Oracle databases are an integral part of modern technological infrastructure, and they provide the backbone for how many companies house their data and process online transactions. Because so much of an organization’s important or sensitive information is stored in databases, they’re valuable targets for cyberattacks and hacking attempts. Considering how the costs of data breaches and cyberattacks are on the rise, it is essential for organizations to take all possible steps to ensure the safety of their data.
No database management system is without security risk, but you can configure and manage your systems to help drastically reduce the problems you may experience. In this post, I’ll lay out some Oracle database security best practices, along with reviews of the best Oracle database security solutions I recommend using to help keep your systems as secure as possible. These practices and products will go a long way in securing your database and reducing what vectors of vulnerability can be used against you, a process is known as Oracle database hardening.
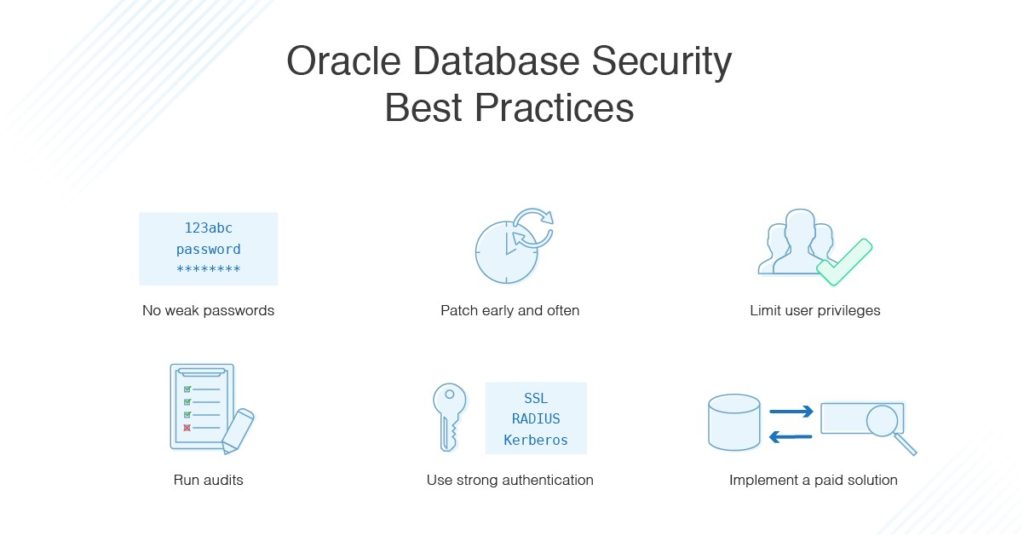
Oracle Database Security Best Practices
1. Stop Using Default Passwords
2. Patch Early, Patch Often
3. Limit User Privileges
4. Regularly Audit Your Database
5. Implement Strong Authentication Methods
6. Use Additional Security Tools to Manage Sensitive Data:
• Database Performance Analyzer
• Security Event Manager
• Patch Manager
• Database Firewalls
7. Educate Your End Users
8. Stay Vigilant
1. Stop Using Default Passwords
One easy Oracle security practice to put in place is to get rid of all default passwords. Easily hacked passwords or ones hackers can decode through a brute force attack are weak links in the chain of your database security. Imagine for a moment you’re a hacker—if you’re looking to harm or access a database, you’ll probably start with the techniques requiring the least amount of effort but with the maximum effect. Misconfigured MySQL databases have proven to be susceptible to attacks, so it’s vital for weak or default passwords to be changed to something more complex. Any stored passwords need to be encrypted. This is easy to do with Oracle Secure External Password Store, which creates a wallet file for protected credential storage.
Oracle Database features tools to help maintain password security, some of which are disabled by default, so you’ll want to make sure they’re enabled for strong security. One is the built-in checkpwd password cracker. Checkpwd scans users’ local password hashes and compares them against a dictionary file, thereby identifying accounts with weak passwords. You can also use SQL scripts to identify if any user accounts accessing your database still have default passwords.
Password verification is another feature available in Oracle Database, though the script running it is often disabled by default. However, it can be enabled by logging in to SQL*Plus with admin privileges. There are default password requirements, but these can be modified to suit the needs or specifications of your organization’s IT department.
Oracle Database also includes an account lockout feature, which can prevent cyberattacks by locking a user’s credentials after a certain number of invalid attempts. This reduces the chances of brute force attacks allowing hackers access to your database.
2. Patch Early, Patch Often
Keeping your software and applications up to date is another integral part of maintaining strong Oracle database security standards. In addition to installing the most current version of the database management system and keeping the host operating system up to date, you need to be vigilant about patching.
Oracle releases Critical Patch Updates four times a year—in January, April, July, and October—for its customers. These updates include fixes for Oracle products like Java security updates as well as information about the vulnerabilities the patches address. The information released in these updates has the unintended consequence of pointing hackers right to the identified vulnerabilities—and according to a Wallarm report on the state of network security, it can take as few as two hours for hackers to exploit those weaknesses in organizations slow to install the patches to their Oracle database. Advanced security professionals insist on applying patches immediately for this reason. You can prepare for scheduled updates and view security alerts on the Oracle website.
3. Limit User Privileges
They say it’s better to ask forgiveness than permission, but this doesn’t hold true in data security circles. The preferred approach is to prevent and stave off security issues in the first place, not to fix or cure the harm a breach might cause. One way to do this is to limit the privileges assigned to each user account, granting solely those privileges necessary for the user to be able to carry out the tasks their job requires. This prevents users from gaining access to applications or tools they don’t need, and from making unauthorized additions, edits, or deletions to information stored in the database.
Since countering internal threats is one of the more challenging aspects of Oracle security practices, it’s better for a user to have to ask for an administrator’s assistance than to give a user excess privileges and have them do something malicious—whether their actions are intentional or not. It is also good practice to regularly review user privileges and revise them where necessary, as this will help prevent users from accessing sensitive company information.
4. Regularly Audit Your Database
Another best practice for ensuring your sensitive information is adequately protected is to run regular database audits. By tracking and auditing the various changes made within your database—including modifications made to objects, roles, or permissions—the Oracle audit trail can help with the detection and resolution of security threats. You should also include logon attempts, both successful and failed, in an audit, to help you detect signs of a hacker attempting a brute force attack.
In an ideal world, you would want to audit all database activities, and applications can do this for you—more on that below. Crucially, a good software solution will collect and correlate log data for centralized auditing. By centralizing audit data, you streamline the process of running reports, which can reveal potentially problematic long-term patterns that a more granular, minute-by-minute analysis might not.
5. Implement Strong Authentication Methods
In distributed environments like Oracle Database, having a robust user authentication system in place is key to maintaining security best practices. Oracle Database supports the use of third-party authentication protocols and can be configured to incorporate them. Options like Kerberos, Secure Sockets Layer (SSL), and Remote Authentication Dial-In User Service (RADIUS) offer industry-standard authentication protocols for database access and securing network connections. Integrating one of these options into your Oracle Database setup will help keep out bad actors and ensure the only people accessing your database are the people who should be doing so.
6. Use Additional Security Tools to Manage Sensitive Data
Data breaches can be costly—not only for an organization’s bottom line and reputation, but also for anyone whose information is stored in the compromised database. Personal data related to people’s health, intellectual property, or payment details needs to be treated extremely carefully to make sure this valuable information is protected.
Oracle Database is equipped with transparent sensitive data protection, which allows you to classify data table columns containing sensitive data—such as Social Security or credit card numbers—and to quickly search for these fields. Transparent sensitive data protection also gives you the capability to create policies to be applied to the specific data table columns to protect the sensitive data stored there.
While the free tools available are certainly useful, many don’t provide the same level of comprehensive protection and monitoring as paid options. If you have the budget for database activity monitoring tools, I strongly suggest you look into an application toolset to help streamline the process of maintaining Oracle database security best practices. Database activity monitoring tools allow you to track activity and changes made in your database in real time.
The Oracle Advanced Security paid upgrade includes database activity monitoring tools, including a data encryption tool to transform text data into unintelligible code requiring an algorithmic encryption key to decipher it. This makes it incredibly difficult, if not impossible, for anyone who happens to access the encrypted text to decrypt it.
Best Oracle Database Security Solutions
Third-party security solutions can help provide another layer of comprehensive insights into Oracle security. In particular, I find Database Performance Analyzer, Security Event Manager, and Patch Manager from SolarWinds incredibly useful in keeping my systems secure. They give you access to a full range of tools and features—many of which work automatically— to take a lot of the worry out of making sure your security countermeasures are functioning optimally.
Database Performance Analyzer employs anomaly detection protocols to alert you when behavior within the database is different than expected, which can sometimes be a sign of suspicious or unauthorized activity. The application uses algorithms that learn the typical behavior patterns of your database, and its lightweight monitoring system is designed to not affect load times.
Security Event Manager, meanwhile, combines SIM and SEM protocols to monitor both real-time network activity and historical data stored in log files, which can help prevent potential intrusions as they’re happening and identify long-term patterns of unauthorized or suspicious behavior. It also allows you to configure and personalize how you audit your Oracle database.
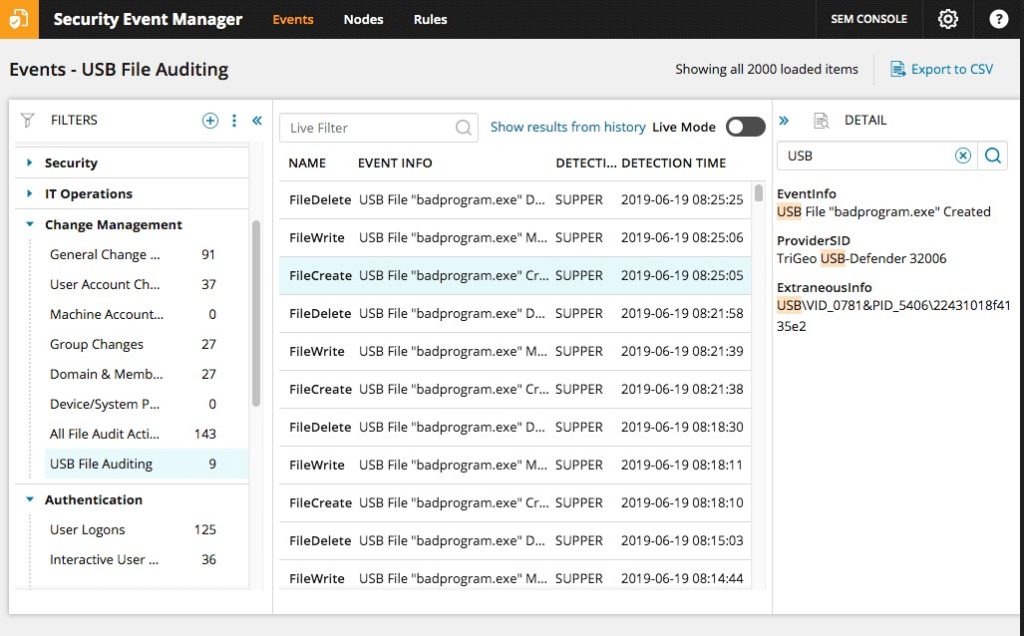
At the very least, you should be auditing database access rights, and Security Event Manager tracks and audits database logins and logouts, as well as changes made within the database. The application is designed to integrate with Oracle Database and comes with a “Recommended Oracle Audit” script to audit these essential categories, in addition to other metrics.
To support an effective patch management security strategy for databases, having a dedicated patching tool like SolarWinds® Patch Manager can make it easier to perform third-party patch management across thousands of servers and workstations at the same time, so they remain updated and compliant.
Patch Manager is designed to reduce the time it takes to patch physical and virtual Windows desktops and servers from weeks to minutes with pre-built and tested patches to ensure successful patch deployments for critical business applications like Adobe, Apple, Oracle, and more—no complicated scripting needed.
- Database Firewalls
In addition to third-party software, database firewalls add another layer of security to your database. Firewalls function as proxies, helping ensure incoming and outgoing traffic is authorized and secure, while also working to prevent successful SQL injections.
7. Educate Your End Users
Studies show that as the amount of cybercrime continues to increase year over year, attacks are being focused more on people rather than systems. You can have all the firewalls and SIEM applications in the world, and user-generated security issues can still slip through. For instance, if a manager or someone in your organization with admin privileges keeps their passwords sticky-noted to their monitor, under their keyboard, or in some other conspicuous location, it increases the opportunities for someone who’s up to no good to do something malicious.
Holding regular security training sessions for the regular end users at your organization can be a useful way to emphasize the importance of being careful. It provides a chance for support technicians or DBAs to keep workers up to date on security standards, legislation, and cybercrime trends.
8. Stay Vigilant
The unfortunate reality is database security is a constant and ongoing process. There’s no one-and-done model. We live in the information age, data is valuable, and cyberattackers are determined. Resting on your laurels or treating security as something to take care of when you have the time is a surefire recipe for trouble. The responsibility of actively ensuring your Oracle database security standards are not only up to date but also enforced is a big one, but it’s also an essential part of doing all you can to prevent your database from being hacked. I am not saying you should be paranoid, only that you should remain cautious, observant, and aware.
It can seem like an uphill battle; but in the same way we don’t hear about all the airplane flights that land without issue, we don’t often hear about an IT department successfully fending off an attempted cyberattack. In many cases, no news is good news—and a sure sign you’re properly protecting your data.
