With Windows Active Directory, a range of different account types can be set up with the necessary permissions, access, and roles. These include service accounts, which are intended for use when installing applications or services on the operating system. Common types of Active Directory service accounts include built-in local user accounts, domain user accounts, managed service accounts, and virtual accounts. These accounts have broader privileges and greater access to the infrastructure than other accounts, which makes them vulnerable to security exploitation.
In this article, I’ll set out best practices for keeping your service accounts secure as well as explain why the final and most important service accounts best practice is making sure you have a solution like Access Rights Manager to provide critical insights into your AD permissions.
Jump ahead:
- Keep access limited
- Create service accounts from scratch
- Don’t put service accounts in built-in privileged groups
- Disallow service account access to important objects
- Remove unnecessary rights
- Set access by using the “Log On To” feature
- Limit time frames
- Control password configuration
- Enable auditing
- Implement access rights management software
How Active Directory Service Accounts Work
Each type of service account has its own operation purposes.
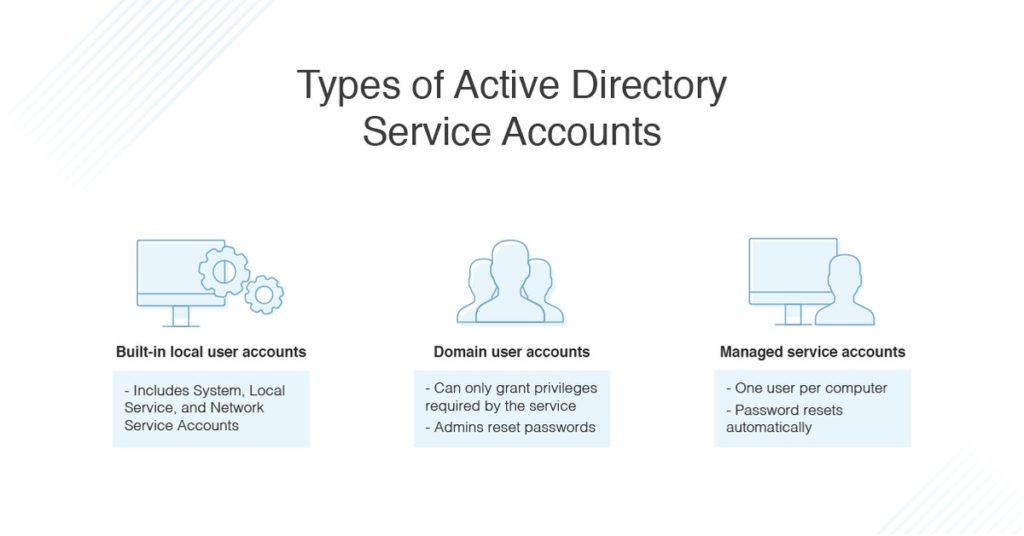
- Built-in local user accounts include the System account (for local system administration), the Local Service account which accesses network services with no credentials, and the Network Service account which accesses network resources using the computer’s credentials.
- Domain user accounts are intended for use by services and are centrally managed by Active Directory. It’s possible to create a user account for a single service, or to share it across multiple services. However, with domain user accounts, you can only grant the privileges required by the service, and you need to reset passwords regularly.
- Active Directory managed service accounts are similar to domain user accounts, but the password is reset regularly and automatically. You can only assign one user account per computer, and each account can be used with multiple services on the computer. Alternately, you can create separate accounts for each service.
The benefits of a managed service account include heightened security and ease of maintenance. Moreover, these accounts can run services on a computer with the possibility of connecting to network services as a specific user principal. However, it’s important to regularly audit these accounts and know some best practices to ensure security.
Active Directory Service Accounts Best Practices
- Keep access limited. Ensure you only allocate AD service accounts the minimum privileges they require for the tasks they need to carry out, and don’t give them any more access than is necessary. In many cases you can remove the functionality for remote access, terminal service login, internet access, and remote control rights.
- Create service accounts from scratch. Don’t create service accounts in Active Directory by copying old ones, as you might accidentally be copying from a service account with much higher privileges than you need. This could lead to security issues and account misuse if you give someone an account with access to resources or information they shouldn’t be privy to.
- Don’t put service accounts in built-in privileged groups. Putting service accounts in groups with built-in privileges can be risky, because each person in the group will have access to the service account’s credentials. If there’s account misuse, it can be hard to figure out who the offender is. If you need a service account for a privileged group, create a new group with the same privileges and allow access only to the service account.
- Disallow service account access to important objects. Use an access control list to protect sensitive files, folders, groups, or registry objects from misuse by AD Service Accounts. To disallow access, go into an object and open the “Properties” window to access security permissions, add an account to the “Permission Entry” list, and set the status to “Deny.” This will prevent the service account from accessing the object. If you need to give someone specific access to the object, you can add them, then switch them back to “Deny” later, when they’ve finished their task.
- Remove unnecessary rights. Denying nonessential user rights is helpful to keep security measures strong. This includes “deny access to this computer from the network,” “deny logon locally,” and “deny logon as a batch job.”
- Set access by using the “Log On To” feature. When you create a service account, you can allow it to only log on to certain machines to protect sensitive data. Open Active Directory Users and Computers, then “Properties.” In the “Account” tab, click the “Log On To” button and add the computers to the list of permitted devices the service account can log on to.
- Limit time frames. You can add extra security by configuring AD service accounts to be allowed to log on only at certain times of day.
- Control password configuration. You can set a service account so the user can’t change their own password. You can also set it so the account can’t be delegated to someone else. This ensures the administrator controls the password, and nobody other than authorized users has access to the account.
- Enable auditing. Be sure to enable auditing for all service accounts and related objects. Once auditing is enabled, regularly check the logs to see who’s using the accounts, when, and for what purposes. Auditing is one of the most important of the best practices: it helps ensure security, verifies internal processes and compliance measures are being followed, and can discover any issues or breaches before too much time passes.
- Implement access rights management software. Being careful is crucial to preventing misuse of broad access and privileges. An access rights management tool can be beneficial to ensure user accounts are set up and managed with appropriate permissions and access.
I recommend SolarWinds® Access Rights Manager (ARM), which is built to automate account management process and reduce the time you need to spend provisioning. The software also includes detailed auditing and compliance monitoring tools to help you meet strict security compliance requirements, including policy- and industry-specific compliance regulations such as GDPR, PCI DSS, and HIPAA.
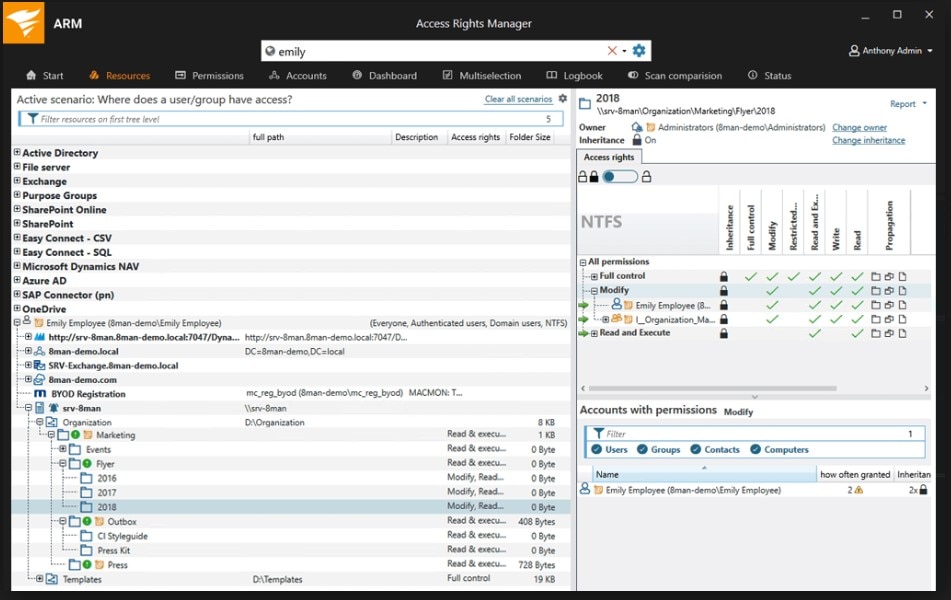
The auditing tools in ARM are simple and easy to use, and they allow you to quickly create auditor- and management-ready reports on account use as well as behavior to show adherence to important security processes.
Another solution worth checking out is Passportal. This is a password management solution for MSPs and other IT service providers, as well as large corporations and businesses of all types.
With Passportal, you get access to a centralized cloud-based platform for managing passwords. You can store as many passwords as you need, search for and change them at will, and configure the setup to meet your needs.
So if you need a way to manage your Active Directory credentials—or those of your clients—Passportal is a comprehensive solution. It’s designed to be secured as well, so you don’t need to worry about your passwords and other key data falling into the wrong hands.
