As regulations around data protection and concerns around privacy increase, identity access management helps organizations monitor data, grant permissions to access that data, report on how they comply with compliance regulations. Adopting the proper enterprise identity and access management software can help organizations more easily navigate the often-complicated process of improving security and compliance. Of the below tools, one excellent option is SolarWinds Access Rights Manager (ARM), which makes it easy to audit and manage access rights across your organization.
What Is Identity Access Management (IAM)?
Enterprise identity and access management (IAM) helps a business or organization protect and manage its electronic and digital properties by providing a framework of processes, policies, and technologies to control who can access sensitive or crucial information. IAM is usually implemented and maintained by IT professionals. It includes features such as single sign-on systems, two-factor authentication, multifactor authentication, and privileged access management to provide a network of protection for data and files. In addition to enterprise user access management, IAM systems are also used to store identity and profile information. They include data governance functionalities to ensure that only relevant data is shared with those authorized to view it.
While IAM systems are sometimes deployed and maintained on-premises, many enterprise access management solutions are provided by third-party vendors using cloud-based subscription products or maintained through a hybrid of the two approaches.
Components of IAM
Most end users are somewhat familiar with IAM systems, as we use them for everything from logging into email accounts to making bank transfers. However, enterprise identity and access management is much more than securely logging in to view data.
First and foremost, an IAM system allows IT professionals to control user access to critical data within an organization. Most IAM solutions provide role-based access control allowing system administrators to govern access to systems based on the roles individual users have within a network. For example, a college professor might not have access to all the student data made accessible to financial aid, though both use the same system to access student data. Instead, IAM controls the ability of individual users to perform the tasks specific to their roles, such as viewing, creating, or modifying files, using relevant access based on job, authority, and responsibility within a company.
IAM systems also create a log of who is accessing information and when. Enterprise access management will capture and record information at the time of login while also managing a database around enterprise identity access management, which controls assigning and removing access. Enterprise user access management involves keeping and updating centralized directories that allow for oversight and visibility of all the data belonging to an organization’s user base.
While we primarily associate IAM with protecting personal data, enterprise access management can also be used to protect and manage the digital identities of devices and applications connected to a network. These protections can go a long way toward establishing trust in end users and customers.
Importance of IAM
Over the past decade, businesses, specifically IT departments, have come under increasing pressure to provide greater protection for organizational data and user information. Due to this pressure and regulatory standards, traditional systems — which often include error-prone, manual processes to assign user privileges and track access — have become nearly obsolete. Instead, automated enterprise access management provides granular control of data while also allowing for security auditing of all the corporate data included within the cloud.
Though enterprise identity and access management is usually associated with solutions like two-factor authentication, its capabilities have grown at the same pace as the potential for breaches. IAM now includes capabilities such as biometrics, behavior analytics, and AI. These new approaches to enterprise access management are much better suited to the needs of growing organizations, which typically include more devices and applications than ever before.
Advantages and Benefits of IAM
Enterprise identity and access management includes gathering, capturing, recording, and managing all user information and sensitive data within an organization. Beyond greater peace of mind, adopting a robust IAM system has many benefits.
Reduced Costs
Manual enterprise access management is both time-consuming and costly. Adopting an automated system for employee onboarding, offboarding, and role changes frees up IT teams for other tasks and reduces the potential for error.
Increased Productivity
By ensuring employees have quick and easy access to the data they need to perform their duties, employees can more easily log in and safely move between platforms and tools without the aid of the help desk.
Improved Security
One of the primary goals of enterprise access management is ensuring that only authorized users have access to an organization’s crucial information. Implementing an IAM system further enhances existing security by putting protocols in place in case organizational data is compromised.
Easier Compliance
With many regulations in place to ensure organizations are going out of their way to protect data, the right IAM system can easily show the exact ways in which data is being protected, along with demonstrating the controls in place to continuously monitor those protections. IAM tools can also automate compliance tasks to meet requirements without draining IT resources. Finally, a good enterprise access management system creates a historical database of activity so organizations can learn which areas require greater protection or improvements over time.
Enterprise Identity and Access Management Software
When it comes to adopting an enterprise identity and access management system, it is important to know exactly what you’re getting. Not every enterprise access management system also includes enterprise user access management. Here are the three main types of enterprise identity and access management software:
IAM
Outlined above, IAM includes both identity verification and access management. This means it provides support for authentication, authorization, user management, and credential storage across your IT infrastructure.
AM
Often used by smaller organizations or organizations not subject to compliance regulations, access management (AM) allows users access to information once they are authenticated once they obtain the correct permissions. AM does not allow for the same controls as an IAM system.
PAM
On the opposite end of the spectrum, privileged access management (PAM) restricts access and privileges as much as possible while still allowing users to perform their jobs. It can be used in conjunction with IAM for greater protection.
Compliance and Standards in IAM
Many regulatory compliance agencies require detailed documentation defining the policies and protocols an organization sets in place to verify users, create rules around managing access, auditing schedules, and much more. Audit activities increasingly drive enterprise access management projects and compliance reports are a central component of these efforts.
A good enterprise identity and access management solution can help you automate reporting by scheduling detailed daily activity information and sending it directly to the appropriate compliance agencies. With an automated solution, you can minimize the effort needed to go into ensuring compliance.
How to Choose an IAM Solution for Enterprise
Organizations of different sizes sometimes need different enterprise access management tools, depending on the amounts and kinds of information they handle, along with compliance requirements. However, a good IAM solution will provide standard enterprise user access management features. Here’s what to look for in an IAM solution:
Greater Control
Good enterprise identity and access management software should quickly automate the security process while also granting IT professionals the level of control they need to modify access rights. Additionally, IAM solutions should come with capabilities for a central directory toautomatically sorts employee job titles, identifiers, and locations to the levels of privilege needed to perform their duties without granting more access than they need.
Better Monitoring
Many organizations experience privilege creep, or the slow increase of access levels to users who do not need the access. IAM solutions should come with features that help combat privilege creep, including easy tools for managing individual requests around information and establishing regular review processes to stop users from accumulating non-essential rights.
Increased Flexibility
While it is essential for enterprise identity access management tools to provide security, IAM systems also offer flexibility. These tools must include the ability to grant specific privileges to established groups. IAM systems should also allow admins to easily modify privileges since sometimes employees with the same job titles in the same building require access to different information to perform their duties.
Easier Reporting
The goal of enterprise access management goes beyond easily granting permissions and protecting data, organizations also need to regularly audit and report the steps they are taking to protect data. That’s why SolarWinds® Access Rights Manager (ARM) was designed with simplifying enterprise access management in mind. ARM allows users to schedule detailed user activity reports and send them directly to auditors in order to satisfy GDPR, PCI, HIPAA, and other compliance requirements. Reports can typically be generated in just a few clicks.
Access Rights Management Software Options
SolarWinds ® Access Rights Manager
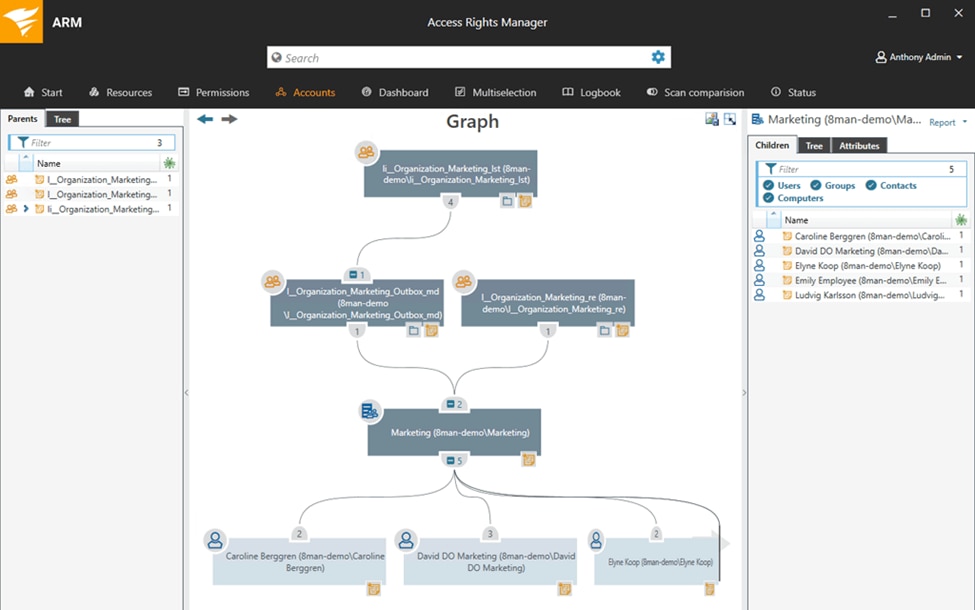
This is a comprehensive, dedicated tool for managing and auditing access rights. It’s useful for Active Directory and Azure AD user provisioning purposes, making it simple to onboard, adjust, and terminate user accounts. You can use role-based templates which are especially useful for bulk action. With ARM, you also get greater visibility into user configurations, with alerts and reports that help you stay on top of threats and prevent data loss. The streamlined reports are helpful for demonstrating compliance with various regulations.
ManageEngine AD
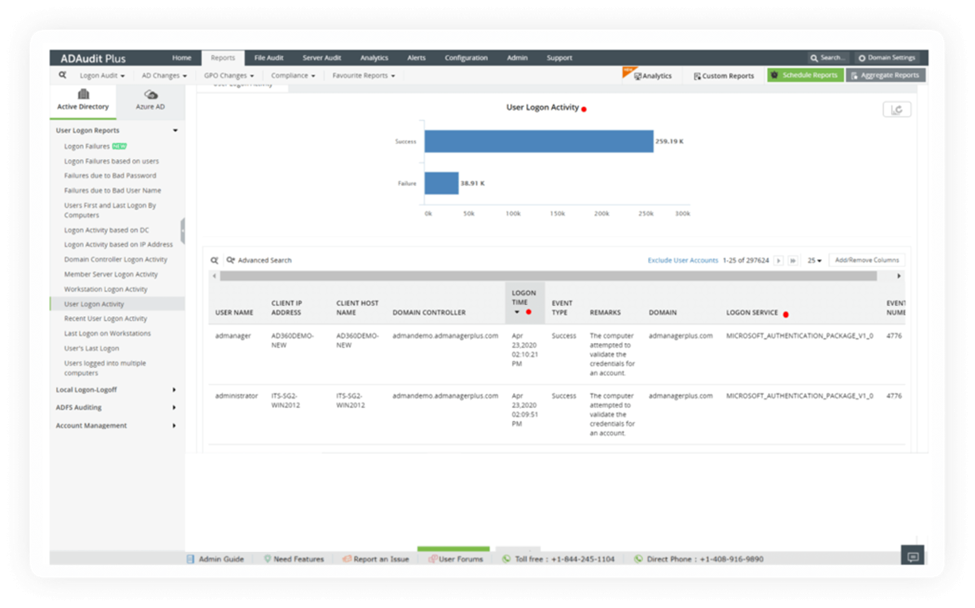
In the Windows Server environment (or Linux), you can use this tool for easy Active Directory management. You can easily access and audit your Active Directory, whether on-premises or cloud-based, providing insight into file systems, email, and other resources. As a management tool, you can adjust access rights easily. This tool also offers user templates so you can easily create user accounts and user groups, as well as carry out bulk actions.
Paessler PRTG Active Directory Monitor
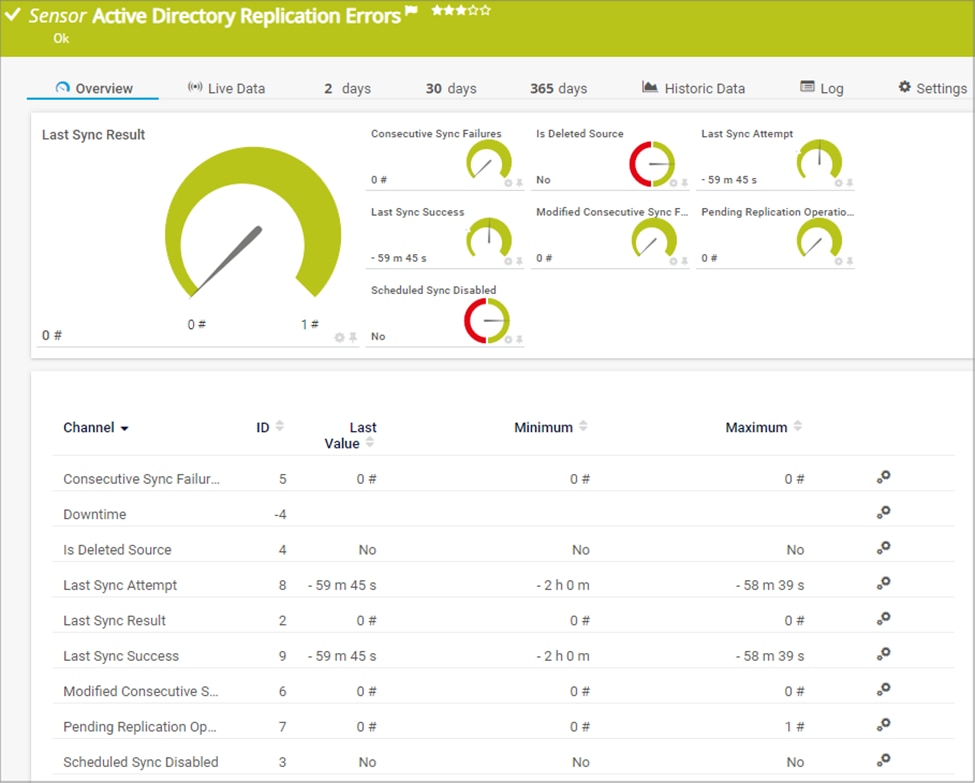
This is a well-known tool for comprehensive network monitoring and it also offers a useful sensor as an Active Directory monitor. Note that it’s not a management tool, just a monitoring tool for viewing and auditing AD. That being said, it’s still useful as you keep an eye out for database errors. Various faults and failures can easily occur and cause problems with access. With PRTG you get alerted to issues so you can take action. If you’re using Paessler PRTG for other purposes, this Active Directory Monitor is a useful addition.
N-able Passportal
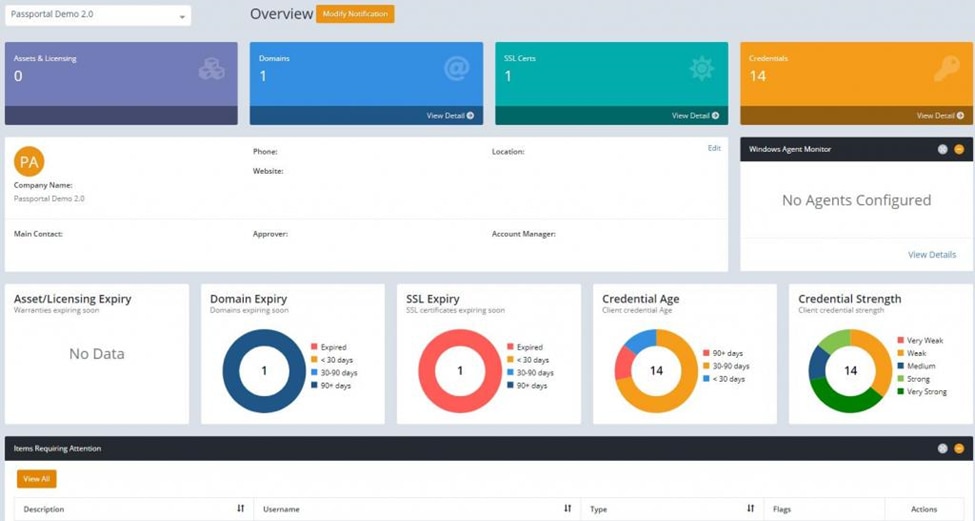
Managed service providers can benefit from this cloud-based tool, making it possible to control access rights for clients even over multiple sites and cloud servers. This tool works for AD, Office 365, LDAP, and Azure, and offers an encrypted password vault. It’s a useful point of centralized control that makes it easy to draw together and make changes in various access rights systems, across your client base.
Atera
© Atera Networks Ltd. 2022. All rights reserved
This is another cloud-based MSP tool, offering you the capability to monitor and back up access rights management systems that include Active Directory. It offers automation features to help MSPs manage various client services more easily. For instance, you get a password tool that lets you more easily handle access for clients. Atera is set up online and as a mobile app, making it convenient and flexible for MSPs.
Takeaways for IAM Solutions
Adopting an enterprise access management solution should combine peace of mind with ease of use. That’s why SolarWinds Access Rights Manager not only allows you to quickly manage groups and control privileges, it also immediately alerts you when accounts are misconfigured, or unauthorized activity occurs, so you can respond with precision. Click here to start your free trial.
