Websites and applications all need to interact with their users, which means users must have some way to input data, whether it’s a text box on a website or a web form within an application. When this kind of input data is directly turned into a SQL query, the program or website allowing the input can be vulnerable to malicious code. This is known as SQL injection.
Understanding how SQL injection works is vital information for application and web developers, as well as network and security professionals who may end up dealing with the repercussions of a poorly developed website. In this guide, I’ll explain the two key questions you must understand when working to prevent or resolve SQL injection. I’ll also review the best tools to help protect against SQL injection attacks available on the market today.
What is SQL Injection?
Types of SQL Injections
How to Prevent SQL Injection
Best SQL Injection Prevention Tools
How Tools Help Prevent SQL Injection Attacks
SQL Injection Definition
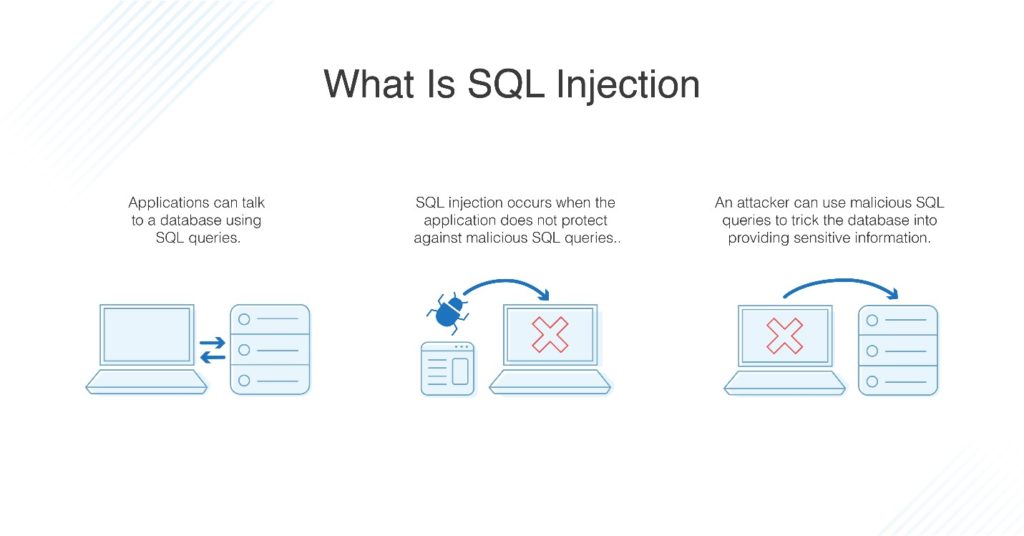
SQL is a programming language designed to manage large amounts of data stored in a database. It’s primarily used to access, add, modify, and delete data from these databases.
When a part of a website or application allows a user to input information turned directly into a SQL query, this makes the website vulnerable to SQL injection. SQL injection is when malicious code is inserted as user input, so once it gets into the system and is turned into a SQL query, it begins to execute the malicious code. Usually the purpose of this code is to access data to steal it (like user credentials) or delete it (to harm a business). If an attacker manages to access data and impersonate a database administrator, they can then access the entire system using those copied credentials.
Types of SQL Injections
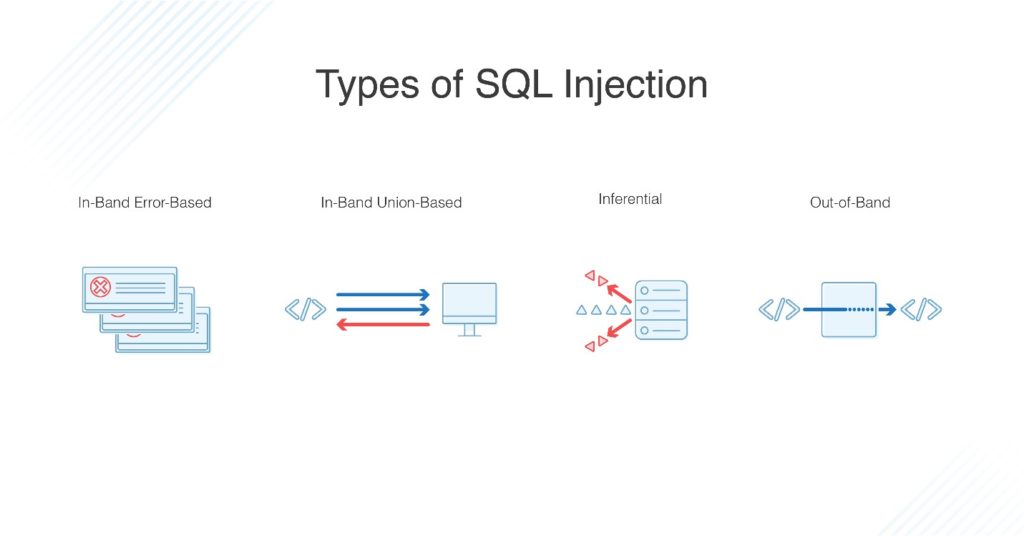
There are a few different SQL injection types, including:
- In-band: This classic type of SQL injection describes an attack in which the attacker uses the same channel to both inject the attack and obtain their desired data results. There are two main types of in-band attack, called error-based and union-based SQL injection. Error-based SQL injections trigger the system into producing errors, building up a picture of what the database looks like. Errors are useful when developing the database and for network administrators, but only certain errors and information should be displayed on a live web application.
Union-based SQL injection exploits a vulnerability in the way SQL is written, by using the “UNION” operator to get the database to return more information than should be accessed. - Inferential: Inferential SQL injections, also known as Blind SQL injections, generally take longer to carry out. They don’t transfer data through the web application but instead send payloads to the database server to look at how it responds and use the resulting information to infer information about the database. For example, it may send a SQL query asking for a time response that either responds immediately or with a delay, depending on if the query to the SQL database returns “true” or “false.”
- Out-of-band: Out-of-band SQL attacks aren’t common, as they use two different channels to send the attack and then receive the results. This can only occur if particular features are enabled on the SQL database.
How to Prevent SQL Injection Attack
Preventing SQL injection can be achieved at several points along your system pathway.
- Design to prevent SQL injection. The first technique to prevent SQL injection is to make sure your application is designed to reduce the surface area through which an attacker can inject code. With good coding practices and code quality tools, you can detect user input and interfaces which expose too much surface area to attack.
- Awareness of vulnerabilities. No matter how well you write your code in the first place, new vulnerabilities can arise whenever code is added or changed. SQL injection vulnerabilities can also be discovered in old code previously assumed to be safe. Make sure you subscribe to updates from security communities so you’re aware of any new issues. Then, review your existing codebase to check for vulnerabilities.
- Tools and software. Next, you can also use tools or software to keep an eye on your system security, so if a vulnerability has gone undetected, the tool will pick up on any issue. Make sure you have set up access alerts and anomaly detection. Choose one of the following tools to get started with protecting your network against SQL injection attack.
Best SQL Injection Prevention Tools
SolarWinds® Security Event Manager (SEM) is my top choice for keeping an eye on how your network is behaving and flagging issues like a SQL injection. Making sure you quickly respond to a SQL injection is extremely important, because attackers can access vital and confidential data fast.
SolarWinds SEM can be set up to automatically respond to suspicious IP addresses or shut down applications behaving strangely (suddenly producing a lot of errors). As a result, you can minimize time delays if there’s an attack on your system. It also keeps tabs on file and USB integrity and can stop data download or access if something doesn’t look right.
The best part is you can try out SEM free for 30 days, and afterward, you simply pay per node.

You can also consider Netsparker Vulnerability Scanner as a SQL injection detection tool. Vulnerability Scanner is a web application security tool with reporting and workflow capabilities. Netsparker includes a special tool called Proof-Based-Scanning technology, which automatically verifies whether any of your security scan results are false positives. This can help prevent database admins or security staff from having to check through all the results from a vulnerability scan.
This is a highly scalable app with the ability to automate a large part of your vulnerability scanning. This relatively new product is still getting some details ironed out, namely issues such as the high system usage while the scanner is running. Rather than a background “always on” tool, this is better used as a periodic scanner.
Leveraging a SQL Server performance monitoring solution like SQL Sentry can also be an effective tool in your toolbox when it comes to taking proactive and ongoing measures against and mitigating the damage caused by SQL injection attacks.
SQL Sentry can help support broader SQL Server security measures with the following features:
- Define alerting and automated remediation for known performance pitfalls
- Know when a new release or data churn over time has changed the performance profile for one or more queries
- Grant read-only access to users, allowing support teams the ability to review dashboards as well
You can download a free 14-day trial of SQL Sentry.
This web vulnerability scanner tool is popular for protecting against common vulnerabilities, including SQL injection, cross-site scripting, and more. It contains a JavaScript analysis engine to help detect security risks and uses “out of band” techniques in addition to conventional scanning. Like many enterprise-grade tools, Burp updates with information on the latest SQL injection vulnerabilities to ensure your system is protected. When the tool detects an issue, it automatically provides step-by-step advice for how to remediate the problem. You can also take advantage of useful manual tools and custom configurations for scanning, viewing, and reporting. Exact capabilities depend on your investment, as the tool comes in Enterprise, Professional, and Community versions.
How Tools Help Prevent SQL Injection Attacks
While all the above tools are built to help prevent SQL injection attacks, you should also take steps to set up your websites and applications to be protected against SQL injections in the first place. Then, with careful site design and high-quality protection tools such as SolarWinds SEM on your side, you’re in the best position to keep your sensitive data safe from an attack.
Further Reading
What Is a Data Breach? Ultimate Guide to Cybersecurity Breaches: Attackers are becoming more and more advanced, and software must adapt in response. I prepared an article about data breaches and how to prevent them, so you can keep your organization’s data safe.
