Since almost everything we own is connected to the internet, it’s time to take another look at cybersecurity. The nature of cybersecurity threats has changed since the early years of the web: cybercriminals are getting more sophisticated and less obvious. According to the Verizon Data Breach Investigations Report, in 2018, 74% of data breaches were caused by phishing attacks or fraudulent emails intended to get people to share sensitive information. And 83% of InfoSec professionals—the best of the best when it comes to cybersecurity—were victims of phishing attacks.
The odds of you being targeted by some kind of cybersecurity attack at least once, however minor, are good. Anyone can have a bad day and click on a well-disguised malicious link while they’re distracted. With all the personal information we store online, you can never be too careful. That’s why cyberthreat intelligence is so important.
What Is Cyberthreat Intelligence?
Types of Cyberthreat Intelligence
Why Is Cyberthreat Intelligence Important?
Threat Intelligence Tools
What Is Cyberthreat Intelligence?
In general, it refers to the information used by an organization to better understand past, current, and future threats. Threat intelligence provides the context necessary to make informed decisions about your network security, especially after an attack has occurred. Who’s attacking you and why? How much damage could they do in your system? Where are your system vulnerabilities? The answers to these questions are essentially the building blocks to a disaster readiness plan.
Cyberthreat intelligence is developed in a process known as the intelligence cycle.
- First, threat information is collected from reliable sources and processed.
- After that, you must analyze the raw data and determine whether the threat is real or a false positive.
- If you determine the threat is indeed real, then you must share the threat information with others through predefined internal and external channels. In a large enterprise, cyberthreat detection and protection is a group effort. Reaching out to others within your organization opens potential avenues you may not have thought of before.
- After you’ve figured out what steps must be taken to avoid the threat, integrate actionable intelligence into existing network security measures, incident response programs, and workflows.
- The final and most important step of the cyberthreat intelligence cycle involves analyzing your intelligence.
We call cyberthreat intelligence a cycle instead of a checklist because arming yourself against security requires constant vigilance and constant readiness to learn. Your job isn’t done once you’ve averted one crisis. Take what you learn from each cyberthreat analysis cycle and apply it to the next one. This extra step helps you better respond to threats in the future.
Cyberthreat intelligence isn’t a solution, but it’s critically important to creating one. If you have a working understanding of security threats before you step up to the drawing board, you’ll be better equipped to build a functional plan for securing your network.
Types of Cyberthreat Intelligence
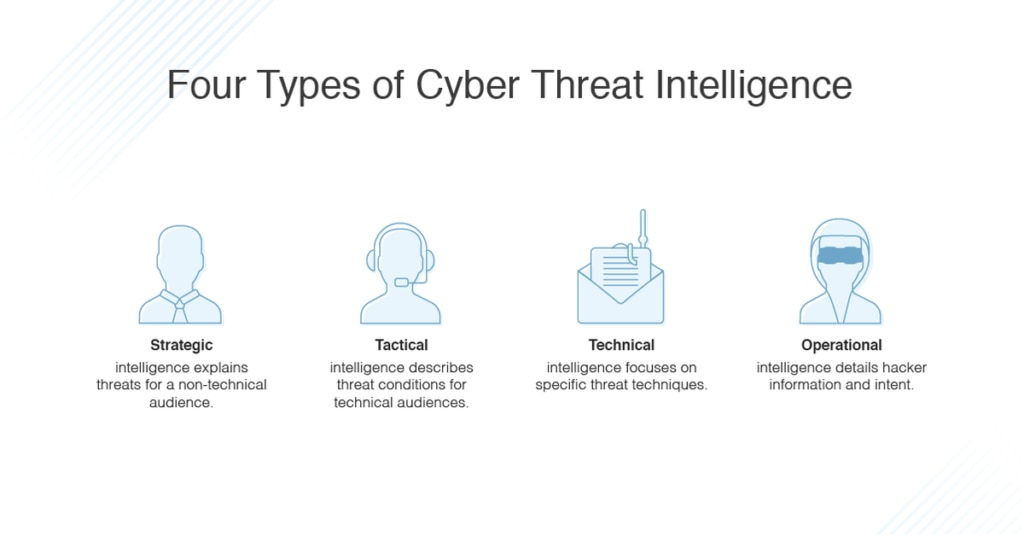
The four main types of threat intelligence are strategic, tactical, technical, and operational.
- Strategic cyberthreat intelligence is a broader term usually reserved for a non-technical audience. It uses detailed analyses of trends and emerging risks to create a general picture of the possible consequences of a cyberattack. Simply put, it asks the question: “Given our technical landscape, what’s the worst that can happen?” This information is often presented to high-level decision makers within an organization, like board members, so it focuses on broader impacts. Some examples include whitepapers, policy documents, and publications distributed within the industry.
- Tactical threat intelligence offers more specific details on threat actors’ tactics, techniques, and procedures, also known as TTPs. It’s intended for a predominantly technical audience and helps them understand how their network might be attacked based on the latest methods attackers use to achieve their goals. They look for Indicators of Compromise (IOCs) evidence like IP addresses, URLs, and system logs to use to help detect future data breach attempts. Tactical, evidence-based threat intelligence is usually reserved for security teams or the people in an organization directly involved with protecting the network.
- Technical threat intelligence focuses on the technical clues indicative of a cybersecurity threat, like the subject lines to phishing emails or fraudulent URLs. This type of threat intelligence is important because it gives people an idea of what to look for, making it useful for analyzing social engineering attacks. However, since hackers change up their tactics, techniques, and procedures frequently, technical threat intelligence has a short shelf life.
- Operational threat intelligence helps IT defenders understand the nature of specific cyberattacks by detailing relevant factors like nature, intent, timing, and sophistication of the group responsible. Operational threat intelligence is where you get into secret agent stuff like infiltrating hacker chat rooms. Less experienced threat groups might discuss their evil deeds online, but the good ones probably won’t, so operational intelligence can mean playing the long game. Still, all facets of cyberthreat intelligence are necessary for a comprehensive threat assessment.
Why Is Threat Intelligence Important?
Cybersecurity threat intelligence is important for anyone who stores sensitive information on a connected device—which pretty much includes everyone. Even if you already have firewalls and other security measures in place, staying up-to-date on the nature of threats is critical for securing your systems. Large enterprises are especially vulnerable to cybersecurity threats because they’re so spread out, meaning the IT team may not know one of their departments has been hit until it’s too late. The varied nature of cyberattacks today makes cybersecurity threat intelligence and awareness essential.
Threat Intelligence Tools
As important as security threat intelligence is, analyzing all the raw data manually would take a long time, and you’d probably miss something. Luckily, there are security solutions currently on the market that can help with the task.
SolarWinds® Security Event Manager is a great piece of tech for detecting and responding to security threats in enterprises of any size. On the front end, built-in threat intelligence feeds automatically identify potential threat actors and alert you to their presence in real time. With automated incident responses you can configure SEM to automatically block IP addresses, kill applications, or disable accounts when a possible threat is detected.
Still, sometimes cyberattackers are successful and manage to get into your system. SEM makes post-attack analysis easy, with advanced search and forensic analysis options to help you unpack attacks for the investigative, response, or auditing purposes.
Main Takeaways
Cyberthreat intelligence is vital for everyone, but especially enterprises. Repeat the threat intelligence cycle often as part of network security best practices. Take advantage of tools like SolarWinds Security Event Manager to streamline threat assessment and response processes.
