Active Directory (AD) is a battle-tested software many company administrators use as a standard remedy for concerns about outsider access to data. But within AD, there are many types of security protocols to choose from. What if I don’t want to enable email access to my users, but instead I want my users to securely access and modify aspects of company data? How do I grant a manager greater access to the server than one of their subsidiaries?
In this guide, I’ll describe everything I know about security groups, how to create groups in Active Directory and the best tools (like my personal favorite Access Rights Manager) you can use to better manage and monitor user permissions in AD.
What Is a Group Within Active Directory?
What Is a Distribution Group vs. Security Group in Active Directory?
How to Create a Security Group in Active Directory
Why Do Companies Create Security Groups in Active Directory?
Risk Control With Security Groups
Managing Active Directory Security Group Permissions
What Is a Group Within Active Directory?
Active Directory is a Microsoft program used to sort users into different groups. This is a centralized way for a company to manage its computer accounts and grant access to company data to its different users. In terms of AD, a group is a collection of users who have special access to company resources through either a Security Identifier (SID) or a Globally Unique Identifier (GUID). SIDs are commonly used for individuals to access company resources, while GUIDs are a broader group access tool. I can create several types of groups on AD. For example, it’s possible to form a group comprised of individual users, or a global group (composed of all individuals sorted under a particular title, like “Manager”), or a domain local group including all members of a domain.
What Is a Distribution Group vs. Security Group in Active Directory?
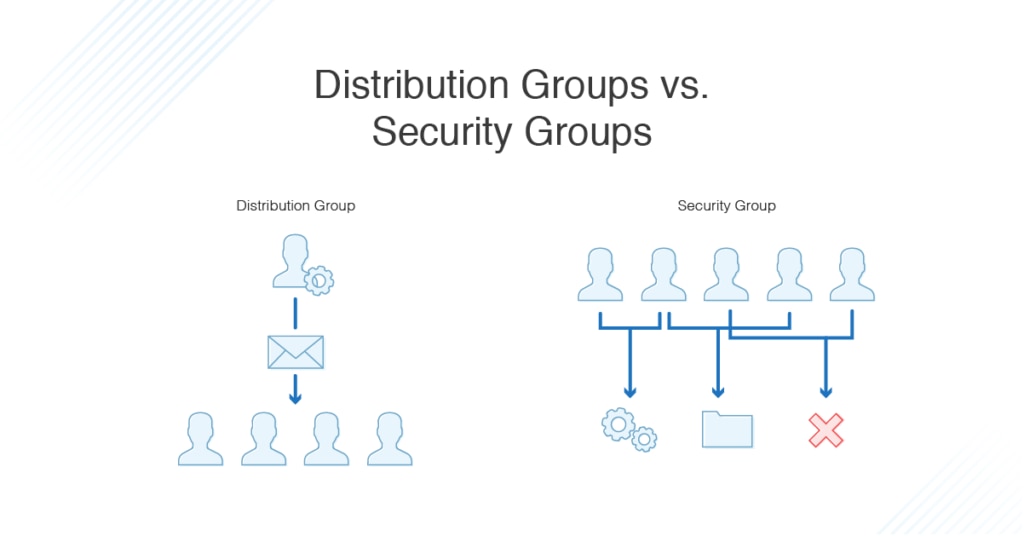
There are two main types of groups AD deals with distribution groups and security groups. Security groups offer many more functions and greater data access than distribution groups, and that’s what I’m focusing on today. But, to understand AD, I first need to explain the difference between these two varieties.
The most essential aspect of a group is whether it’s a security group or a distribution group. If my groups are intended for email distribution or other types of one-way notifications from the central controller, then they’re coded as distribution groups. But if I want my users to access and modify data, I have to code these groups into a specific, more complex category—they now must be security groups. Security groups are divided into the same general categories as distribution groups (i.e., individual, global, domain local, etc.) but the central AD controller must pay special attention to security groups to manage the security risks from granting many individuals access to modifying company data and resources.
How to Create a Security Group in Active Directory
Creating a security group within Active Directory is fairly straightforward—the more complicated part is deciding how you’ll organize users across your network to allow necessary access without compromising security. To create a security group, do the following:
- Within Active Directory, it’s simple to choose New and click Group
- There you can name the new group, choose Universal for Group Scope, and Security for Group Type
- Once the group is created, you can find the Members tab within Properties, and click Add
- You can then add the users you’d like to the Security group
Why Do Companies Create Security Groups in Active Directory?
Security groups are a useful tool for managing what users hold access to what data, and for establishing different levels of security for different types of users. For example, using AD, a company can establish a security group labeled “Managers” which enables all designated managers to submit their monthly data to HQ, or to submit data for their associates, other associates shouldn’t be able to modify. You can also establish a security group called “Associates” to grant lower-level data entry access to designated associates.
Active Directory also allows a company to modify the status of group members whenever you want. With a quick visit to the AD portal, you can change the parameters of access delegated to a particular group. You can easily move a user from the Associate Group to the Manager Group or remove a user from groups altogether. A user’s SID/GUID will only give them the access permissions of the group to which they belong.
A useful feature of AD security groups is their ability for self-sufficiency. Individuals beyond the IT team can control the parameters of a group. This takes a major burden off IT teams and can free up lots of time and money. When members of a security group can define their own destiny, they can modify their group to make the most sensible company decisions.
The issue with this is many group managers might not have the sophisticated IT literacy needed to modify a program like AD.
To allow groups to easily manage their own affairs, I recommend a program like Access Rights Manager (ARM) from SolarWinds. With the click of a button, you can delegate group members to manage their group’s access parameters and monitor user compliance.
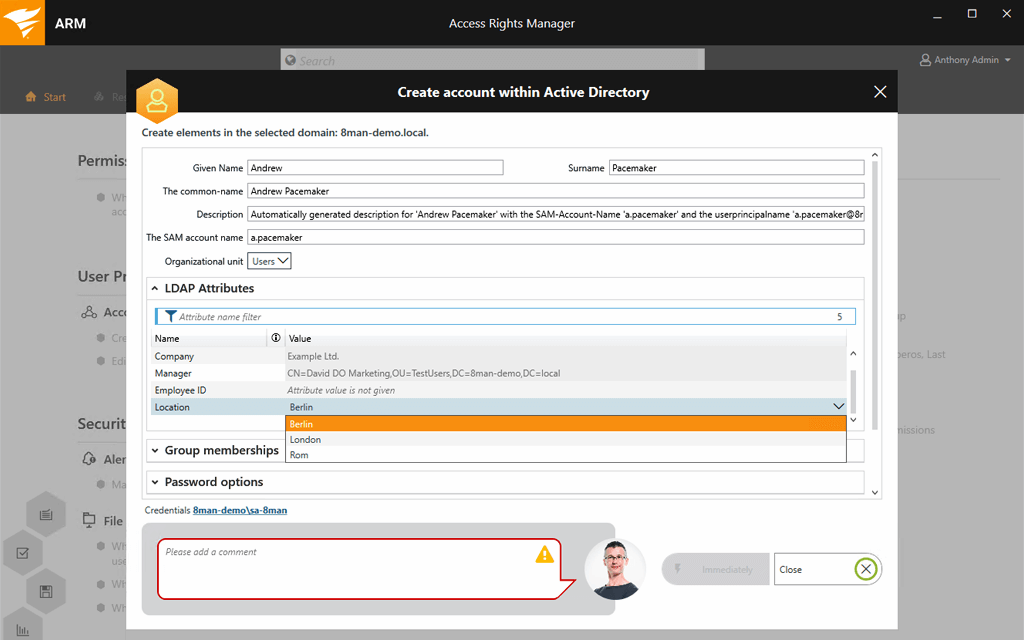
With a program like ARM, security groups can keep track of their own levels without requiring more work for the IT team. Designated users can provision and take away access to security groups without a middleman.
Risk Control With Security Groups
For cybercriminals, user logins can be a major target. Whenever a company delegates its resource management to users in security groups, there’s bound to be a risk. I need to let my company’s security groups submit data and access private company information, but one security breach from a trusted user can incite a major company meltdown.
This is another reason why it’s useful for the data owner to easily manage their own access rights. SolarWinds® Access Rights Manager comes with a highly intuitive interface allowing centralized access to a security group’s safety threats. ARM also delivers Active Directory user access reports to ensure user compliance, and it provides a robust audit trail in case there’s any aberrant user behavior.
Another useful measure you can take to minimize security risk is to monitor the activity of every application on the server, whether the applications are on cloud space or in virtual machines. Cybercriminals pose a major threat to any twenty-first-century company, and, though security groups can be important for success, companies also need a firm way to keep tabs on what activity is always happening in their security group.
For this, I recommend SolarWinds Server & Application Monitor (SAM). It typically only takes a few minutes to get started, and it’s surprisingly easy to customize.
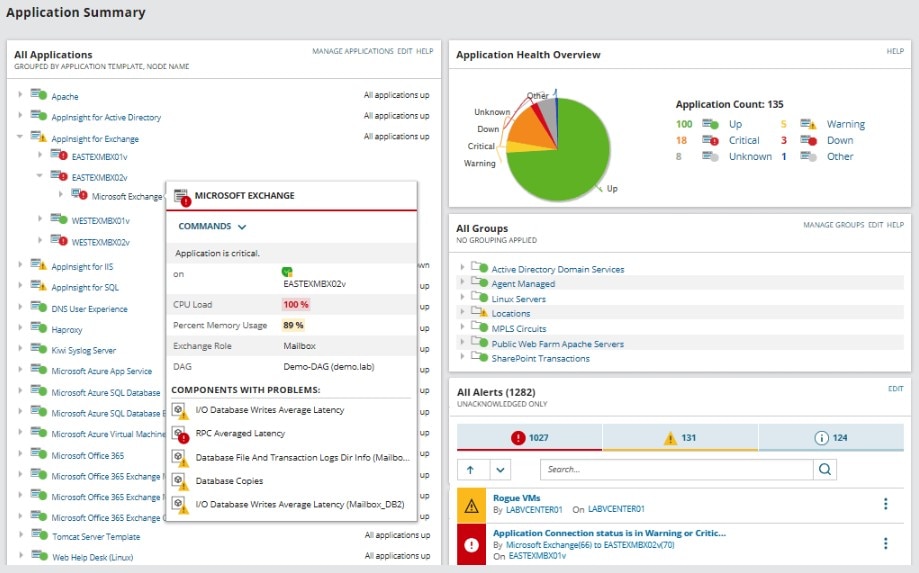
SAM helps me visualize all application activity on my server, and it offers a dashboard where I can analyze IT data with easy-to-use visuals. SAM even monitors my server capacity to ensure I’m not pushing the boundaries of storage on my server.
Managing Active Directory Security Group Permissions
Nobody wants to worry about the security of their company accounts. Nearly every business, from large-sized companies to mid-sized businesses on a more local scale, must contend with the fact many independent agents have access to company accounts, passwords, data, and servers. In the wrong hands, this access could make the difference between smooth sailing and a corporate catastrophe. Make sure you understand security groups in Active Directory and have the best tools at your disposal to manage AD permissions. I recommend trying out a tool like Access Rights Manager free for 30 days to see if this level of insight can help improve your organization’s overall security posture.
