Depending on the success of your database audit trail program, creating an audit trail for your data log can either be a benign part of company protocol or a major nuisance. Several industries, from health care to finance to public works, require detailed reporting of data logs through an audit trail. When your company’s data is audited for compliance with regulations like HIPAA, SOX, and PCI using predisposed templates, you need to be ready to streamline the process and provide auditors with proof you’ve remained within regulatory guidelines.
Oracle is commonly used to collect and store company logs. It also connects into database-capable servers like Microsoft SQL Server and is compatible with Windows and Linux operating systems (with the exception of Oracle 9, which cannot be used in Linux). Once installed, an Oracle database can track a vast array of user activities on the company network.
While Oracle offers some configuration options to help with compliance, it’s typically necessary to link the program up to more robust tools to easily and effectively prove compliance. In this article, we’ll look at the reasons for using an audit trail, types of data you can audit, and best practices to help you get the most out of your Oracle audit log. I’ll also discuss how even if you’re focusing only on Oracle database logs, the amount of data you’ll need to collect and analyze can be prohibitive. So, having a log monitoring solution like Security Event Manager in addition to some other important Oracle monitoring solutions can help support your ability to follow best practices for auditing Oracle database logs – which I will describe in more detail below.
Jump directly to the section of interest to you:
Why Use an Audit Trail for Oracle Database Logs?
What Kinds of Data Can I Audit?
Oracle Database Auditing Best Practices
Best Practice #1: Optimize Your Database
Best Practice #2: Analyze Your Data
Best Practice #3: Protect Your Network
Why Use an Audit Trail for Oracle Database Logs?
Aside from industry audit trail standards, there are many reasons to use a database log as part of managing a successful enterprise. Oracle can collect a diverse variety of data in its database log, with the specificity of the data based on the level of sophistication of your Oracle audit script.
Basically, database audit trails are used to ensure your data is secure, and your users are doing what they’re supposed to. Security concerns can be traced to machines through analysis of the data log and flagging of the suspicious data can be enhanced with certain applications to automatically track and report suspicious data identified during the database auditing process.
User compliance can also be measured through an audit trail, since data logs collect user information such as login data, machine use data, and activity data.
What Kinds of Data Can I Audit?
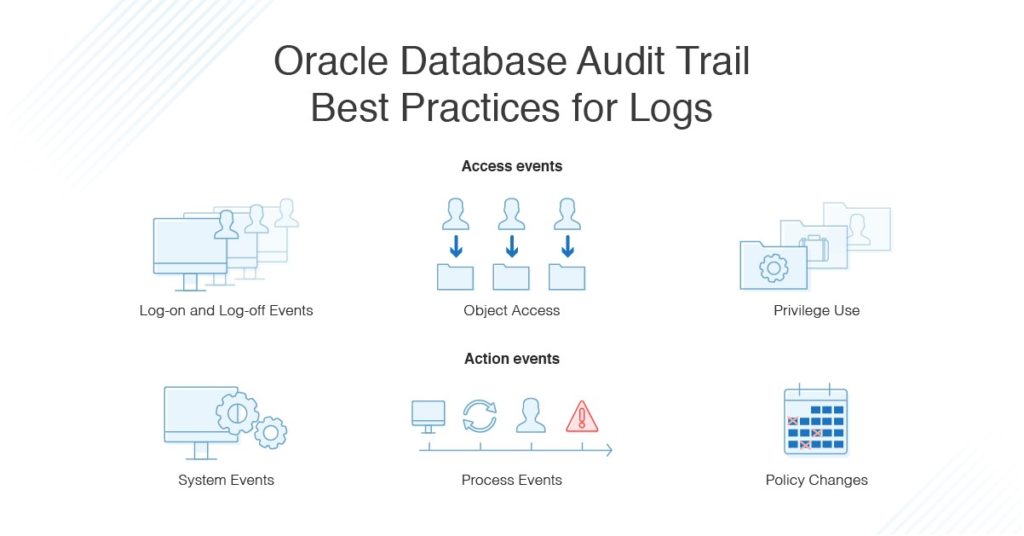
The first consideration in implementing an Oracle database, and later an audit trail of your data log, is the type of data you’d like to audit. You can audit two main categories of data in your system: access events and action events.
Access events include:
- Log-On Events: View who’s been logging on to what units in your system.
- Log-Off Events: View who’s been logging off what units in your system.
- Object Access: View who’s been accessing what files in your system.
- Privilege Use: View object access according to the assigned system privileges to different users.
Action events you may wish to monitor include:
- System Events: See when a change has been made to your system.
- Process Events: View what processes have taken place in your machines, such as shutdowns.
- Policy Change: See when a certain network policy has been changed or abandoned. In security auditing, tracking policy change can be critical so you’ll know if any safeguards have been disabled in your system.
If your company is subject to audit requirements from a standard protocol like HIPAA, for example, it’s worth checking out the types of data HIPAA requests for their audit trail report. If you don’t have specific parameters, consider the basic data tenets to help you keep tabs on your security and user access info. At the most essential, an Oracle audit log should track who’s logging in to your system, who’s logging out, and who’s making changes to the system.
Though these audit trails can be supremely useful, they can also be difficult to navigate without the use of applications to analyze data and earmark unusual data points.
SolarWinds offers multiple extremely helpful solutions for managing my data logs and making the best possible use of my database audit trail. I’ll explain in the next section exactly how SolarWinds® Database Performance Analyzer (DPA), Log Analyzer, and Security Event Manager (SEM) can help optimize your Oracle database auditing process, analyze your data, and protect your network.
Oracle Database Auditing Best Practices
Administering a database audit trail not only enables detailed data collection, but it might be the first step in your journey to a complete and robust data tracking system. To maximize efficacy, I recommend employing software with data analytics and visualization, as well as security software linked to your Oracle database to trigger an immediate response to safety threats.
Below I’ll explain 3 Oracle audit trail best practices and corresponding tool every IT should consider using to help you make the most of your audit log.
Best Practice #1: Optimize Your Database
SolarWinds DPA offers a comprehensive solution to performance concerns you may encounter when using an Oracle database to analyze company data. In addition to Oracle, DPA is compatible with other database systems, like MySQL, DB2, SAP ASE, and the cloud. This wide range of compatible integrations is an advantage to any company with a reason to expand their database inventory past Oracle.
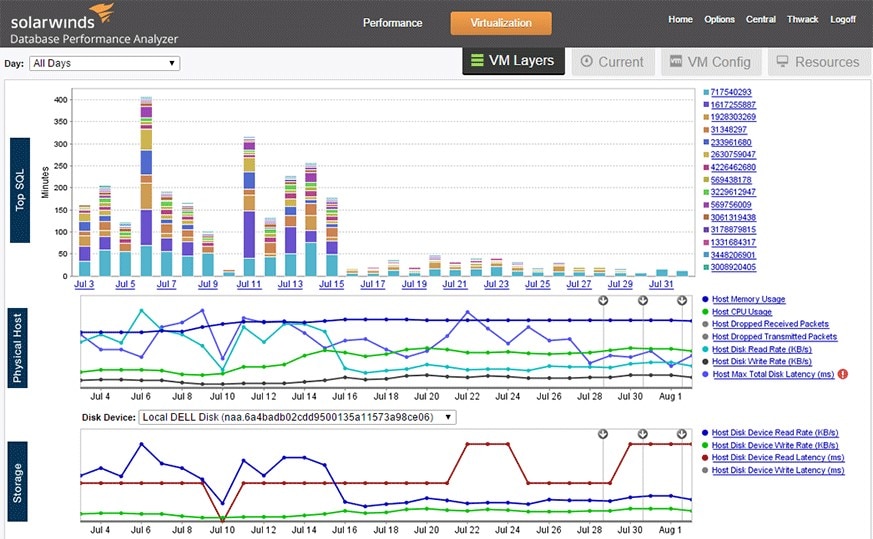
DPA is particularly useful as an analytical tool. With clear visual displays of statistics generated in real time based on network data logs, administrators can pinpoint exactly where the inefficiencies lie, and even receive recommendations on what steps to take to increase productivity.
SolarWinds DPA is also built to allow a central manager to detect unusual instances in user behavior within the network. Based solely on access and action events in the data log, this feature has the capacity to identify why your company is experiencing inefficiencies. Since the anomaly detection in Database Performance Analyzer is machine learning-powered—its algorithm is constantly adjusting when it obtains new data—the program’s recommendations get more and more accurate over time.
DPA also analyzes data logs to assess workloads from different machines in the system. This is useful in locating productivity gaps among various regions of the system. In this way, DPA helps you identify which areas are having the greatest negative impact on the system, which in turn may help you reallocate resources to fix trouble spots in efficiency.
After you’ve been using DPA in conjunction with an Oracle database for a while, there is a chance you will wish to focus on one aspect of the database’s performance analytics—there can be a great benefit to analyzing data with regularity and focusing your efforts on the trouble spots. DPA allows you to use an API to designate your focus areas for future observations.
Best Practice #2: Analyze Your Data
While DPA analyzes your log to help you assess your users’ performance trends, what if you want to analyze the functioning capacity of the machines in your network? When used correctly, log data can also serve as an extremely effective troubleshooting tool.
SolarWinds Log Analyzer constantly collects machine data to build an increasingly complete record of what your bottlenecks and machine efficiency issues might be.
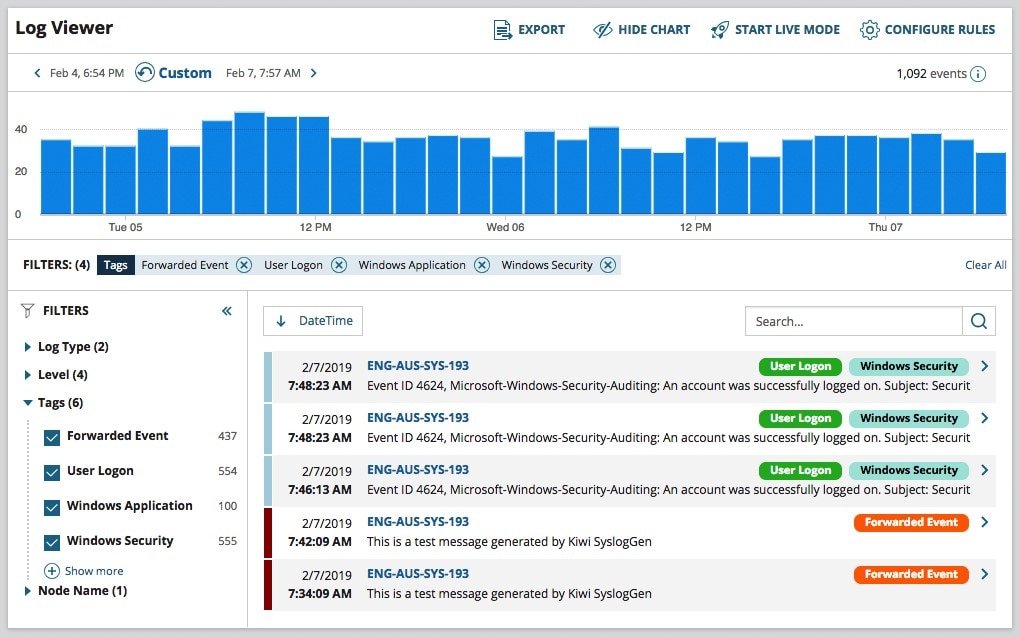
Log Analyzer paints a vivid picture of the immense collection of data in your Oracle log. It can be difficult to diagnose IT inefficiencies from a database when there is so much access data with hidden trends. I’ve found Log Analyzer helps me make sense of IT discrepancies in my log through detailed visual analysis of trends, helpful labels of data categories, and a search bar to help me investigate any hunches I might have about the network.
And Log Analyzer doesn’t operate in a vacuum—making it useful for a large network with a complex database. It can be easily integrated into my existing Orion® Platform, a centralized solution from SolarWinds. Once Log Analyzer is integrated into my Orion Platform, the IT performance data collected by Log Analyzer is managed in tandem with other diagnostics and insights from my other SolarWinds products. This paints a holistic picture of my network’s IT performance using both log data and intrinsically gathered network performance intel.
Best Practice #3: Protect Your Network
So far, I’ve discussed the use of software to optimize performance (with DPA) and analyze log data (with Log Analyzer). Along with optimization and analysis, security is a crucial Oracle audit log best practice. You can greatly increase your ability to detect and eliminate security threats by integrating security tools into your Oracle database.
Security Event Manager is software from SolarWinds that can be integrated seamlessly into your database. Once you’ve properly configured SolarWinds SEM into your Oracle database, SEM will closely monitor your database for any security threats.
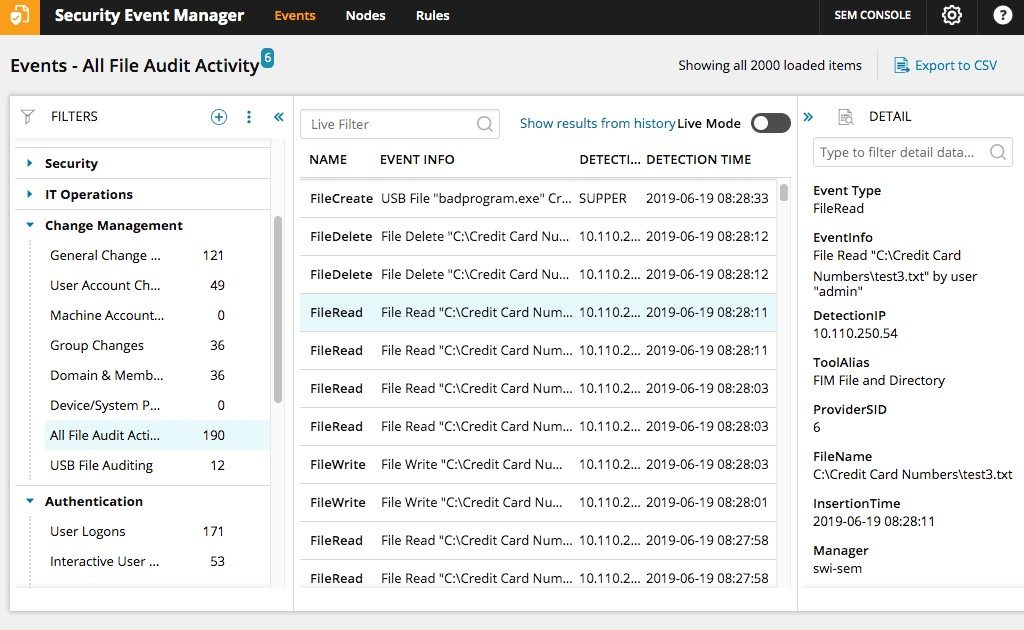
To connect SEM to an Oracle database on a Windows OS, you can follow the steps outlined on the SolarWinds website. (Integrating SEM into Oracle would take an additional few steps if you were working on a Linux operating system. Instead of following this configuration, you would have to syslog SEM into your system. Instructions on how to do this can also be found on the SolarWinds customer support website.)
SEM observes user access data to detect any possible insider threats from a password-protected user who makes undesired changes to company data, and it closely observes the database for any evidence of outsider threats, such as hacking or viruses. If a threat is detected, SEM has the capability to disable compromised accounts, log off suspicious users, disconnect USBs, and even shut down entire machines—all in real time.
Many standards of database audit trail compliance, including HIPAA, require companies to have security systems in place to monitor data from outside interference. This is another reason I highly recommend SolarWinds SEM—its security standards are compliant with more audit trail protocols than most competing data security programs.
Further Reading
How to Do Performance Tuning in Oracle
I’ve written a handy how-to guide for performance tuning to help with your Oracle management needs.
Must-Know Tips and Tools for Oracle Virtualization
If you’re integrating Oracle into a virtual machine, you should know a few things first.
A quick rundown on how professionals in the medical field can protect data and databases to comply with HIPAA regulations.
Security Logging Best Practices for Retention and Monitoring
Ensure your security logging process helps protect your overall IT infrastructure.


