A security log keeps a digital record of all your server activity and can provide an IT security admin a centralized view to better log and track who has made what changes, as well as if there are any issues with the data.
A security log can be crucial to your company. For some, a security log is a professional requirement—for example, medical professionals must keep years of logs according to HIPAA compliance regulations. In high-stakes data entry, a pristine security log can also mean the difference between an easy forensic analysis of company log activity or an endlessly confusing search to identify discrepancies.
When you keep a close eye on your security log, you can provide yourself and your company some much-needed peace of mind. By following common security best practices when it comes to log retention and monitoring, you’ll find it easier to ensure your security logging process helps protect your overall IT infrastructure. In this guide, I’ll dive deeper into each of these best practices to explain their importance and discuss some easy ways you can achieve them.
Security Log Retention Best Practices
Security Log Access Rights Best Practices
Security Log Monitoring Best Practices
How to Improve Security Log Analysis
Security Log Retention Best Practices
To ensure security—and compliance—it’s crucial to retain relevant log data for a long enough time. Having this historical data can allow you to more easily see common trends in, as well as causes, of insecure log data.
One way to achieve this is by leveraging an audit trail, a digital record of server activity including data entry and user access activity. In fact, many companies require audit trails due to applicable compliance standards. For example, HIPAA sets the log standards for medical professionals, GLBA for financial professionals, SOX for company financial data, and so on. Some regulations may even require security logs data for as long as six years of company activity. As a result, it’s important to ensure you’re retaining security logs for a long enough time and running reports on those logs within that time.
For an easy-to-use security log system, I’d recommend Security Event Manager (SEM). The insights provided in SEM can help you perform audits on applications and devices across your environment while simultaneously helping ensure the safety of your system by comparing issues to a list of known threats. SolarWinds® SEM generates security reports to help you demonstrate compliance with a longer list of regulations than traditional security report software—from HIPAA to NERC CIP, GLBA, SOX, and more.
As far as log retention goes, SEM includes three types of datastores: a raw database for original log datastore, a syslog/SNMP data log store, and an event store with all the normalized log events from SEM. SEM offers 230GB by default for log and data retention. Additionally, SEM stores original syslog data for 50 days in its original format in case you need to review it, with data compressed and rotated to maintain 50 days of data at a time. By regularly backing up the SEM VM, you can easily back up log data elsewhere for additional retention and offline storage.
Security Log Access Rights Best Practices
Another way to retain a successful security log can be to invest in software with the capacity to quickly analyze the history of user data from a central management console. Too often, when IT professionals are performing security audits, they must track down multiple different security management consoles to pinpoint the source of a user access issue.
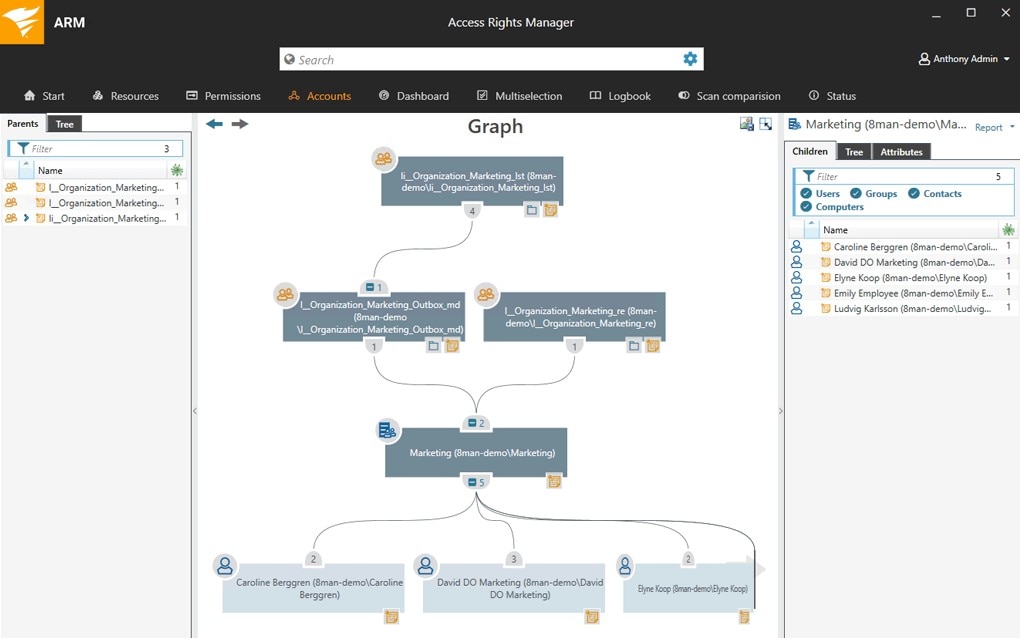
I’ve found Access Rights Manager (ARM) to be an effective way to centralize analysis of user activity security logs, which can prevent confusion during the high-stress time of an IT security audit. SolarWinds ARM includes a “deep visibility” feature, which provides an easily-to-digest visualization of what users have access to what data, including when they accessed which resources. In terms of retention, this tool typically stores events for 30 days, although you can manage this setting. How many events you can effectively store (and then report on) depends on your own storage space limitations, but 30 days is typically a good place to start.
Security Log Monitoring Best Practices
- Use a tool to actively monitor logs to identify and alert on security issues
Beyond retaining event data, log files, and resulting reports for enough time, it’s important to have a tool actively monitoring logs to identify and alert on security issues. I like to use software to keep tabs on my security log to make sure there’s no unusual exterior intervention, like malware and hacking. But I also need to make sure there’s no strange behavior from password-capable agents inside my server.
I like to run software to block these potential threats before they affect my data, and quickly respond if they detect any sort of looming threat. I’ve found a clean security audit can be worth the investment in security monitoring software.
- Collect and aggregate logs to a central platform, where they can more easily be analyzed
Any applications and devices can be targets for potential hackers. So, I need a trustworthy quick-response program to defend the networks on my premises. Luckily, all manner of apps and devices generate logs that can be collected and aggregated to a central platform, where they can be more easily analyzed. Part of this is ensuring log data is standardized for easier use. Admins should look for a security logging monitoring program which, in addition to helping with efficient security log retention, includes features to automatically perform this collection then analyze the logs to quickly react to potential security threats.
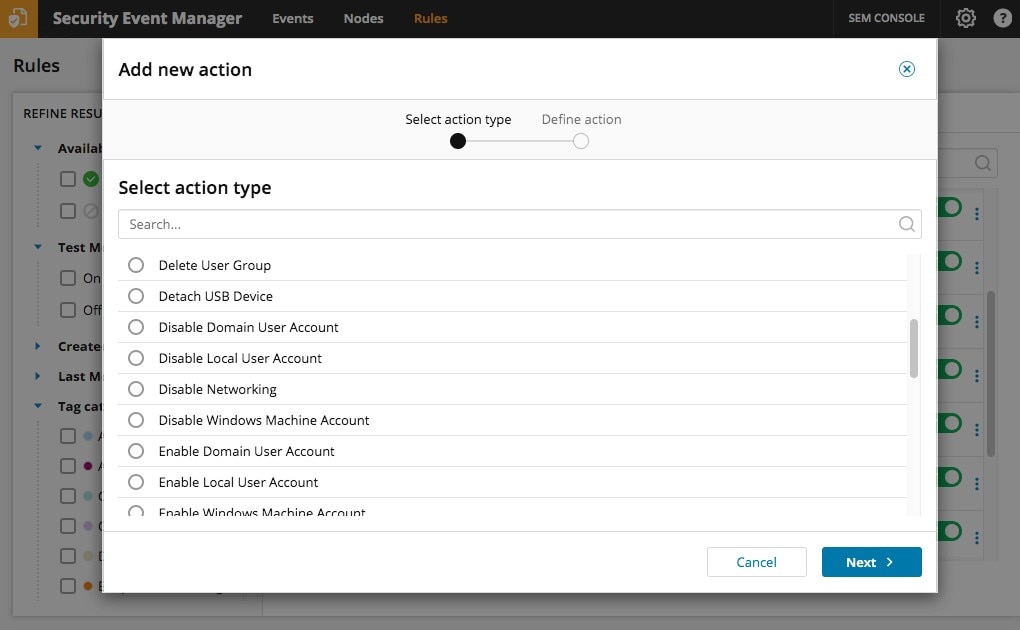
- Compare potential threats to a database of known threats and respond to them
Effective log monitoring should include a comparison of potential threats to a database of known threats—a more common but critical feature for security logging software these days. To block identified exterior threats, an effective security log monitoring tool should also be able to respond to threats with some initial action, at least before an admin can take steps to protect the network. Also, look for a tool with response capabilities. If the threat is grave enough, the tool may be able to shut down or restart a unit, send alerts and pop-up messages, log off users, and even detach suspicious USB devices.
- Monitor user activity
What about threats from inside the network from internal user activity? For many companies, the collection of network users is often so wide it’s impossible to trust the motives of every password-protected user. It’s also possible for a hacker to obtain verified access credentials. If a suspicious user is already privy to password access on a company’s server, you need security defense strategies distinct from outsider hacking and viruses as well as a way to monitor and prevent insider threats and privilege abuse.
This means investing in a security log monitoring tool with a focus on user activity, both in real-time and over a historical view. Look for a tool capable of detecting any risks associated with a privileged user. With many members in a security group, it can be crucial to immediately know whose account or what directories might be compromised. It’s also useful to have a tool providing a central visualization of privileged accounts, allowing you to run reports based on user activity logs. When a company’s institutional standing depends on a security audit, trusting unusual activity from privileged accounts isn’t worth the risk.
How to Improve Security Log Analysis
By retaining logs to meets compliance log retention standards and using these logs to identify potential threats, focusing on user access and activity logs to catch additional risk factors, and implementing an overall strategy around security log monitoring, you are on your way to better identifying and alerting on security issues. Also, make sure you check out how a security log monitoring tool like SolarWinds Access Rights Manager can help support your efforts in improving the overall security posture of your organization.
