If you’re an IT admin responsible for managing your organization’s critical assets in an enterprise network, Active Directory (AD) should be your number one tool. Whether you’re running a small network or a large one, managing a slew of assets, users, and permissions can be a tedious ordeal. AD facilitates and streamlines this process. A Microsoft software used to manage computers and other hardware on an organization’s network, Active Directory enables IT teams to organize users into logical groups and subgroups, and to allocate access control for each group with ease.
When properly monitored and managed, Active Directory is an invaluable tool for network administrators, especially as an organization grows larger and begins adding more users and resources to their networks. It’s also enormously helpful in demonstrating industry compliance. In this article, I’ll offer an overview of the important concepts IT teams need to know about Active Directory, then a review of the best tools to keep your AD networks organized. These all have free trials, so I recommend giving them a shot—especially my top picks: SolarWinds® Access Rights Manager and SolarWinds Server & Application Monitor.
Feel free to jump ahead or continue reading:
What Is Active Directory Forest?
Understanding Active Directory Structure
AD Objects
AD Domains
AD Forest vs. Domain
Single vs. Multiple Active Directory Forest
Understanding Active Directory Replication
The Benefits of Active Directory Replication
Active Directory Replication Topologies
Best Tools for Managing Active Directory
SolarWinds Access Rights Manager (ARM)
SolarWinds Server & Application Monitor (SAM)
Paessler PRTG Network Monitor
ManageEngine AD Manager Plus
What Is Active Directory Forest?
Microsoft designed Active Directory to store and manage information about objects and users on a network. In a way, it can be thought of as a telephone directory for network resources—when an IT team wants to access information about a computer, server, hardware resource, shared file or folder, or group of users, they look it up in AD.
IT teams use Active Directory to arrange, manage, and control network access and permissions, as well as to arrange network objects into logical, hierarchical groups, so admins and managers can better oversee and control their assets. Active Directory is also used to authenticate and authorize users, so only privileged users can obtain access to an organization’s most sensitive data and resources.
Understanding Active Directory Structure
Active Directory is a database management system. To organize its data, it uses a hierarchical structure made up of objects, domains, trees, and forests. Understanding these components of Active Directory structure is vital to effective AD management and monitoring.
AD Objects
In Active Directory, objects can best be understood as physical network entities—AD objects include computers, servers, hardware resources, shared files and folders, and even end users. To make these entities more easily identifiable, Active Directory will assign unique attributes to an object. For example, Active Directory will define a user by name, location, and department. With the added granularity of these attributes, IT teams are better equipped to track and manage important network objects. They can even create AD groups based on certain attributes to better manage a company’s resources or employees.
An Active Directory object can be categorized as either a container object or a leaf object:
- Container objects: Container objects can contain other objects. Examples of a container include folders and printers.
- Leaf objects: Leaf objects, on the other hand, only account for themselves. Examples include users and single files.
Beyond these categories, certain objects are designated as security principal objects, which can be assigned permissions or special authentication rules. IT teams use a unique SID (security identifier) to identify each security principal.
AD Domains
In Active Directory terms, a domain is an area of a network organized by a single authentication database. In other words, an Active Directory domain is essentially a logical grouping of objects on a network. Domains are created so IT teams can establish administrative boundaries between different network entities. There’s no limit to the number of objects you can add into an AD domain, and objects don’t need to be in the same physical location to be grouped together.
Active Directory domains are controlled by a tool called the domain controller. The domain controller acts as a domain authority, meaning it’s responsible for all Active Directory object permissions, authentications, modifications, and edits in a domain. AD domains are usually identified via a domain name system (DNS). Usually the DNS is the same as a company’s public domain name, although sometimes there are alternate subdomain names.
One of your first considerations when setting up AD will be whether to use a single domain vs. multiple domain Active Directory structure. It’s always advisable to use only the minimum number of domains necessary for your organizational needs. The simplest option is to limit the structure to a single domain, but this isn’t typically possible at the enterprise level.
In large networks, there might be dozens or even hundreds of Active Directory domains. To organize them in a manageable way, domains are put together into groups called Active Directory domain trees.
AD Forest vs. Domain
Enterprise networks with hundreds of users and thousands of network entities might have dozens and dozens of Active Directory trees. In such cases, IT teams will organize AD trees into groups called forests. Active Directory forests are the highest level of security boundary for network objects in the Active Directory tree and forest structure.
Within this Active Directory hierarchy, an AD forest is considered the most important logical container in an Active Directory configuration. This is because it contains all other users, domains, computers, group policies, and any other network objects of importance.
Single vs. Multiple Active Directory Forest
Although Active Directory may contain multiple domains and trees, most single Active Directory configurations only house a single domain forest. However, in certain situations, it can be advantageous to create multiple Active Directory forests due to a given network’s autonomy or isolation requirements.
In multiple forest ecosystems, information and data exchange can only occur within the confines of a single Active Directory forest. This can be a challenge to manage, so IT admins should know creating more than one forest can make Active Directory monitoring practices significantly more complex.
Generally speaking, it’s considered best practice to run only a single Active Directory forest, but if you need an added layer of security between your Active Directory domains, it’s wise to leverage a multi-forest ecosystem. However, this isn’t an automatic security fix—IT teams still need to manage and enforce permissions for every created Active Directory forest.
Additionally, IT pros might find multiple forests helpful if they’re installing Active Directory management software. With an additional forest, IT teams can leverage an isolated copy of their AD system to test and tweak the configuration of their new software before rolling it out on a live network, minimizing the risk of the software affecting day-to-day operations.
What’s more, multiple forests can be helpful in the case of large company mergers and acquisitions, especially when a company buys another business already using Active Directory on its network. Depending on the nature of the transaction, it can sometimes be easier to create an entirely new forest for the newly bought business, as opposed to migrating every user and resource over into your existing domains and trees.
If the acquired organization plans on operating under its current name even after the acquisition, chances are it won’t want to switch its domain name either. This means it can’t be integrated into your company’s existing domains and trees due to complications with the DNS. In such circumstances, an IT team can attempt to port the trees of the new division over to the existing forest, but this can quickly become complex.
Instead, leave the acquired network alone, and link the two Active Directory forests together by establishing a transitive trust authority. Although this solution has to be carried out manually, it can be effective. A transitive trust authority will extend the accessibility of resources, so the two forests can effectively merge on a logical level. This saves time and IT resources, which will likely already be stretched thin during a merger. IT teams can still manage the two Active Directory forests separately and let the trust link handle any mutual accessibility.
Understanding Active Directory Replication
To understand Active Directory replication, it’s first important to look at how Windows NT environments operated before AD. Windows NT environments were built as single master networks, meaning they used a single primary domain controller. This domain controller was the sole authority responsible for managing the domain’s database.
With this setup, the primary domain controller was responsible for replicating any and all changes made to the backup domain controllers. If the primary domain controller was unavailable or experiencing downtime for some reason, no changes would be made to the domain database, which meant data was at risk of being lost or unaccounted for. This made Windows environments significantly less reliable, since IT teams had to take many manual steps to continually ensure changes could be made to a domain database or else risk losing valuable information.
To mitigate these risks, IT teams needed a software to deploy more than one domain controller. If you were to deploy multiple domain controllers on a single network environment, performance would improve, since the network’s processing load would be spread to all domain controllers instead of a single primary domain controller.
The solution came with the introduction of Active Directory, which, unlike Windows NT environments, was designed to be a scalable, distributed, replicated database. This means AD operates with multiple domain controllers. Because every domain controller in an Active Directory ecosystem automatically creates a replica of the information it stores within its own domain, the entire AD system is more reliable than previous systems.
Accordingly, Active Directory replication is best understood as a guarantee that any information or data processed by any of the domain controllers is consistent, updated, and synchronized. Any changes made to a replica on one domain controller will automatically be transferred to replicas on an organization’s other domain controllers. This replication process enables IT admins to modify any Active Directory database from any domain controller, and to have these changes be automatically replicated to all other domain controllers in the same domain or tree.
The question then becomes, what information is replicated in Active Directory? Some actions in AD are replication triggers, meaning when they occur, replication automatically happens. For example, when an object is created, deleted, moved, or changed, it will be replicated.
The Benefits of Active Directory Replication
Replicated domain controllers have many security benefits. Crucially, if one domain controller becomes damaged or goes down, the IT team can more easily replace all the original records it stored by copying its database to another site.
What’s more, if a threat actor breaches valuable credentials from users on your organization’s network, they may try to change the permissions held in the local domain controller to exfiltrate higher privileges. If higher privileged credentials are compromised, your network’s sensitive data is significantly more at risk, since these users tend to have access to the most sensitive data. With replication, those changes can more easily be mitigated or dealt with once they’re spotted.
Additionally, having access to an ongoing comparison of an organization’s domain controller databases offers IT teams valuable security monitoring capabilities. Active Directory replication can also help your IT team eliminate a compromised account from your network altogether.
On the flipside, if you want to restore an original database and roll out updated records, it’s essential to run regularly scheduled system sweeps and integrity checks.
To get the most out of your replication, you need to implement good management policies for the network managers tasked with operating Active Directory. The increase in local domain controllers opens the door to security threats, creating more opportunities for bad actors to steal or alter data before being detected and locked out; security protocols should always be followed to avoid these risks.
Coordinating copies between domain controllers can quickly become complicated and time consuming, thus making it difficult to carry out Active Directory monitoring manually. It’s important to invest in automated tools to ensure your domain controllers and their replicas are all monitored.
Active Directory Replication Topologies
Replication traffic travels between domain controllers through a route known as the replication topology. There are four fundamental replication topologies. When deciding which to implement, you’ll want to consider the physical connectivity of your network.
- Ring Topology: In ring topologies, every domain controller has two outbound and two inbound replication partners. With this configuration, there are never more than three hops between domain controllers on a single site.
- Hub and Spoke Topology: The hub and spoke topology is defined by the existence of one or more hub sites using slow wireless area network (WAN) connections to connect to spoke sites, while the hub sites connect to each other with fast WAN connections. This topology is most commonly implemented in enterprise environments where scalability is paramount, and redundancy isn’t as highly valued.
- Full Mesh Topology: Full mesh topology is typically used in smaller organizations where redundancy is of the utmost importance and site availability is limited. However, this topology is costly and not easy to scale.
- Hybrid Topology: A hybrid topology can be a combination of any of the topologies outlined above.
Best Tools for Managing Active Directory

Managing your Active Directory authentication system can be an incredibly difficult process, especially when you’re dealing with large numbers of domains, trees, and forests. It’s easy to become overwhelmed if you attempt to do this manually, without the assistance of special, automated tools.
There are so many Active Directory tools on the market, it can be hard to choose the best one for your needs. I’ve tested many of the most popular solutions out there and assessed their strengths and weaknesses to narrow down the field. Below are my top picks for the best Active Directory management solutions.
The best Active Directory tool on the market is without a doubt SolarWinds Access Rights Manager. IT teams can install ARM on any version of Windows Server and immediately begin managing access rights across an IT infrastructure.
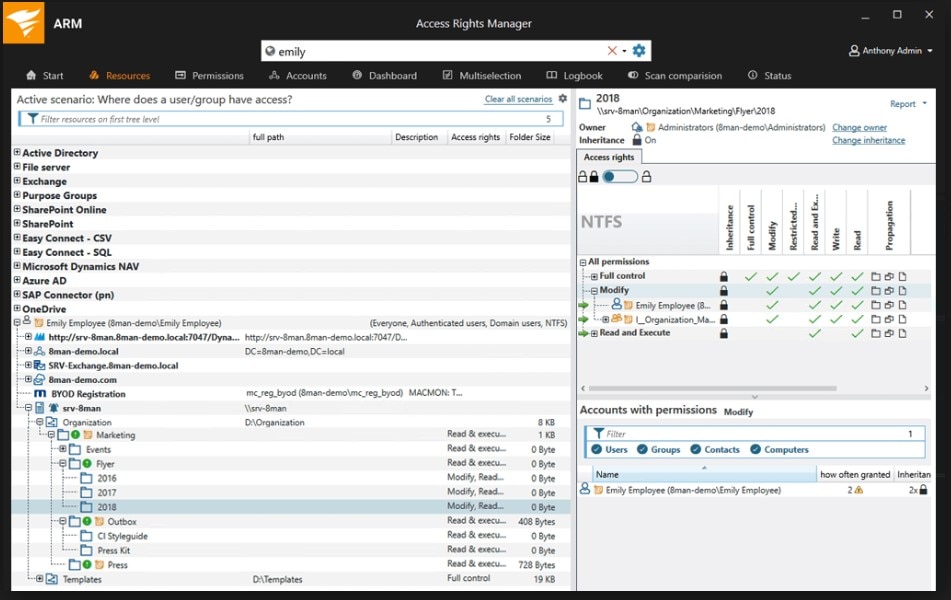
ARM has several automated tools to make access rights management easy. For one, it includes custom-delivered Active Directory reporting, enabling IT admins to generate ad hoc reports to see which users have access to what on their networks. The reports can go into detail to show when a user accessed a file or folder on the network.
In addition to helping IT teams analyze and monitor user access, the ARM Active Directory reporting tool can be leveraged to generate preconfigured compliance materials for a myriad of industry formats—including GDPR, PCI, and HIPAA. These reports can be automated and scheduled ahead of time.
Additionally, IT teams can use ARM to protect their organizations against data loss and potential security breaches with the help of automated monitoring. When ARM is installed in your infrastructure, it will get right to identifying user accounts with insecure configurations that might signal credential theft or authorization misuse. And with ARM’s ability to provide IT admins with a full audit trail of all permissions and access-level changes, cybersecurity investigations can be completed in a matter of minutes.
Finally, ARM enables IT teams to automate the entire Active Directory user provisioning process with the aid of role-specific templates. These templates ensure users conform to security policies by commissioning access privileges via the principle of least privilege.
Server & Application Monitor is another excellent tool from the team at SolarWinds. In addition to being a full-stack server monitoring software, SAM operates as a tool for Active Directory management. Users can easily monitor and troubleshoot any Active Directory performance issues with a myriad of automated features.
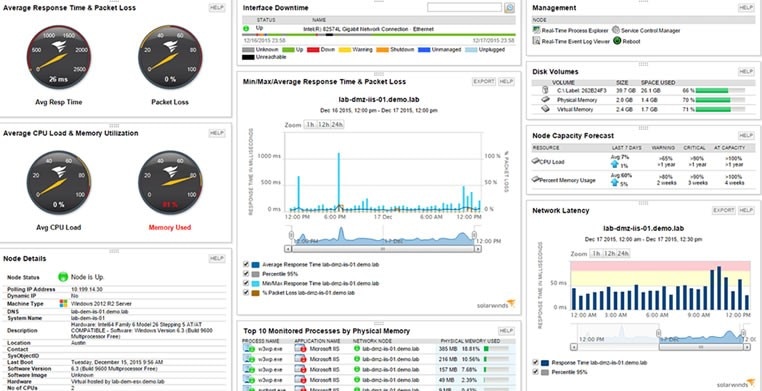
With SAM, users can leverage the Replication Summary view to make sure all replications between domain controllers are successful. This allows IT teams to quickly identify replication status and drill down into the domain controller replication process. With a full cart of metrics, IT teams can glean insights into the progress and success of different configurations, AD schemas, and more.
In addition, SAM includes a Domain Controller Details widget, so IT teams can review domain controller roles and make changes as needed. This tool provides a holistic view into the status and role of each domain controller on your network. IT admins can even view, search, and sort all seven Flexible Single Master Operations roles—from the domain name and schema master to the domain controller emulator and the infrastructure manager.
Beyond these features, SAM offers a resource for IT teams to view all Active Directory site details in real time. The Site Details tool allows users to drill down into each site, which means IT admins can obtain and leverage helpful information—from site link name to subnets and IP ranges—to quickly identify and solve any remote location Active Directory issues.
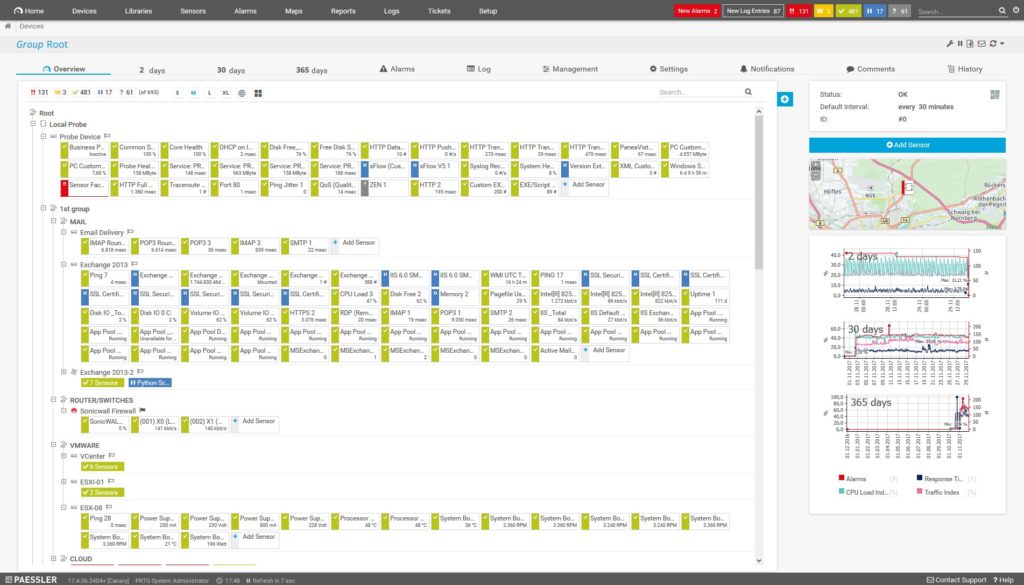
PRTG Network Monitor by Paessler operates as a bundle of tools, which it refers to as sensors. Some of these are Active Directory sensors, which can be used to monitor your AD systems. If you only activate 100 sensors, you can use PRTG for free. If you exceed 100 sensors, payment depends on how big your network is and how many sensors you choose to activate.
The PRTG Active Directory sensors can be used by IT teams to monitor their AD replication system. When used properly, they ensure the database is copied to all domain controllers on the network. Additionally, the tool’s Active Directory Replication Errors Sensor is designed to monitor different parameters during a directory’s replication period, to help ensure your domain controllers are synchronized and in line with one another. In the case of an anomaly or an error, an alarm will be sent to an IT admin.
What’s more, this solution can log employees’ network activity, which can offer network admins insights into suspicious behavior or internal threats and is helpful in managing issues associated with logged-out or deactivated users.
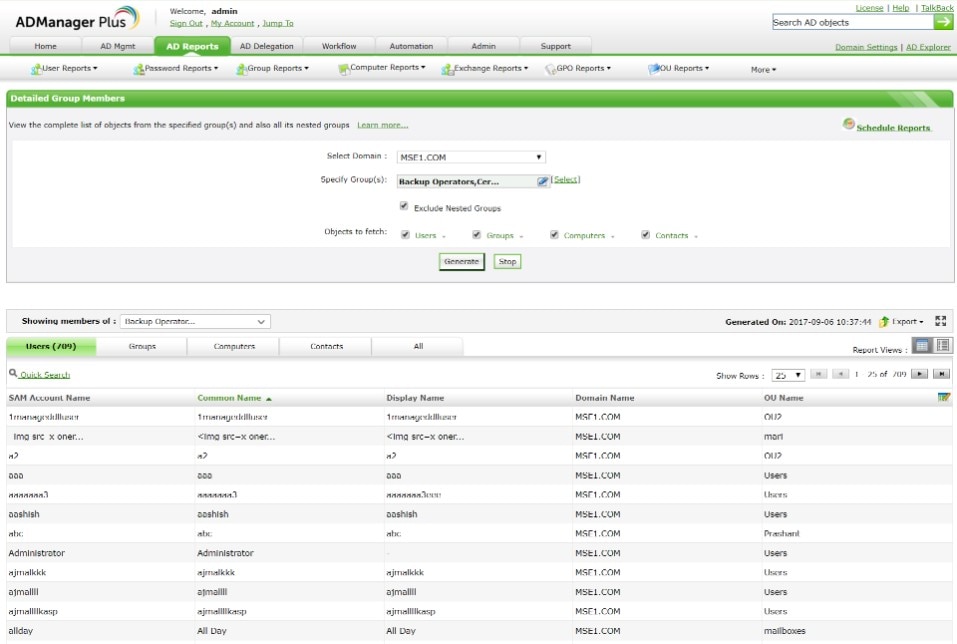
ManageEngine has a wide variety of network monitoring solutions, one of the best of which is its full-service Active Directory management tool. IT teams can use AD Manager Plus to extend Active Directory into G Suite, Office 365, Microsoft Exchange, Skype, and their own internal network access rights.
The tool is neatly organized: it operates from a single dashboard, on which IT admins can easily view and monitor all Active Directory objects and groups, and provision users. In addition, I like AD Manager Plus for its robust reporting system. You can easily generate Active Directory reports on either a scheduled or ad hoc basis, and the tool comes with more than 150 preconfigured report templates, which goes a long way when you’re working to stay in compliance with industry regulators. ManageEngine can also generate specific reports for Active Directory users, logons, computers, passwords, and other objects.
AD Manager Plus comes with more of a learning curve than the other tools. Its user interface isn’t the most intuitive, especially when operating on mobile, and the lack of documentation makes it hard to deal with little bugs here and there. Users may also have a tough time tracking down a support team member to assist with more complicated inquiries.
