Remote access technology is an incredibly useful tool, enabling IT support staff to quickly access and control workstations and devices across vast physical distances. When deployed effectively, the technology has the potential to maximize the efficiency of IT departments and provide rapid, responsive support for an organization’s end users.
However, like any other networked connection, application, or device, remote access technology requires security measures to ensure it remains protected from potential bad actors. The ability to access and directly control systems and processes from afar can be disastrous if it falls into the wrong hands.
Jump ahead:
What Is RAT Software?
How Are RATs Useful to Hackers?
How to Protect Yourself from RAT Software
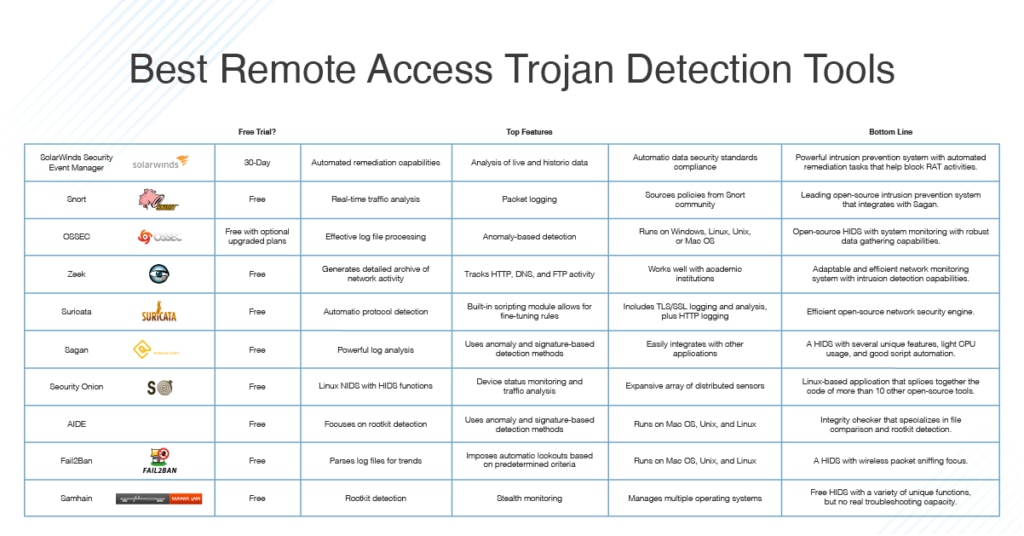
The 10 Best RAT Software Detection Tools:
Selecting the Right Remote Access Trojan Detection Software
What Is RAT Software?
One malicious example of remote access technology is a Remote Access Trojan (RAT), a form of malware allowing a hacker to control your device remotely. Once a RAT program is connected to your computer, the hacker can examine the local files, acquire login credentials and other personal information, or use the connection to download viruses you could unwittingly spread along to others.
Like most other forms of malware, Remote Access Trojans are often attached to files appearing to be legitimate, like emails or software bundles. However, what makes Remote Access Trojans particularly insidious is they can often mimic above-board remote access programs. They don’t usually announce themselves once they have been installed—they won’t appear in a list of active programs or running processes, for instance—because it’s more advantageous for hackers to keep a low profile and avoid detection. Without taking proper security measures, it’s possible you could have a Remote Access Trojan on your computer for an extended period without it being detected.
How Are RATs Useful to Hackers?
The practice of stealthy, ongoing hacking seeking to accumulate data over time, as opposed to causing damage to information or systems, is known as an advanced persistent threat (APT). Remote Access Trojans are a powerful tool in this type of attack, because they do not slow down a computer’s performance or automatically begin deleting files once installed—and because they’re so adaptable.
Unlike other types of virus—such as keyloggers, which record everything someone types on the infected computer, or ransomware, which essentially holds a computer or files hostage until the hacker is paid off—Remote Access Trojans give hackers total administrative control over the infected system, so long as they remain undetected.
As you might imagine, this can lead to sticky situations. A Remote Access Trojan paired with a keylogger, for instance, can easily acquire login information for bank and credit card accounts. Used together, these approaches can discreetly turn on a computer’s camera or microphone, or access sensitive photos and documents. They can even use your home network as a sort of proxy server, through which a hacker can commit crimes anonymously and, for the most part, with impunity.
Remote Access Trojans can be used toward more straightforwardly malicious ends, as well. The administrative access they provide means hackers can resort to wiping hard drives, downloading illegal content if they so choose, or even impersonating you on the internet.
This can have geopolitical repercussions. If hackers manage to install Remote Access Trojans in important infrastructural areas—such as power stations, traffic control systems, or telephone networks—they can wreak havoc across neighborhoods, cities, and even entire nations.
An example of this occurred in 2008, when Russia used a coordinated campaign of physical and cyber warfare to seize territory from the neighboring Republic of Georgia. The Russian government did this using distributed denial-of-service (DDoS) attacks which cut off internet coverage across Georgia, combined with APTs and RATs allowing the government to both collect intelligence about and disrupt Georgian military operations and hardware. News agencies across Georgia were also targeted, many of which had their websites either taken down or radically altered.
The bottom line: the trouble APTs and Remote Access Trojans are capable of causing is equal to the deviousness of the hacker (or hackers) behind them. Remote Access Trojans are bad news, which is why it’s so important to protect your systems against them.
How to Protect Yourself From RAT Software
While it perhaps sounds simple or obvious, the best way to avoid Remote Access Trojans is to avoid downloading files from untrustworthy sources. Do not open email attachments from people you don’t know (or even from people you do know if the message seems off or suspicious in some way), and do not download files from strange websites. Making sure your web browsers and operating systems are kept patched and up to date is also essential.
Creating brand-new Remote Access Trojans capable of avoiding detection is a time-intensive process, which means it’s usually more worthwhile for hackers to use them against larger targets like governments, corporations, and financial institutions. Home and small business networks can often benefit from antivirus software like Malwarebytes and Kaspersky, both of which are continually updating their databases of identified security threats, making them good RAT detectors. That said, antivirus software will not do much good if users are actively downloading and running things they shouldn’t.
Things become more complicated when you’re attempting to scale up security practices. It’s relatively easy for one person to monitor activity on their computer and avoid clicking suspicious links, but larger businesses or enterprises present a greater number of variables, including the degree of security awareness each end user within the organization brings to the table. Ongoing security education for users is always a good idea, but if you find yourself in the position of needing to detect RATs on computers across a network environment, there are further measures administrators can take.
That we continue to hear about Remote Access Trojans going undetected for years on workstations and networks indicates antivirus software isn’t infallible and shouldn’t be treated as the be-all and end-all for APT protection. RATs can easily go unnoticed among the multiple processes parallel programs generate, and if they employ rootkit techniques—which can mask an intrusion or interfere with software specifically designed to locate malware—they can be difficult to remove. While formatting a computer or server is a drastic move and can be inconvenient, especially if the malware has spread to multiple devices, it’s a surefire way to eliminate Remote Access Trojans.
The best option, especially for larger organizations, is to employ an intrusion detection system, which can be host-based or network-based. Host-based intrusion detection systems (HIDSs), which are installed on a specific device, monitor log files and application data for signs of malicious activity; network-based intrusion detection systems (NIDSs), on the other hand, track network traffic in real time, on the lookout for suspicious behavior. When used together, HIDSs and NIDSs create a security information and event management (SIEM) system. SIEM is an incredibly beneficial part of a strong security regimen and can help to block software intrusions which have slipped past firewalls, antivirus software, and other security countermeasures.
Larger companies, especially managed services providers (MSPs), also need a way to protect their email data and that of their clients. A lot of malware and other attacks are delivered via email, making this a potential vulnerability in your clients’ networks.
To help manage this risk, check out Mail Assure. This tool is designed specifically for MSPs, although it also works well for large organizations of all types. It offers a suite of cloud-based tools for enhancing email security.
Mail Assure provides advanced threat protection for both inbound and outbound emails. It also includes long-term email archiving, encrypted in order to help keep data secure. These features can go a long way toward minimizing the risks of Trojan and other malware attacks.
I’ve put together a list of 10 intrusion detection systems I recommend for use in Remote Access Trojan detection. My top pick is SolarWinds® Security Event Manager (SEM), a premium paid solution going beyond detection to block Remote Access Trojans. While most RAT detectors on the market are free and open source, they don’t come with the capabilities or support you’ll get with SEM.
10 Best RAT Software Detection Tools
Security Event Manager (SEM) is the option I most highly recommend. SEM is a host-based intrusion detection system including several powerful automated threat remediation features. SEM intrusion detection software is designed to compile and sort the large amounts of log data networks generate; as such, one of the primary benefits it offers is the ability to analyze vast amounts of historical data for patterns a more granular, real-time detection system might not be able to identify. This makes Security Event Manager an incredibly useful RAT detection tool, considering how APTs tend to stay under the radar over long periods of time.
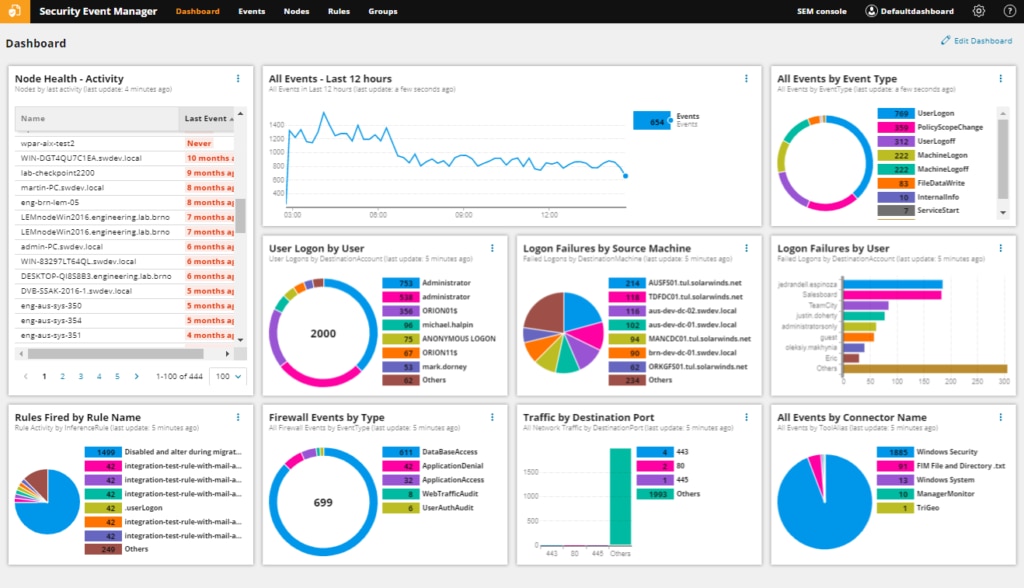
One standout feature of SEM is how it can incorporate and analyze logs from Snort as well as other connectors to provide greater visibility into security threats across your network. This log repository function essentially gives this tool many of the same insights as network-based intrusion detection and other supported vendors, allowing you to use it for both historical and real-time data analysis. (More about Snort below; the important thing here is the application’s packet sniffing functions are widely relied on across the industry.)
The ability to have a centralized log monitoring platform to combine and normalize data from host-based and network-based detection systems makes Security Event Manager an all-in-one SIEM tool creating a cohesive monitoring environment specifically designed to identify and respond to APT cyberattacks, giving you the ability to spot intrusion signatures in your log files and to track and stop live intrusion events.
In addition to the Remote Access Trojan detection portions of the application, Security Event Manager includes several other useful security elements, including streamlined reporting to help demonstrate you are in compliance with a range of data integrity standards, such as PCI DSS, HIPAA, SOX, and DISA STIG. Though it can only be installed on Windows, SEM is capable of collecting and analyzing log data from other operating systems like Linux, Mac, and more.
If want to try before you buy, take advantage of the 30-day free trial, during which SEM is fully functional.
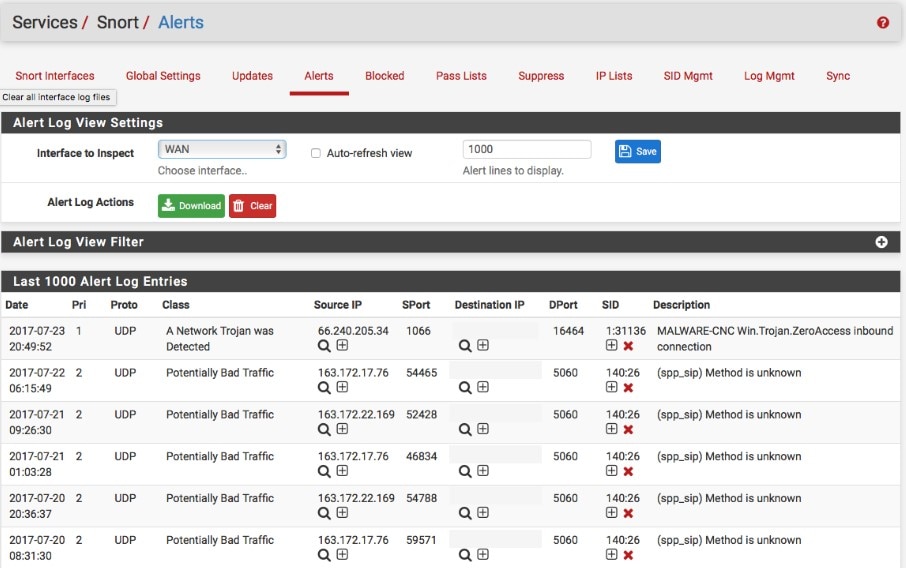
Snort is an open-source NIDS application used across the industry, in part because it includes so many useful security features. Snort comes with three monitoring modes: a packet sniffer mode, mentioned above, to monitor data packets moving across the network in real time; a packet logger mode to make a file record of packet traffic; and an intrusion detection mode which includes analysis functions.
The intrusion detection mode operates by applying threat intelligence policies to the data it collects, and Snort has predefined rules available on their website, where you can also download policies generated by the Snort user community. You can also create your own policies or tweak the ones Snort provides. These include both anomaly- and signature-based policies, making the application’s scope fairly broad and inclusive. Snort’s base policies can flag several potential security threats, including OS fingerprinting, SMB probes, and stealth port scanning.
While Snort is free to use, it’s also available via paid year-long subscriptions, to ensure your threat intelligence policies stay relevant and include the most recent updates. It integrates easily with other applications, and when paired with other open-source tools (such as Sagan—more on this below) can create a powerful SIEM toolset for IT admins on a budget or who like to customize protocols to their own specifications.
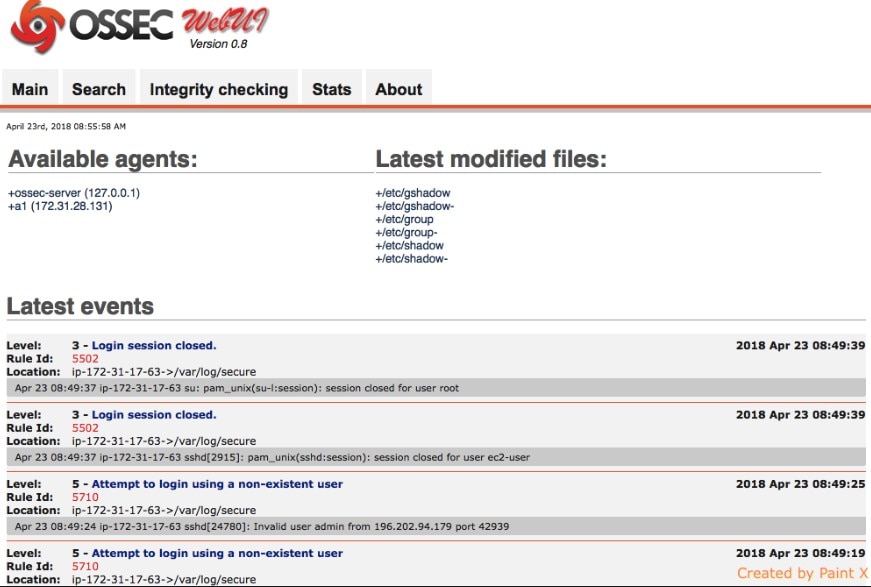
OSSEC is an open-source host-based intrusion detection system including system monitoring tools more commonly found in network-based intrusion detection systems. It’s incredibly efficient at processing log data, and, as with Snort, it gives you access to threat intelligence rules created by its community of users, which you can customize to fit your needs.
The downside? OSSEC’s user interface isn’t all that user friendly. However, OSSEC can easily integrate with other applications whose dashboards are easier to use—Graylog, Kibana, and Splunk are commonly paired with OSSEC.
OSSEC sorts and monitors log files and employs anomaly-based strategies for Remote Access Trojan detection. If you ever need technical support with something OSSEC related, the active user community provides free help, while a professional support package is available from Trend Micro—the firm publishing the application—for a subscription fee.
OSSEC runs on Linux, Mac OS, Unix, and Windows operating systems. For Windows systems, OSSEC not only monitors event logs for APT detection, but it also monitors the system registry for signs of tampering. For Mac OS, Linux, and Unix systems, it protects the root account. It offers reporting functions to keep you in data security compliance, too.
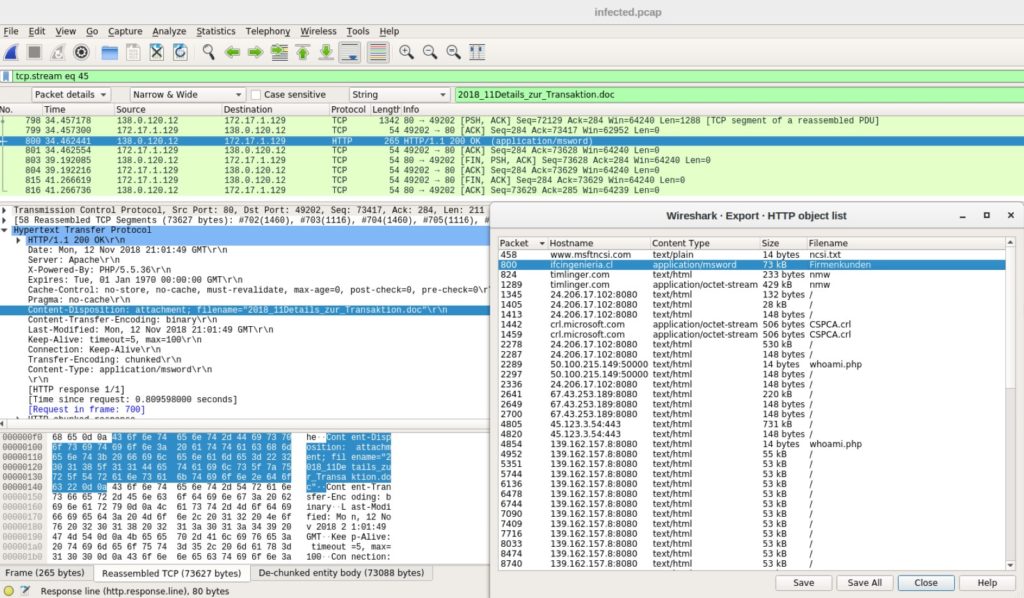
Zeek (formerly known as Bro) is a free, open-source network-based intrusion detection system for Linux, Mac OS, and Unix. Zeek not only tracks activity in real time, it also creates comprehensive logs of the behavior over time, creating a high-end archive of all activity occurring on the network it monitors—a necessary part of conducting forensic analysis during a security breach.
One way in which Remote Access Trojans can evade the live data analysis NIDSs provide is by dividing the command messaging sent through the malware across multiple data packets. NIDSs like Zeek, which focus more on application layers, are better able to detect split command messaging by running analyses across multiple data packets. This is one advantage Zeek has over Snort.
Zeek combats attempted intrusions by first flagging potential triggering events—including HTTP requests or new TCP connections—and then applying modifiable policies and scripts to determine the best way to address and remediate the identified security threat. In addition to tracking DNS, FTP, and HTTP activity, Zeek tracks SNMP notifications and can raise security alerts when it detects unauthorized changes to device configurations or SNMP Trap messaging. Zeek can allow for easy interfacing with third-party applications to quickly pass relevant information along multiple programs and systems.
Since the application’s inception more than two decades ago, the creators of Zeek have been interested in leveraging research and empirical data to refine its functionality. The end result is a flexible and adaptable intrusion detection system not limited to any one set of intrusion detection approaches and avoids using generic intrusion signatures. The publishers of Zeek are community oriented and strongly encourage involvement from the program’s users. They also have several ongoing research projects through the International Computer Science Institute at UC Berkeley, making this NIDS an especially good fit for academic entities and researchers.
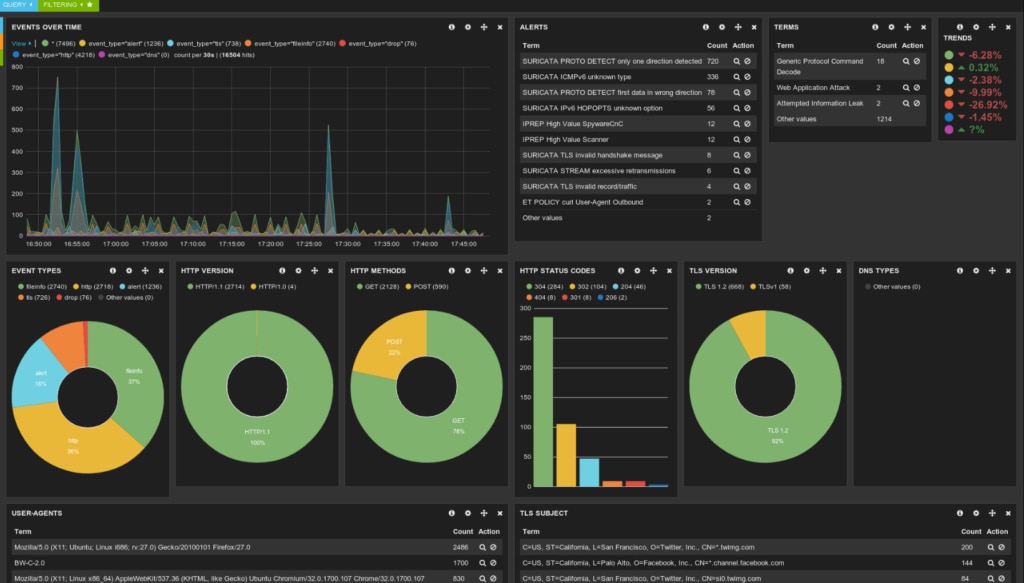
An open-source network-based intrusion detection system largely equivalent to Snort, Suricata can be installed on Linux, Mac OS, Unix, and Windows systems. Similar to Zeek, Suricata uses application layer analysis to identify Remote Access Trojan signatures split across multiple data packets.
Suricata leverages a combination of real-time intrusion detection, network security monitoring, and inline intrusion prevention to track various protocols, including IP, TLS, TCP, and UDP activity. It does this through the implementation of a complete signature language used to flag common cyberattack vectors and policy violations, and suspicious behavior that may be an indication of a security threat. The Suricata engine is compatible with Snort, so rules packages can be seamlessly imported from the latter to the former.
Built-in automatic protocol detection means when the Suricata engine identifies a potential threat, it’ll automatically administer a present response based on a set of predefined—but customizable—rules and logics. Automating these processes reduces the response time to potential threats, which makes it easy to identify and remove malware like Remote Access Trojans. Another built-in feature is a scripting module enabling the modification and combination of rules, allowing you to tailor and fine-tune the intrusion detection policies Suricata applies across your network.
Other features include the ability to log, store, and examine TLS certificates; to extract potentially infected files from data flows and store them to disk for analysis; and to leverage Lua scripting to assist in detecting more complex security threats. Suricata also logs HTTP activity requests, thereby cutting down on the need for additional hardware performing a similar function.
Suricata is designed to efficiently handle large amounts of network traffic, and a single instance can monitor multiple gigabytes of data each second. The code base for the Suricata engine is intentionally scalable and includes support for hardware acceleration, making it an excellent open-source option for organizations anticipating their networks expanding or changing in some fashion. It also features a sophisticated user interface providing extensive visual data representations for easy analysis and problem identification.
Suricata can require a lot of CPU usage to perform all its various functions, but its architecture spreads tasks across multiple processors—it can even tap your graphics card for a little extra horsepower—for multithreaded activity keeping the entire system from bogging down the computing resources of a single host.
Sagan is another open-source host-based intrusion detection system employing anomaly-based and signature-based detection policies. The application includes threat remediation countermeasures helping to quarantine security breaches once they’ve been identified. This HIDS also features a lot of built-in customization options to give you greater control over the intrusion triggers and thresholds creating alerts, as well as over defining the automated actions Sagan will take to address those threats. By interacting with firewall tables, Sagan can even lock down a network to prevent additional security breaches.
Another unique tool Sagan offers is an IP geolocation function, which will create alerts if it detects new or unauthorized activity from multiple IP addresses based out of the same physical location—which can be a sign of suspicious activity.
Sagan easily integrates with several other programs on this list. It was designed to be compatible with Snort’s packet sniffing module, and data from Suricata and Zeek can also feed into the Sagan dashboard.
Sagan’s primary function is log analysis, but its detection features and capabilities in the area of script execution make it worth noting as a useful component in a larger intrusion detection system. Though it can only be installed on Linux, Mac, and Unix, Sagan can still collect and analyze Windows event logs.
- Security Onion
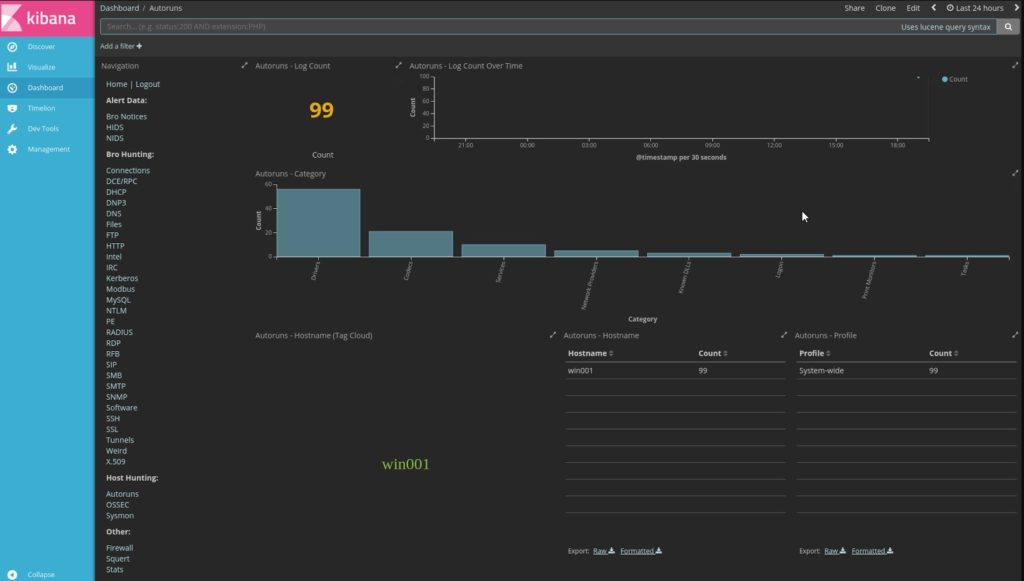
Security Onion is an interesting option for Remote Access Trojan detection, though not one I would suggest for newbies, or for those who want a fairly hands-off approach to their intrusion detection system.
A lot of the options on this list are open source, which means—and this is obvious, I know, but bear with me—each program’s source code can be downloaded and edited. So, you’re not far off to wonder if someone could combine the various open-source RAT detectors available into one powerhouse security application.
That’s precisely what Security Onion sets out to do. Using elements of the source code from OSSEC, Snort, Suricata, and Zeek, this Linux-based HIDS-NIDS hybrid is designed to run on Ubuntu and picks up pieces from other well-known open-source analysis tools like Kibana, NetworkMiner, Snorby, and Sguil. The combination of host-based and network-based functions allows Security Onion to not only survey network traffic for malicious activity but also monitor config and log files and run checksums on those files to detect unauthorized changes. Security Onion employs anomaly-based and signature-based alert policies and tracks device status and traffic patterns.
While this may at first sounds like an open-source dream come true—and Security Onion includes several useful tools, make no mistake—there are downsides. First is Security Onion can be somewhat complicated to use. The functionalities of each of the open-source programs it pulls code from are essentially stitched together and not seamlessly integrated. The range of operational structures included in Security Onion—especially when it comes to the analysis modules of the application—means each tool functions differently and somewhat separately, which can lead to users ignoring some of the tools entirely.
The Kibana dashboard does provide useful graphic representations for easier problem identification, but the lack of available reading material about everything the Onion is capable of means some experimentation will be required on the part of network admins. Security Onion also lacks some of the automated functions of other tools, meaning it requires a more manual approach.
Bottom line: This isn’t a tool I’d recommend for beginners, or for administrators who don’t have the time to tinker with the program to figure out its full functionality. For those who like taking a hands-on approach to their security and Remote Access Trojan prevention procedures, Security Onion offers several tools to test and implement.
AIDE—short for Advanced Intrusion Detection Environment—is a HIDS designed specifically to focus on rootkit detection and file signature comparisons, both of which are incredibly useful for detecting APTs like Remote Access Trojans.
The functionality AIDE offers is fairly comparable to the functionality of Tripwire threat detection software, but with the added benefit that it’s available for free (the company publishing Tripwire also offers a free version of the application, but a lot of the tools making Tripwire useful are only available in the Enterprise version). Designed for Unix operating systems, AIDE will also run on Linux and Mac OS.
When installed, AIDE uses config files to create a database of admin data, which it then uses as a sort of benchmark. AIDE includes anomaly-based and signature-based detection methods, and if any changes to systems settings or log files are detected, it can easily roll back those alterations to the original baseline.
There are downsides to this host-based intrusion detection system, one being system checks, by default, are only run on demand and not continuously. However, since AIDE operates as a command line function, you can configure it with cron or another operating method to run system checks periodically. While this doesn’t allow for real-time monitoring of log files, you can create a close approximation by scheduling AIDE to run system checks at short intervals.
While good for data comparison, AIDE does not include scripting languages; this may not be an issue for those who have some shell scripting chops, but it can make searching data and implementing rules more difficult. What it lacks in comprehensive intrusion detection tools, it makes up for in configuration management capabilities.
The design of this host-based intrusion detection system specifically targets suspicious or unusual events in log files and works to prevent attempted hacks by imposing blocks on IP addresses. For instance, if Fail2Ban notices a disproportionate number of failed login attempts, it’ll block the IP address generating the attempts. This can obstruct brute force password cracking attempts and can even prove an effective deterrent to denial-of-service (DDoS) attacks. The bans Fail2Ban institutes are not permanent, though—their duration is adjustable, and by default they usually last a few minutes.
Fail2Ban uses combinations of filters to define its monitoring scope, and the services it oversees include Apache, Courier Mail Server, Lighttpd, and Postfix. It also pairs filters with auto-response actions—the combination of which is known as a “jail”—to activate when certain threat conditions are triggered. Written in Python, Fail2Ban has the capability to write to system tables to block addresses it identifies as being the source of suspicious activity. Lockouts happen in netfilter/iptables and PF firewall rules, and the hosts.deny table of TCP Wrapper.
One thing to be aware of with Fail2Ban is it does have some intrusion protection system functions. Since the application can automatically take action to remediate what it considers threats, administrators will need to make sure their policies aren’t so tightly configured they lead to locking out legitimate users from accessing the networks, applications, or other computing environments required to perform their daily tasks. The focus on repeated actions from individual IP addresses can be limiting as well. So, while Fail2Ban is good for stopping DOS attacks, it’s not nearly as effective at preventing DDoS attacks or distributed attempts to crack passwords.
Fail2Ban can be used on Mac OS, Linux, and Unix operating systems.
Samhain is another free and open-source host-based intrusion detection system. One distinctive feature is it can run either on a single device or on several—the application compiles data from log event files gathered from the agents running on each monitored machine. These agents can run various tasks, including rootkit virus detection, port monitoring, rogue user access detection, and hidden process detection. This allows Samhain to manage multiple systems—even those running different operating systems—from a centralized interface, using encryption to protect the communication between agents and the central console. Strict authentication protocols assist in preventing hackers from disrupting or stopping the monitoring processes, as well.
One extremely useful feature Samhain offers is stealth-mode monitoring. When entering a system, hackers will often be able to spot and stop detection processes to remain hidden, but Samhain cloaks those processes with what is called steganography.
While the data Samhain collects and compiles will flag intrusions and allow administrators to analyze activity on hosts across the network, the tool lacks the ability to block intruders or to kill rogue and unauthorized processes. For this reason, maintaining backups of user identities and config files is a necessary part of running it effectively. Samhain also uses a PGP key to protect central log files and config backups from modifications or tampering by hackers.
Samhain can be installed on Linux, Mac OS, and Unix operating systems, and possibly even Windows under Cygwin.
How to Select the Right Remote Access Trojan Detection Software
All APTs are bad news, and Remote Access Trojans are especially pernicious. While there are several measures that can be helpful depending on the size of the environment you’re looking to protect—including security awareness training and antivirus software—intrusion detection systems are your best bet for preventing a Remote Access Trojan from slipping past your security setup.
Pairing a host-based intrusion system with a network-based one is the most effective way to provide complete coverage for your environment. This combination helps to ensure any unusual or suspicious activity detected in configuration changes and root access on your monitored devices will be immediately flagged as a potential security threat—it also ensures strange activity in the traffic flows on your network will be identified. SolarWinds Security Event Manager has it all in this regard: its features go beyond detection, incorporating automated incident responses to remediate threats.
Of course, which tool is right for your organization will be a matter of budget, convenience, as well as weighing which features you cannot do without and which would be nice but aren’t absolutely necessary. While there’s much to be said for the convenience, automation, and access to support teams paid options offer, many free tools have active user communities to help troubleshoot issues or answer questions. Should you opt for an open-source solution, you should take advantage of these dynamic and expanding resources. However, investing in a comprehensive tool like SolarWinds SEM will be well worth it in the long run.
