The security of network devices is vital to network security, but it’s easily overlooked when setting up network components out of the box. It’s common to purchase network devices and install them without customizing settings to suit the individual business situation, which can leave organizations open to security risks and network vulnerabilities. The importance of network device security configurations should not be underestimated, nor should the risk profile of network devices more generally.
This guide will look at five of the most common network devices and the role they play in security, along with the role network device security plays in the larger IT risk environment. I’ll then go through six best practices for assessing risk and setting up your network devices to be as secure as possible, including the use of software like SolarWinds® Network Configuration Manager (NCM) to ensure optimal configuration.
Skip to read more about NCM >>>
Common Network Devices and Risks
Large enterprise networks consist of numerous devices. Properly managed, each of these plays a role in shoring up vulnerabilities and securing your network against threats. Below are five common network devices and how they affect the security of your network.
Firewalls
The first line of defense is your firewall. The firewall isolates your network from external actors and blocks malicious connections between your network and other networks. You can implement a firewall as part of another solution, or as standalone protection. Some devices, including routers and switches, have firewalls built in.
There are two primary ways you can operate your firewall:
- Block everything except permitted traffic (whitelisting).
- Block nothing except suspicious traffic (blacklisting).
Both approaches have their place. Your organization will have to decide which one is more appropriate for your circumstances and risk of breach.
Routers and Switches
Your routers and switches are another important part of your network security setup. Routers play a part in delivering and directing network traffic, which means any vulnerabilities in the router can also be a point at which an intruder gains access. Switches also need to be carefully monitored, as they connect the devices on your network to the network itself through packet switching.
Proxy Servers
The proxy server acts as a barrier or intermediary between the web browser on your computer and the server at the other end of the internet connection. The proxy server can help disguise your IP and can block malicious traffic or malicious connections attempting to come through the browser.
Intrusion Detection and Prevention Systems
An intrusion detection system (IDS) catches anything that gets through the firewall. An IDS will flag when an intruder has accessed your network and provide helpful information to prevent another intrusion the next time someone attempts the same thing.
Alternatively, or in combination with an IDS, you may want to use an intrusion prevention system (IPS). As an active response tool, IPS implements responses to intrusions—for example, blocking access as a firewall would.
Unified threat management (UTM), meanwhile, is carried out by a system with the above functions in a single package.
Antivirus Software
Finally, if a malicious file or executable gets through all of the above defenses, antivirus or anti-malware software can detect malicious code or strange logs or alterations to files. These tools will then alert you before you accidentally run the malicious file and infect your system.
Network Device Security Best Practices
To prevent the loss or misuse of data, data breaches, or unauthorized access, implement the following network device security best practices.
Conduct an Inventory
First, ensure you’ve conducted a thorough inventory of all your network devices and the security measures you’ve implemented for each one, including computers, routers, switches, printers, and mobile devices. As new devices are purchased, or devices are sold or retired, the inventory needs to be updated.
Performing this process manually can be time consuming and costly. In most cases, it’s better to use a tool that can scan your network and determine what devices are connected.
Determine High-Risk Devices
Next, you need to figure out which of your devices carry the highest risk, so you can identify routes through which a malicious actor may try to access your network. Devices with a particularly high-risk or containing sensitive information—such as servers and databases—should be flagged, with additional security applied.
In addition, look at the access permissions set up for each device and for each part of your network. The aim here is to determine whether there are accounts with broad access, or whether a particular device is very permissive in regard to the kind of traffic it lets through.
Identify Vulnerabilities for Devices
Among those high-risk devices, each will have its own vulnerabilities that need to be identified and managed. When performing regular updates on devices, for example, you may determine a device or type of device has a vulnerability needing to be patched. Setting up your network to give this device extra protection in the meantime can help proactively prevent breaches.
You should deploy an update manager to check whether any devices have vulnerabilities in need of patching, and to identify devices that have reached end of life and need to be replaced. If anything is no longer supported by the manufacturer, this is a potential vulnerability.
Apply Configuration and Management Tools
The easiest, most effective way to handle network device security management and network device security configurations is by using an appropriate professional tool. Using a tool takes pressure off your IT administrator, as performing network configuration and security tasks manually can take a lot of time and effort that could be better spent doing other things. In addition to being time-intensive, the manual review of security logs can be inaccurate if patterns of unusual behavior are not spotted, or if problematic events are missed. It’s much more efficient to use a tool to automate large sections of the process, with greater accuracy, and capable of quickly analyzing large amounts of information using pattern recognition.
My recommendation is SolarWinds Network Configuration Manager, which has several features ideal for network administrators looking to efficiently and effectively handle security issues. First, NCM can manage rapid changes across complex networks, with the ability to automate and streamline repetitive tasks and standards maintenance. This helps free up IT team resources to focus on more proactive troubleshooting or handling of issues.
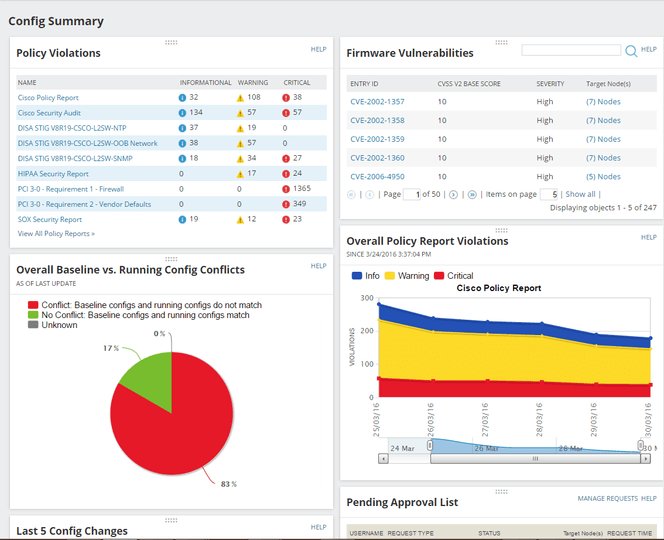
You can use NCM to deploy standardized configurations, and to detect out-of-process changes to your network performance or network devices. It’s integrated with the National Vulnerability Database, which equips it to procedurally identify potential vulnerabilities before your IT team has spotted them.
In addition, NCM includes real-time network configurations change detection and notification, so you’re notified as soon as a configuration change is made. The notification includes information on what was changed, and who made the change. You can also easily see whether the configuration change was tied to any network performance issues or security problems.
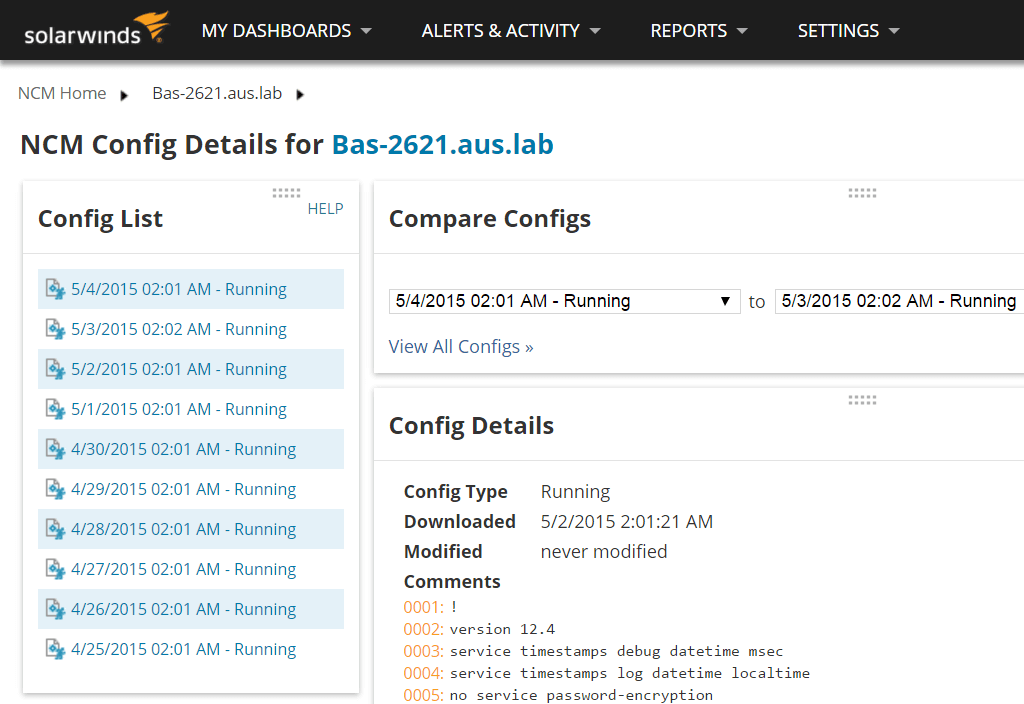
For all configuration changes, you can apply approval. By enabling the config change approval system in NCM, you ensure no device uploads are executed unless approved by an administrator. You can also use NCM to lock down devices if you spot unauthorized access or changes.
When you need to make a configuration change yourself, NCM can automatically deploy individual or bulk changes across multiple devices to save you time. The NCM device configuration tool also helps you establish a running inventory, as it shows you which devices are connected to your network, their configurations (for both hardware and software), and when they’re reaching end of life.
Notably, you can link up NCM with other SolarWinds products, including SolarWinds Network Performance Monitor (NPM), through the Orion® Platform. The Orion Platform allows you to integrate different SolarWinds tools and use them as one larger solution. Combining NCM with NPM allows you to detect more network faults, while still keeping an eye on configurations. With this kind of broad and continuous monitoring, you can keep your network secure and reduce downtime so end users aren’t affected.
You can download a free trial of NCM, good for up to 30 days.
Report, Review, and Audit
Finally, it’s essential to perform regular reviews of your devices. Whether you implement NCM or another solution, it should be capable of generating reports. These reports should analyze whether your device security plans are working as expected. You should review these regularly, along with the results and monitoring outputs your solution is producing. In addition, regularly review your device inventory, security measures, and configurations.
Furthermore, if you’re subject to any compliance obligations, such as data protection laws, you should run reports to verify your network device security measures are up to standard.
Maintaining the Security of Your Network Devices
The security of network devices like firewalls, routers and switches, and proxy servers is extremely important to the success of any organization. Without good security measures in place, you risk significant breaches of data, loss of data, productivity interruptions, and reputational damage. Following the above practices, including the use of high-quality tools such as SolarWinds Network Configuration Manager, is key to maintaining your network device security, which in turn supports the health and safety of your network as a whole.
