolarWinds Security Event Manager (SEM) is a security information and event management (SIEM) tool designed to improve your security and demonstrate compliance. It’s a lightweight application with a dynamic console that’s easy to use and navigate. With this tool, your data is displayed graphically wherever possible, making interpretation faster and more accurate. As a security-boosting solution, SEM contributes to PCI DSS compliance in many ways.
SEM offers log collection, log normalization, historical search, endpoint security, compliance reporting, and real-time correlation capabilities. It uses file integrity monitoring to audit who is accessing and altering sensitive data, supporting compliance with the access control PCI requirement. It also monitors access to cardholder data without maintaining databases or files, and you can configure alerts to notify you if unauthorized access occurs. This complies with the PCI stipulation of all access to cardholder data needing to be restricted.
Among its appliance security and data protection processes, the tool utilizes multiple controls to safeguard audit trails, ensuring they’re accurate and complete. Moreover, SEM features a range of out-of-the-box PCI content, which helps with reviews of log data. This includes log filters, correlation rules, reports, and charts.
To ensure effective and safe log retention, SEM uses a highly compressed and secure log database. You’re able to schedule archives to offload log data to cold storage, if appropriate. This ensures you’re keeping what you need for when you need it and disposing of information you are no longer authorized to retain.
SEM also addresses several other PCI requirements, including usage of default accounts, ensuring AV is generating log data, ensuring antivirus processes are active and unchanged, logging various audit trails, including timestamps with all logs, and deploying change detection mechanisms. Out-of-the-box PCI FIM templates are included with this PCI DSS compliance software, to assist you with monitoring any access or changes to system files of a critical nature.
This lightweight program covers an impressive array of PCI requirements, offers advanced capabilities, and is notably user-friendly. Because it’s a SolarWinds product, it integrates beautifully with other SolarWinds tools. As such, it is easily extended as a PCI compliance solution with, for example, SolarWinds Patch Manager and SolarWinds Access Rights Manager, both included on this list.
A 30-day free trial of Security Event Manager is available.
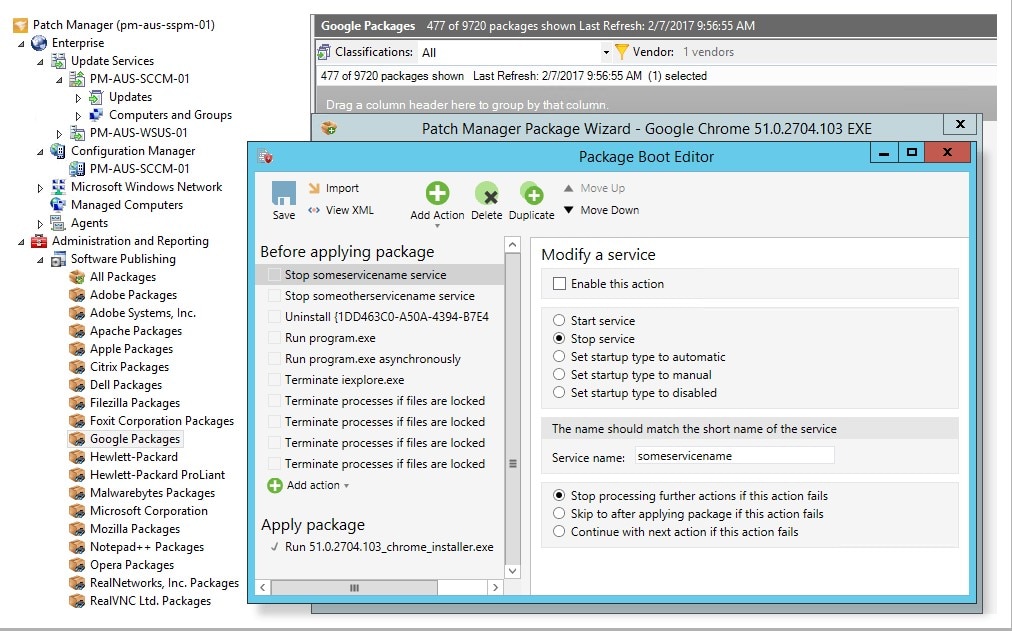
SolarWinds Patch Manager was designed to address software vulnerabilities. It offers integration capability with native Windows patching technology and provides patching for third-party applications, workstations, and servers. This is a simple tool to automate patching and reporting, saving you time and resources. By controlling what’s patched at what point, and certifying patches are applied, Patch Manager helps you decrease risks to security and limit interruptions to service.
PCI DSS compliance requires proof all your workstations and servers, however many hundreds or thousands you might have, are up to date and patched appropriately. Patch Manager helps ensure software has the latest patches within a month of their release, deploying both third-party and Microsoft updates to keep your equipment updated. Its out-of-the-box reports help with rapid identification of missing patches and notify you as to which of your machines haven’t been patched. Moreover, it helps you demonstrate patch compliance by allowing you to produce summary reports displaying patch status.
This PCI compliance testing software assists with certifying all antivirus systems are up to date and current, by performing software inventory to identify all installed applications and their versions. With out-of-the-box inventory reports, you can identify antivirus software needing to be updated. Patch Manager gives you granular control over your patches, letting you decide which are approached for deployment. You can approve patches for test machines to ensure the patches are validated before the production deployment stage. This capability assists with the PCI requirement requiring change control procedures and processes be adhered to for all changes to your system components.
As a SolarWinds product, Patch Manager would complement a wider SolarWinds solution and could be used to extend the PCI compliance capabilities of SolarWinds Security Event Manager or SolarWinds Access Rights Manager. A 30-day free trial is available.
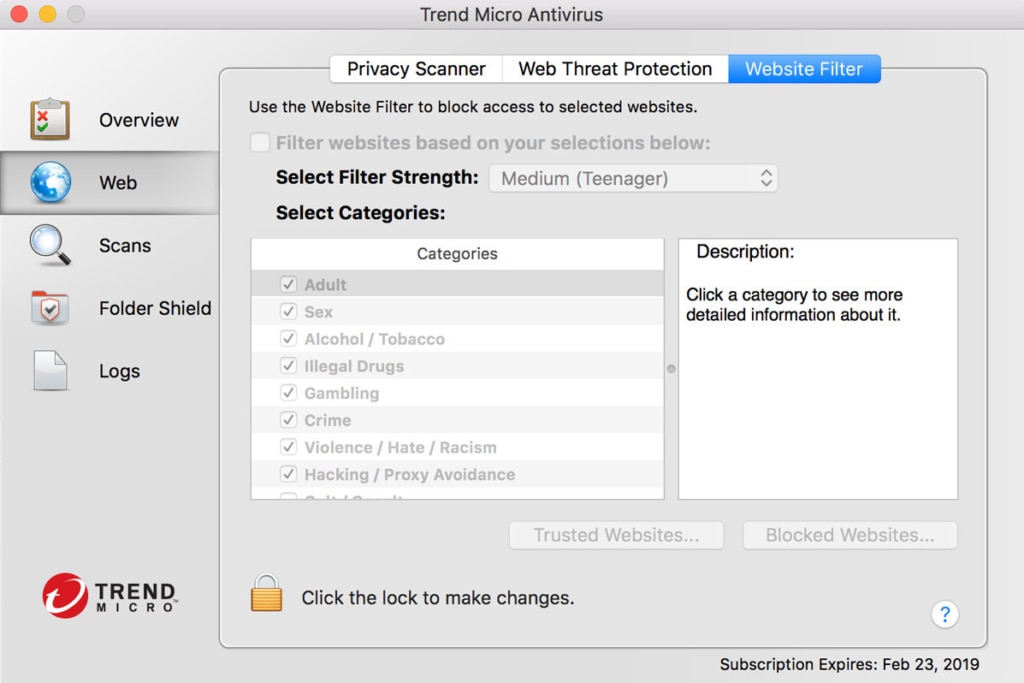
Vulnerability protection is one of the six PCI control objectives and complying with it requires you have appropriate anti-malware and antivirus systems in place. Trend Micro Antivirus for Mac is one of the best antivirus programs available because it simplifies protection while addressing advanced and complex threats.
This PCI compliance software can significantly improve your security through a range of sophisticated capabilities. It can defend against online dangers (including ransomware), prevent software attacks, protect you from phishing emails, prevent unauthorized access to your microphone and camera, and block malicious websites, so you can browse safely.
Trend Micro uses an AI-based detection system, which means it can defend against even the newest viruses. This program is easy to use, with intuitive settings and status reports. Unfortunately, as the name suggests, it’s only available for Macs. Maximum Security is an alternative product by Trend Micro, available for use with Windows, Mac, Android, and iOS devices. Though this tool is more expensive, it allows you to protect up to 10 devices on a one- or two-year subscription basis.
Both Trend Micro Antivirus for Mac and Trend Micro Maximum Security meet several PCI DSS requirements, and as such are good options for businesses. Maximum Security comes with the added benefit of keeping your transactions secure, using a proprietary system to certify financial sites are legitimate. There are also password management capabilities.
Although Trend Micro products may be suitable for use by businesses, it’s clear they have been designed for home use. Many of the utilities—like mechanisms to keep your children safe online—are likely to be obsolete for businesses, which reduces the value.
You can access free trials of the Trend Micro tools here.
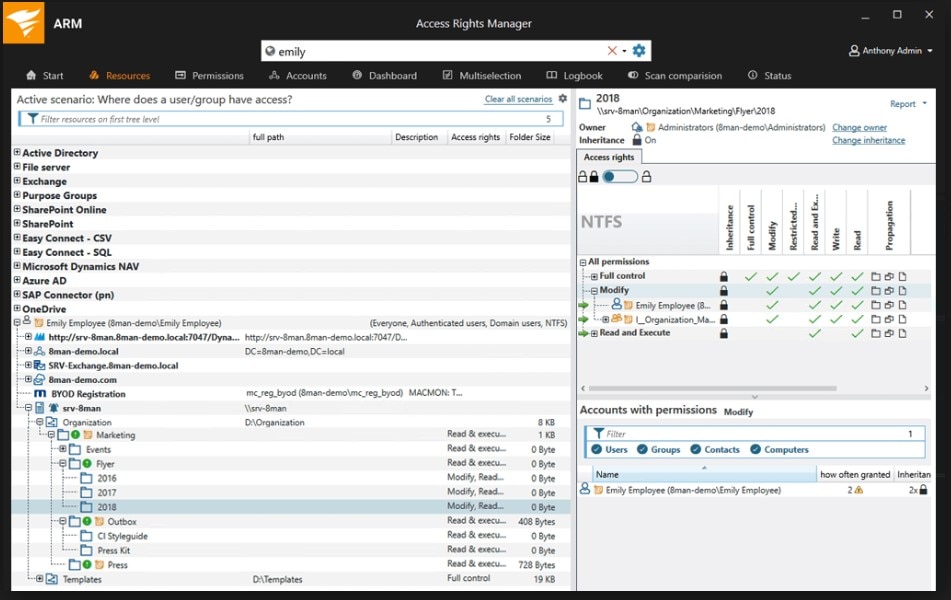
SolarWinds Access Rights Manager (ARM) mainly addresses the access control PCI objective, enabling you to analyze access permissions to your data, systems, and files to protect your organization from data breaches and losses. It allows you to create customized reports outlining which of your staff have access to what information, and when the information was accessed. All these reports can be generated to support PCI compliance requirements.
The tool also features provisioning and deprovisioning capabilities, which can be performed by utilizing role-specific templates, certifying access privileges are aligned with security policies. With ARM, you’ll be given maximum control over access, while the program works to minimize insider threat exposure.
As a PCI DSS compliance software application, ARM can help you achieve compliance with multiple requirements. User provisioning functionalities limit access to cardholder data and system components by letting you create user accounts in Active Directory, assign group memberships, populate related attributes, and deprovision users when appropriate. On-demand or scheduled reports, delivered automatically, can help you demonstrate compliance.
These user provisioning and deprovisioning capabilities also address two other PCI requirements—one demanding procedures be defined and implemented to ensure user identification is managed properly, and the other requiring access to any database containing cardholder data be restricted. ARM serves as effective PCI logging software, addressing the PCI requirement stating audit trails linking access to individual users be implemented. The program’s logging capability allows for access to certain data to be monitored.
ARM features a risk assessment dashboard, which can help you identify misconfigured access rights potentially exposing sensitive data or make the data vulnerable to breaches. By utilizing the risk assessment dashboard on a quarterly basis, you can meet the PCI requirement of running internal and external network vulnerability scans at least once every quarter.
If you want to try Access Rights Manager, a 30-day free trial is available.
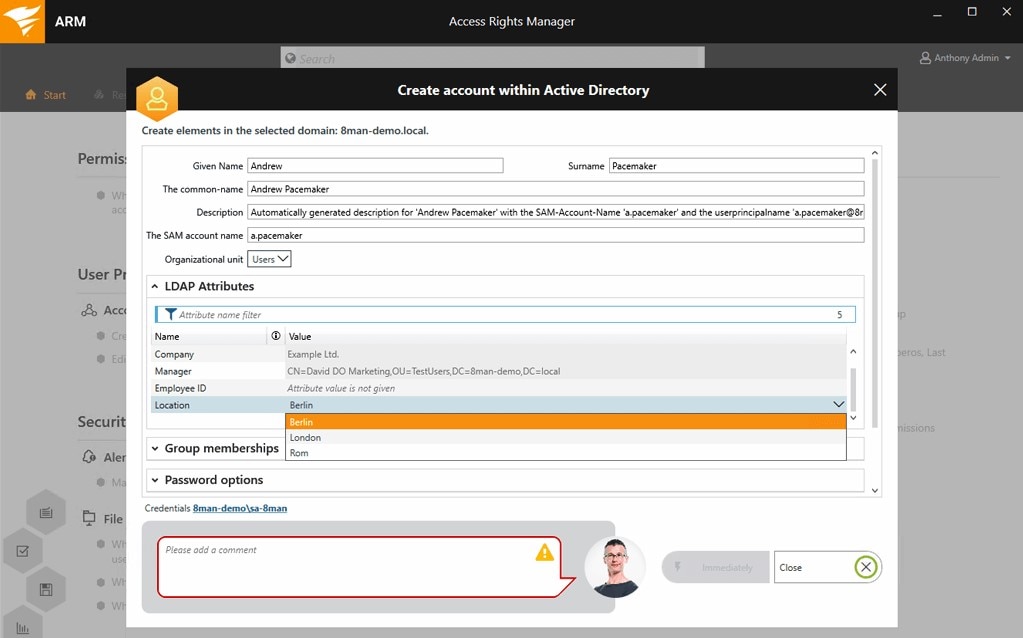
This is an Active Directory-focused tool used to monitor and log any alterations to permissions. It’s an excellent tool for implementing and demonstrating PCI DSS compliance because it runs audit reports automatically. ADAudit Plus is a highly versatile auditing tool covering Windows logon and logoff auditing, Windows file server auditing, and Windows server auditing, which means you can implement everything from printer auditing and file integrity monitoring to user logon monitoring and insider threat identification.
ADAudit Plus audits your Windows Active Directory in real time, ensuring your critical resources are monitored, audited, and reported on. These processes take into account all AD object information, including groups, users, group policy objects, organizational units, computers, DNS, configuration changes, and AD schema. The application offers more than 200 preconfigured GUI reports. Reports are compliance specific, including for PCI DSS, and can be scheduled and customized to suit your specific organizational needs.
ADAudit Plus delivers preconfigured, customizable alerts on unauthorized modification events and network access. With compliance-specific email alerts as standard procedure, you can rest assured your network will be monitored on a 24/7 basis. Still, although this is a powerful business-grade solution, users would benefit from it being easier to integrate with other programs to create a comprehensive PCI DSS toolkit.
A 30-day free trial is available, after which the program will automatically revert to the free edition.
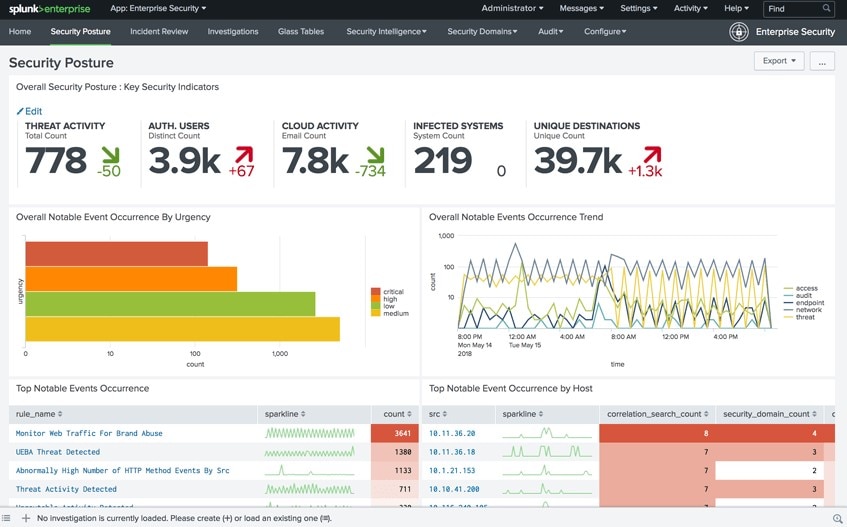
Splunk Enterprise is all about empowering you to turn data into action. It ingests data from multiple sources, devices, systems, and interactions, and then turns the data into actionable business goals and meaningful outcomes. Although Splunk is commonly known as a network traffic analyzer, the Splunk Enterprise and Splunk Cloud editions also offer intrusion prevention capabilities.
With visualized metrics, these tools make interpreting and responding to the latest data fast and easy. Splunk Enterprise features an analytics workspace, where you can convert logs into metrics and boost the performance of your search and monitoring functionalities. It uses integrated, machine learning analytics to facilitate a future-centric, proactive approach to data. Instead of reacting to current issues, it helps you predict and prevent. This contributes to the overall aim of PCI DSS, because it focuses on preventing issues, rather than responding to them.
One of the most notable benefits of Splunk Enterprise is it’s easy to integrate with other tools. Splunk Connected Experiences is a secure, encrypted cloud service allowing mobile devices to communicate directly with both cloud-based and on-premises instances. Using Splunk Connected Experiences, everyone on your team can interact with your data and view insights wherever they are—no need to configure firewall rules or open ports. The service includes Splunk Mobile, Splunk TV, Splunk Natural Language Platform, and Splunk Augmented Reality, providing flexible access to data insights.
This software offers continuous monitoring of conditions, KPIs, and events, with out-of-the-box monitoring dashboards for common application, IT, and security environments. Combined with real-time alerts, these monitoring capabilities assist companies in meeting PCI monitoring requirements.
You can access a free trial of Splunk Enterprise here.
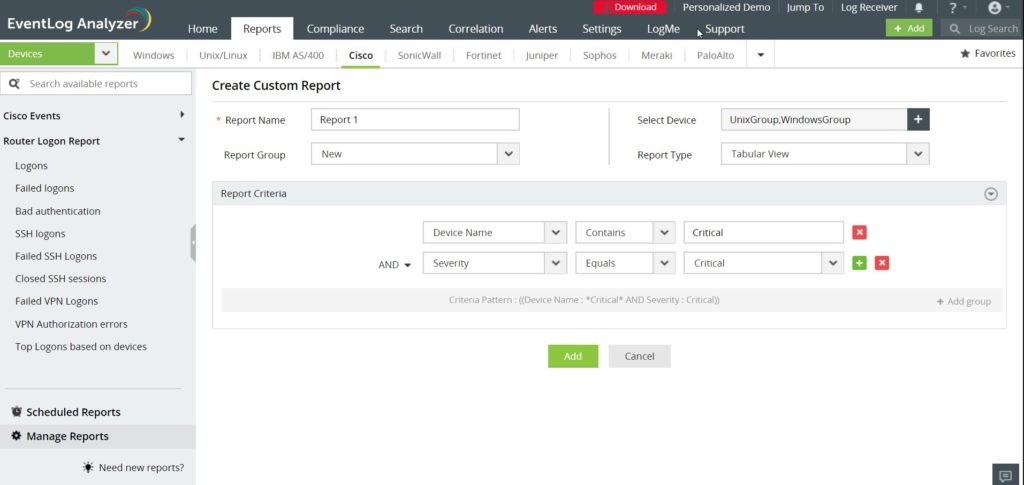
EventLog Analyzer is an effective PCI logging software program, offering compliance auditing for PCI DSS. It features auditing, log management, and IT compliance management, making it a versatile PCI tool. This program tracks syslog messages and uses SNMP processes to identify anomalous network activity. All log files are protected with encryption and compression, requiring user authentication before the data can be accessed.
EventLog Analyzer actively listens to your logs: it collects, manages, correlates, analyzes, and searches through data logs from over 700 sources on an out-of-the-box basis. It uses agentless log collection, agent-based log collection, and log importing to deliver a flexible and versatile solution. The tool even comes with a custom log parser to extract fields from human-readable log formats, which is a highly sophisticated utility.
EventLog Analyzer supports compliance with multiple regulatory mandates, including HIPAA, PCI DSS, FISMA, GDPR, SOX, and ISO 27001. It allows you to archive log data for the period of time you specify, helping you comply with the log archival stipulations of most compliance mandates.
The tool is able to audit log data from multiple perimeter devices, including switches, firewalls, routers, and IDS/IPS. This functionality affords you valuable insight into user logon and logoff attempts, inbound and outbound traffic of a malicious nature, and firewall security policy and rule modifications. All this data is presented in the form of predefined reports, and you can use templates to establish alert profiles to keep you informed of unusual events. This is a powerful PCI compliance tool from a dependable provider, but it’s worth noting there’s an initial learning curve.
There are three editions of EventLog Analyzer. Although the paid versions do not offer free trials, you can download the free edition here.
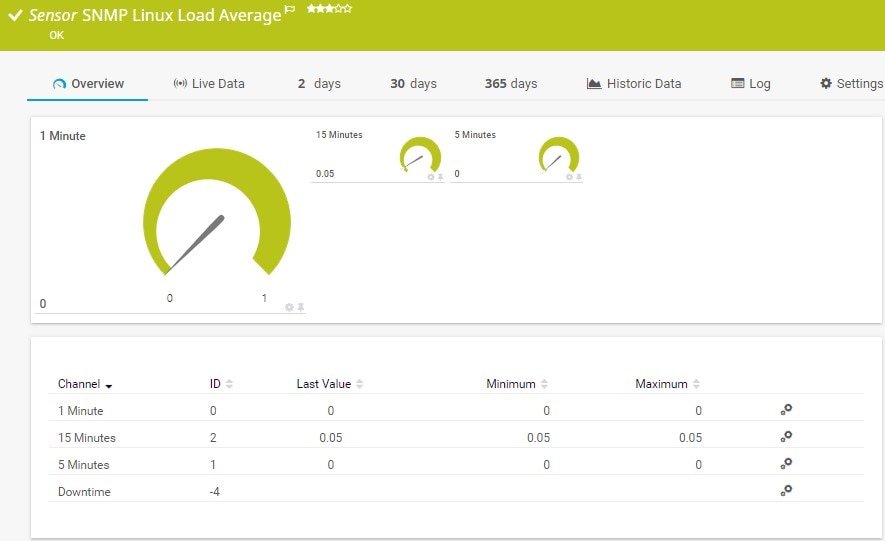
Paessler PRTG Network Monitor offers a range of monitoring capabilities to address and assist with meeting PCI monitoring and tracking requirements. PRTG is a truly all-in-one monitoring solution, covering traffic, applications, systems, and devices in your IT infrastructure.
PRTG doesn’t require any additional downloads or plugins. It’s a sensor-based solution allowing you to selectively implement the features you need. For example, you could employ a sensor for monitoring the workstations, switches, servers, printers, and routers on your LAN, or you could implement a bandwidth monitor.
This tool supports all key technologies, including SNMP, WMI and Windows performance counters, HTTP requests, ping, SQL, and REST APIs returning JSON or XML. It’s great for facilitating accurate and fast data interpretation, because it allows you to visualize your entire network in the form of real-time maps. You are also able to create your own dashboards with the intuitive PRTG map designer, with more than 300 map objects at your disposal.
PRTG offers flexible alerting with numerous built-in mechanisms for notifying you—these include HTTP, email, and push notifications. Paessler also provides Android and iOS mobile applications, so you can receive notifications directly to your phone. Alerts can be scheduled to suit your needs.
With hundreds of sensors available, covering almost every monitoring functionality you can think of, PRTG is one of the most versatile PCI compliance tools. On the downside, it’s entirely focused on monitoring and doesn’t integrate well with other solutions, which means creating a comprehensive PCI DSS toolkit could be tricky.
You can access a free trial of PRTG Network Monitor here.
RFProtect is a wireless intrusion protection program offering a sophisticated solution to man-in-the-middle and denial-of-service attacks, and mitigating security threats occurring over the air. It uses Aruba access points to serve Wi-Fi clients while containing threats.
This PCI compliance tool provides around-the-clock defense against threats and attacks, including ad hoc networks and unauthorized Wi-Fi clients. It constantly scans the environment, proactively contains rogue hardware, locks down device configurations, and evaluates forensic data.
One of the main benefits of RFProtect is it allows you to automate compliance reporting. You can tailor reports to suit your unique audit obligations. RFProtect compliance audit capabilities support PCI DSS, HIPAA, Department of Defense, and GLBA requirements, among others, and internal corporate regulatory mandates.
To get a quote for Aruba RFProtect, contact the sales department directly.
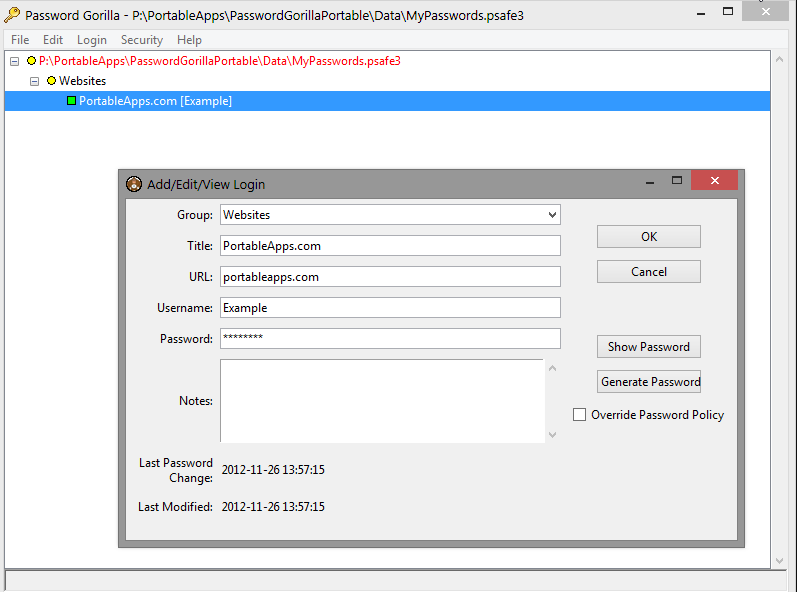
Password Gorilla addresses the password management aspect of PCI DSS compliance. It’s a free and simple, but effective cross-platform password manager. Password Gorilla stores all your passwords, usernames, and other login credentials in an encrypted file. A master password protects this file, keeping it secure, which means you only need to memorize one password.
When you attempt to log in to a website or service, Password Gorilla automatically copies in your login credentials, allowing you to paste it into your application or browser. The password does not appear on the screen, so Password Gorilla can be used even when other people are around. This tool also features a random password generator, so you can create one-off passwords customized to suit specific password requirements.
Password Gorilla is free to use and can be run on Windows, Linux, and Mac OS X. Though I love the simplicity of this tool, it’s better suited to personal use than to business use.
How to Get Started With PCI Compliance Software
The main purpose of PCI DSS is to establish the minimum amount of security required for any business taking card payments. When it comes to PCI compliance testing, software is vital to ensure all requirements are met. The PCI control objectives, however, cover a range of security practices and processes. As such, a single PCI tool is unlikely to facilitate full PCI compliance on its own.
The PCI control objectives encompass password management, antivirus and anti-malware operations, access control, patch management, data protection, and monitoring and tracking processes. For businesses seeking to successfully manage all these components and achieve compliance, the SolarWinds PCI compliance software range—which includes Security Event Manager, Access Rights Manager, and Patch Manager—is the most dependable solution. In particular, you can’t beat the flexibility, extensibility, and comprehensiveness of Security Event Manager. An important benefit of choosing a SolarWinds tool is you can implement it individually and then add to it as needed.
