As business technology and security systems continue to evolve, so do the tactics used by cybercriminals. In 2018, businesses worldwide lost $2.7 billion because of cybercrime, and research shows this number will continue to grow every year. These losses include ransoms paid to cyberattackers, fines, money paid for updates and repairs, and the costs associated with lost clients and diminished reputation.
A common misconception is only large organizations are at risk of cyberattack. However, there has been a significant rise in the targeting of small and medium-sized businesses. This is because these smaller organizations tend to use less-sophisticated cybersecurity measures. As much as 50% of all cyberattacks target small businesses, costing an average of $200,000—enough to put less-established companies out of business.
To protect your business from cyberattacks, you should arm yourself with an enterprise-grade security system and knowledge of the different types of cyberattacks facing businesses today. By understanding what you’re up against, you can effectively combat cyberattacks and minimize your business’s vulnerability to them.
Here is the list of 6 common types of cyberattacks. Feel free to jump ahead to the selected description:
- SQL Injection Attack
- Phishing and Spear Phishing Attacks
- Malware
- Botnets
- Cross-Site Scripting Attacks
- Denial-of-Service and Distributed Denial-of-Service Attacks
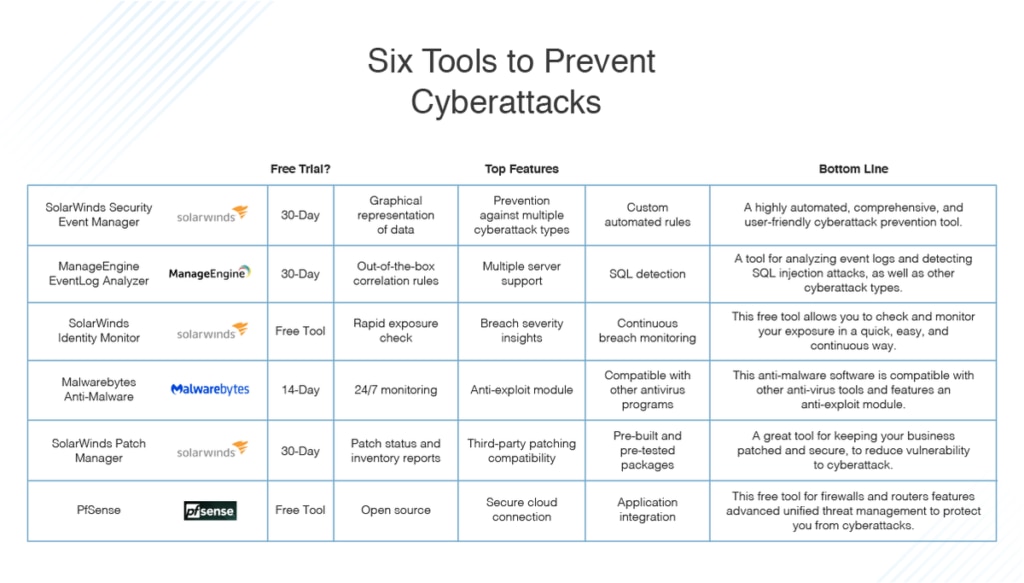
This guide outlines the most common types of cyberattacks and recommends SolarWinds® Security Event Manager (SEM)—among other tools—as a sophisticated, comprehensive, and user-friendly solution to your IT security needs.
Here is the list of all solutions presented in this article:
- SolarWinds Security Event Manager
- SolarWinds Patch Manager
- SolarWinds Identity Monitor
- ManageEngine EventLog Analyzer
- Malwarebytes
- pfSense
What Is a Cyberattack?
A cyberattack is an intentional attempt to exploit networks, computer systems, and enterprises dependent on technology. Cyberattacks use malicious code to modify computer data, code, or logic, often resulting in data compromise and sometimes identity or information theft. A cyberattack is sometimes called a computer network attack, or CNA.
Types of Cyberattacks
There are many types of attacks in cybersecurity. And although attacks evolve every day, cybercriminals are rarely looking to reinvent the wheel. Instead, they rely heavily on the approaches they know to be effective. The following list of types of cyberattacks focuses on those most commonly used by criminals.
For each type, I’ve provided recommendations for tools to help protect your business. I’ll discuss these tools in-depth in the second half of this article.
- SQL Injection Attack
The SQL injection attack has become a common problem for database-driven websites. These attacks occur when a SQL query is executed by a cybercriminal and issued to a database, delivered from the client to the server via the input data. The SQL command is injected into data-plane input, often instead of the password or login credentials. This allows the cybercriminal to run their own predefined SQL commands.
When a SQL injection attack is successful, sensitive information can be read, stolen, modified, inserted, updated, or deleted. Cyberattackers can also execute administration processes, like shutdown, on the database; recover content from any given file; and even issue commands to the operating system.
SQL injection detection tools:
- Phishing and Spear Phishing Attacks
A phishing attack entails the cybercriminal sending emails that appear to be from trusted sources. The aim of this type of attack is to acquire a person’s sensitive information or to influence them into doing something. It might, for example, feature an attachment that downloads malware onto the device when opened. Alternatively, it might provide a link to a fake website to persuade someone to hand over their information or trick them into downloading malicious software.
Spear phishing is more targeted. These attacks require the attackers to conduct research into their targets, so they can craft a tailored and personal email. This makes spear phishing very difficult to defend against. For example, the “from” field in an email might be fake, leading the recipient to believe the message is from someone they know; or an email might pretend to be from a person’s employer, requesting urgent funds. Another popular spear phishing technique is to clone a legitimate website, thereby tricking a person into entering their login credentials or personal information.
Spear Phishing detection tools:
- Malware
Malware, or “malicious software,” is unwanted software installed on your system or device without your knowledge or permission. Malware often infiltrates a system by attaching itself to authentic code and propagating. It can hide in applications or duplicate itself via the internet. There are many different types of malware, and more and more emerge every year, but these are the most common malware types:
- System or Boot-Record Infectors: Boot-record viruses attach themselves to the master boot record on hard disks. When the system is initialized, it will review the boot sector and then load the virus into the system’s memory, where it goes on to infect other computers and disks.
- Macro Viruses: A macro virus infects applications, like Microsoft Excel and Word, by attaching themselves to their initialization process. When the application starts up, the macro virus executes instructions and transfers control to the infected application. It then replicates and attaches to other code.
- File Infectors: These viruses attach to executable code, like .exe files. When the code is loaded, the virus installs. Another type of file infector creates a virus file with the same name as a legitimate file, but with a .exe extension. When the file is opened, the virus code is executed.
- Trojans: A trojan, sometimes called a trojan horse, is a malicious program hiding in a legitimate program. The difference between normal viruses and trojans is trojans can’t replicate. Trojans not only launch an attack, but also create a back door to exploit for future attacks. For instance, a trojan could be designed to create a high-numbered port, which would allow the attacker to execute a new attack.
- Stealth Viruses: These viruses conceal themselves by taking control of system processes and functions. They compromise malware detection software, so it reports infected aspects of the system as being uninfected. Stealth viruses can hide an increase in the size of a file being exploited and changes to the file’s date of last modification.
- Logic Bombs: Logic bombs are another example of a malicious program. These viruses attach themselves to an application and are triggered by specific events, like a certain time or date.
- Ransomware: Ransomware is a well-known type of virus that prevents access to the system’s data. The attacker may also threaten to publish or delete sensitive information if the ransom is not paid. Simple ransomware is relatively easy to fix, but when an attacker uses more sophisticated malware—like crypto viral extortion—recovering the files is almost impossible.
- Adware: Adware is a software program used by businesses as part of their marketing efforts. It usually manifests as advertisements or banners displayed while applications are running. When you browse a website, adware can automatically download itself to your device.
- Spyware: This type of cyberattack is designed to collect information on the victim, particularly their browsing habits. Spyware tracks everything you do without your consent or knowledge and delivers the information directly to a remote user. It can install other malicious applications onto your system via the internet.
Malware detection tools:
- Botnets
A botnet comprises personal computers or devices collaborating to achieve a specific task. We call it a “botnet” because these programs, otherwise known as bots, or robots, exist across a network of devices.
A single bot can’t do too much damage, but collectively they’re powerful and potentially dangerous. Botnets are used by cybercriminals to drive a range of cyberattacks. They can help a cyberattacker facilitate a denial-of-service attack, for example, which floods a webpage with traffic designed to take it offline. Such attacks can cost a business millions of dollars in losses, fines, and clients.
Botnets are also used to steal passwords and sensitive information, spread spam, and distribute viruses. Botnets are popular tools for cybercriminals because they’re cheap and effective. To protect your business from botnets, you should employ a comprehensive IT security solution.
A bot attack can be used to bypass enterprise firewall security measures and can potentially infect thousands of devices, turning them into a network of bots. These bots will remain benign until they establish communication with a command and control server. Bot armies can then launch a range of attacks, including online scaling, crypto mining, and much more.
Botnet detection tool:
- Cross-Site Scripting Attacks
Cross-site scripting attacks, otherwise known as XSS attacks, use third-party web resources to execute scripts in a person’s scriptable program or web browser. XSS attacks involve an attacker injecting a payload infected with malicious JavaScript into a website’s database. If the intended victim attempts to visit a page on this website, the page is transmitted with the payload as part of the HTML body. This is then transmitted to the intended victim’s browser, which activates the script.
The script could send a user’s cookie to the cyber attacker’s server. This would allow the attacker to extract it and use it for session hijacking purposes. XSS can have severe consequences if used to exploit other vulnerabilities, which could potentially enable the attacker to capture screenshots, log keyboard activity, steal network data, and even remotely control the victim’s device.
XSS can be used to launch an attack from within ActiveX, Flash, VBScript, and JavaScript. Since JavaScript is widely supported, it’s the most commonly abused method of executing XSS attacks.
Lots of web applications have weaknesses, which allow cybercriminals to use XSS to misrepresent the website being visited. To snag a victim, all the attacker has to do is get them to interact with these illegitimate webpages and unknowingly click on malicious script. Given how easily someone could fall victim to an attack of this nature, employing an effective security solution is of critical importance.
Cross-site scripting detection tool:
- Denial-of-Service and Distributed Denial-of-Service Attacks
A denial-of-service (DoS) attack is used by hackers to overload a system’s resources, which causes the system to become unresponsive to service requests. A distributed denial-of-service (DDoS) attack also targets the system’s resources, but the source of the launch comes from a large number of host machines, each of which is infected and under the control of the cyberattacker.
DDoS attacks work in partnership with botnets and are capable of completely incapacitating a website or online service. They do this by overwhelming the target with a flood of activity from hundreds or even thousands of devices in a botnet.
Unlike other attacks, which are usually aimed at allowing the attacker to gain access, DoS attacks don’t directly benefit the person responsible for the attack. In some cases, cyberattackers seem to be satisfied with mere denial of service. If, however, the targeted resource is owned by a competing business, DoS attacks can benefit the attacker by ruining their competitor’s reputation and ability to deliver services.
Another reason an attacker might use DoS or DDoS is to make the system vulnerable to another attack. By taking the system offline, a cyberattacker could then use session hijacking, for example, to reap some reward.
There are several different types of DDoS and DoS attacks, including TCP SYN flood attacks, smurf attacks, teardrop attacks, and ping of death attacks. Botnets, which were explained earlier in this guide, are also considered a type of DDoS attack.
- TCP SYN Flood Attacks: To execute a TCP SYN flood attack, the cyberattacker uses the buffer space during the initialization handshake of a Transmission Control Protocol (TCP) session. By exploiting the buffer space, the attacker can flood the victim’s system’s in-process queue with a mass of connection requests but doesn’t respond to request replies. As a result, the system times out, and the overload on the connection queue causes it to crash.
You can protect yourself from TCP SYN flood attacks by placing servers behind a firewall configured to prevent SYN packets and by increasing the capacity of the connection queue while decreasing the timeout on live connections. - Smurf Attacks: Smurf attacks involve using the Internet Control Message Protocol (ICMP) and IP spoofing to flood the victim’s network with traffic. This attack type uses ICMP echo requests, which originate from a fake victim address.
As an example, if the target IP address were 10.0.0.10, then the cyberattacker would create a fake ICMP echo request from the same address number and send the request to the broadcast address 10.255.255.255. This ICMP request would then be sent to all the IPs in the range, but all responses would be redirected to the target’s address. This, in turn, overwhelms the network. Smurf attacks can be repeated and even automated, resulting in massive network congestion.
To protect yourself from smurf attacks, you will need to disable your router’s IP-directed broadcasts. Alternatively, you could configure the end systems to prevent them from replying to ICMP packets originating from broadcast addresses. - Ping of Death Attacks: The ping of death attack pings a victim’s system with an IP size exceeding the maximum number of bytes. It uses IP packets to do this. IP packets of this size, however, are not permitted, so the cyberattacker has to divide the IP packet. When the victim’s system reconstructs the packet, it will potentially experience crashes.
Employing an effective firewall to check fragmented IP packets for maximum size can prevent these types of attacks. - Teardrop Attacks: The teardrop attack causes the length and fragmentation offset fields of the sequential IP packets to overlap each other on the targeted host. During this process, the targeted system tries to reconstruct the packets with no success, and the system crashes under pressure.
It’s important for users to have patches to protect them against this type of DoS attack. If you don’t have patches, make sure you disable SMBv2 and block ports 445 and 139.
DDoS detection tools:
Useful Cyberattack Detection Tools
When looking at how to prevent cyberattacks, implementing the right software is paramount. Above, I recommended the best tool or tools for each type of cyberattack. In this section, we’ll look at these solutions and how they work to ensure security.
1. SolarWinds Security Event Manager
SolarWinds SEM is a great tool for detecting SQL injection attacks and proactively protecting your database server from them. It features a correlation manager to identify suspicious activities, alert you to them, and respond to potential attacks automatically, according to preconfigured event rules. By using a pre-populated list of vectors often found in SQL injection attacks, the rules can effectively and rapidly detect and stop these attacks.
When cybercriminals try to execute an SQL injection attack, they usually generate SQL errors. SEM identifies these errors and flags them in real time and alerts you to unusual system table references made by accounts that aren’t whitelisted. This activity could herald a potential SQL injection attack, so being kept informed is crucial.
SQL injection attacks often limit the attacker to retrieving information from a single row per query, because of limitations associated with the original query. This behavior can result in a high offset. SEM monitors and flags unusually high offsets and allows you to establish a rule activity filter, which sorts recent and historical events on the server that triggered rule activation. With SEM’s log correlation manager, you can search and sort log data, using it to drill down into and locate certain activities. You can also use templates to create rules with the built-in rule creation utility.
SolarWinds SEM helps prevent phishing and spear phishing attacks by monitoring user accounts, logs, and system changes. It features file integrity monitoring, which allows administrators to proactively detect any alterations made to folders, files, and registry settings. When a modification is suspicious, cybersecurity alerts are automatically delivered to the relevant IT team members. To save you time, you can also automate how SEM responds to specific events by establishing custom rules. The tool recognizes shifts in account usage patterns in real time, delivering notifications, so you can respond to any unusual activity instantly.
SEM additionally serves as a malware detection and prevention solution, offering advanced anti-ransomware capabilities. With the tool’s sophisticated SIEM utilities, you can implement security best practices and optimize ransomware detection. With SEM, ransomware detection begins with effective privileged-access management processes, which keep ransomware and other cyberattacks from gaining access to privileged or administrative accounts. SEM monitors user activity, detecting and flagging any changes in file extensions, locations, and permissions.
SEM’s most notable anti-ransomware feature is the community-sourced, regularly updated intelligence feed. This feed lists all known malicious hosts, IPs, and attack vectors, so your log data can be analyzed alongside it, facilitating the rapid detection of attacks.
The solution also features a botnet detection tool that, unlike traditional botnet detectors, includes a built-in correlation engine capable of identifying abnormal behaviors and patterns in a network’s traffic. This information is an invaluable resource for mitigating botnet attacks.
SEM gathers data logs from multiple sources, including servers, IAM solutions, endpoints, IDS/IPS, and firewalls. These logs are then synthesized to improve the application’s situational awareness across the entire network. As with other threats and attack types, SEM uses the community-sourced lists of known bad actors to detect bots. It also allows you to create your own policies and can automatically undertake IP blocking, account shutdowns, and alerting.
SEM uses log file monitoring, alerting, and active response processes to mitigate the threat of XSS attacks. Aggregating logs into a single, unified view, helps IT departments and administrators establish complete control over their log data. By combining all security logs, security-related systems, devices, and applications into one tool, SEM vastly improves threat detection capabilities. Most importantly, it offers a robust way of remediating XSS attacks and other cyber threats.
SEM comes with preconfigured rules, created by SolarWinds experts, to identify and prevent XSS. It does so by referencing a list of common vectors and constantly monitoring your logs for them. The tool’s XSS prevention capabilities will alert you to attacks in real time, and you can configure automated responses to disable or halt certain operations.
SEM is also effective at detecting and preventing DDoS attacks. Continuous log monitoring ensures you stay informed of what’s happening in your environment, in real time. If any issues arise, you can respond with rule-based correlation built for rapid implementation—no more custom scripts. The defense alerts and automated response mechanisms protect your system even when you aren’t at your desk.
Prior to many security attacks, credentials are stolen or permissions are escalated. This is how a lot of cyberattackers gain access in the first place, which is why privileged accounts management is key to protecting your business’s security. SEM features a Privileged Account Monitoring (PAM) tool, which allows you to monitor, track, and report on privileged user behavior.
PAM was designed to assist you in implementing a policy of least privilege, which reduces unnecessary allocation of permissions and ensures access to sensitive information is as limited as possible. It also gives you insight into how current privileged accounts are behaving, so you can investigate any unusual activity.
A 30-day free trial of SEM is available.
2. SolarWinds Patch Manager
Successful cyberattacks are usually caused by exploited vulnerabilities. Poor patch management can create numerous vulnerabilities within your business, which is why it’s key to have an informed patch management strategy in place. SolarWinds Patch Manager is an extremely useful tool because by keeping your business patched and secure, it can prevent one-off cyberattacks that allow an attacker to gain access to your system.
Patch Manager helps you manage, diagnose, and fix issues with your Microsoft products via Windows Update Agent. This means you can schedule patches and report on patch status and inventory, which Windows Server Update Services can’t do alone. You can view detailed information on third-party software patches and the status of SCCM-managed endpoints.
Patch Manager also features pre-built and pre-tested packages, doing away with the need for extensive research, scripting, packaging, and testing of patches. With these third-party application packages, built and tested by the experts at SolarWinds, you can save a significant amount of time.
A 30-day free trial of Patch Manager is available for download.
3. SolarWinds Identity Monitor
This is a fantastic tool for ensuring your emails remain private and secure, guarding you against spear phishing attacks. Identity Monitor lets you check your exposure by simply entering your details on the website, you gain instant insight into past data breaches, with information on the level of severity, the data involved in the breach, and the type of breach. The tool can monitor for breaches continuously and notify you, so you can act before damage is caused. You can even conduct password resets through the program.
Identity Monitor lets you check your email address exposure for free here.
4. ManageEngine EventLog Analyzer
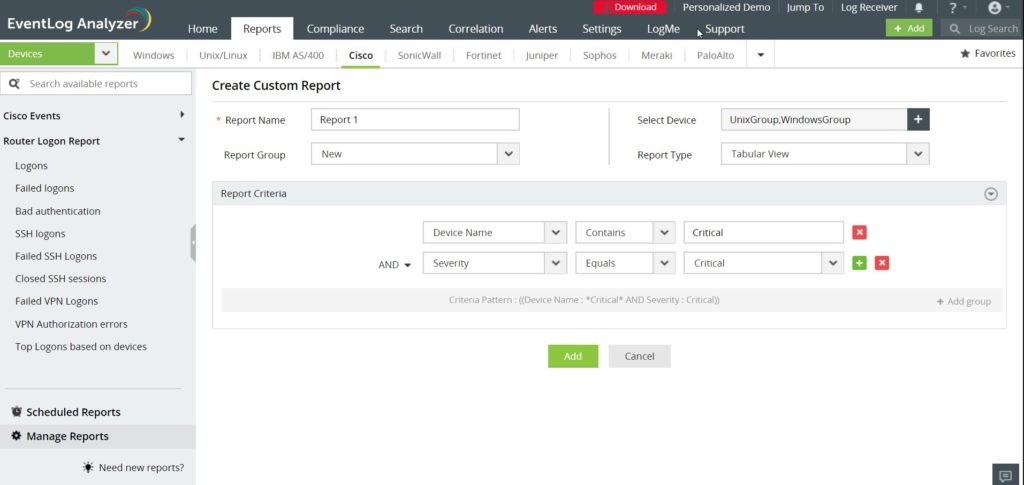
This is another effective SQL injection detection and cyberattack prevention tool. EventLog Analyzer looks for vulnerabilities and potential data breaches by running SQL injection reports for Apache web servers, IIS web servers, Oracle database servers, and Microsoft SQL servers. It provides out-of-the-box SQL injection correlation rules for events detected in the web server, database events, Oracle security incidents, Microsoft SQL security incidents, and Apache and IIS web server events.
A 30-day free trial of EventLog Analyzer is available.
5. Malwarebytes
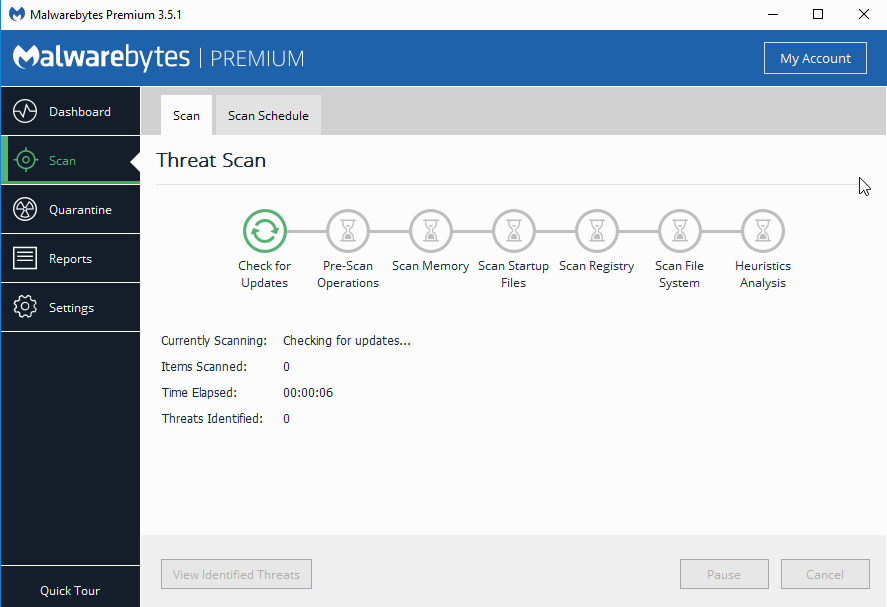
Malwarebytes is a popular program that conducts deep scans for malware, effectively removes all instances, and provides daily updates. Malwarebytes Premium can remove all advanced threats, including spyware, and monitors for malware 24/7.
This program features an easy-to-use interface and an anti-exploit module to protect vulnerable systems and applications from exploit attacks. It can protect you from malicious websites by preventing them from gaining access, and it halts ransomware in its tracks before data is held hostage. One of the most notable benefits of this software is it works well alongside other antivirus programs.
6. pfSense
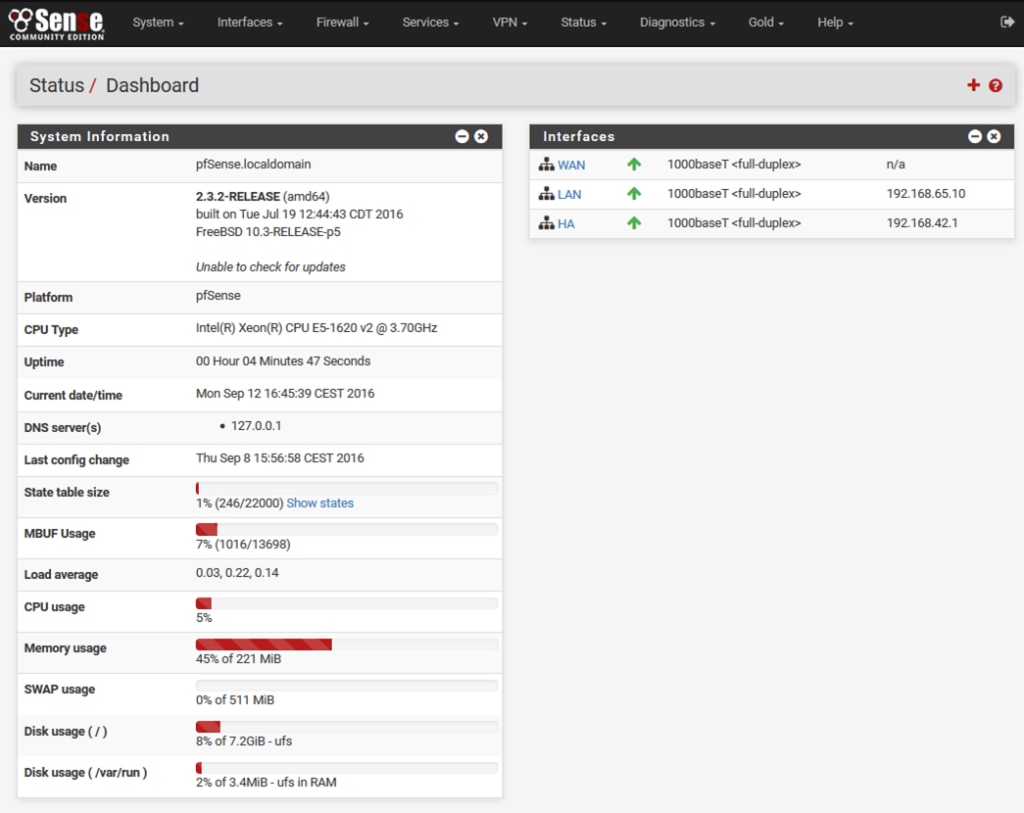
This popular open-source network security program can protect you against many DoS and DDoS attacks. PfSense allows you to securely connect to the cloud, extending your applications and connectivity to all your users, no matter where they are, via Microsoft Azure and Amazon AWS.
This program is highly cost-effective, though it’s important to note open-source programs aren’t especially well-suited to business use. However, if you are a fan of the flexibility open-source software offers, then pfSense comes highly recommended.
Best Cyberattack Prevention Tool
Although all of the tools mentioned in this guide offer robust cyberattack prevention and detection solutions, none are as versatile or comprehensive as SolarWinds SEM. SEM bundles an impressive range of sophisticated utilities designed to protect you and your business from bot attacks, cross-site scripting attacks, DoS and DDoS attacks, spear phishing attacks, and much more. Not only is the solution advanced enough for enterprise-grade use, but it’s also approachable for beginners.
SEM is a one-stop-shop, all-in-one IT security program. It features a dynamic dashboard, where data is represented in the form of line graphs, pie charts, and bar graphs, among other graphics, making it easy to read and interpret. One of the benefits of adopting this software is it is compatible with other SolarWinds solutions, including Patch Manager and Identity Monitor. This allows you to extend your network and IT security solution, making it more powerful, flexible, and versatile.
