SAP security is a technical module that works within SAP systems to allow access where it’s needed and prevent access where it’s not. Establishing good internal security and access processes is a vital part of helping ensure your SAP system is protected and will function well. Protecting against external threats is important, but internal threats should not be underestimated. Make sure you manage them!
In this comprehensive introduction to SAP security, I review what SAP is, how it works, and how to best use it in your organization. I also list what I believe are the three leading access rights and security tools that can help support your SAP security strategy, including a review on the SAP security features included in SolarWinds® Access Rights Manager.
What Is SAP Security?
SAP (short for Systems, Applications, and Products in data processing) is the company behind SAP ERP (Enterprise Resource Planning) software. SAP security is a module that keeps certain kinds of data under lock and key while allowing access to others, working to ensure your SAP system is secure from both external and internal threats. This is a comprehensive introduction to SAP security: what it is, how it works, and how to best use it in your organization.
Why Is SAP Security Important?
SAP systems store large amounts of confidential or sensitive data. Users on your network using an SAP system must have access to everything they need to do their jobs; at the same time, they should not have access to important data, such as financial records or confidential information. If an employee accidentally accesses data that should be restricted, they could cause problems by deleting or moving something. An even worse scenario is if someone accesses sensitive data deliberately, whether to damage your business, leak data or commit fraud. Moreover, for compliance reasons, in some industries (like those involving health or financial data), certain types of information must be carefully protected.
How Does SAP Security Work?
The SAP ERP offerings include software dealing with goods and services, sales, finance, accounting, human resources, manufacturing, and logistics. All businesses need systems that are interconnected with the ability to share information between different parts of the business as needed. ERP systems integrate back-office functions, like organizational plans, data analysis, stock management, and governance planning—as well as front-office functions, including customer relationship management (CRM) and e-business.
ERP is comprised of several applications, including those relating to human resources, accounting, CRM, sales, and so on. By integrating these processes and centralizing their management, you can save time and money.
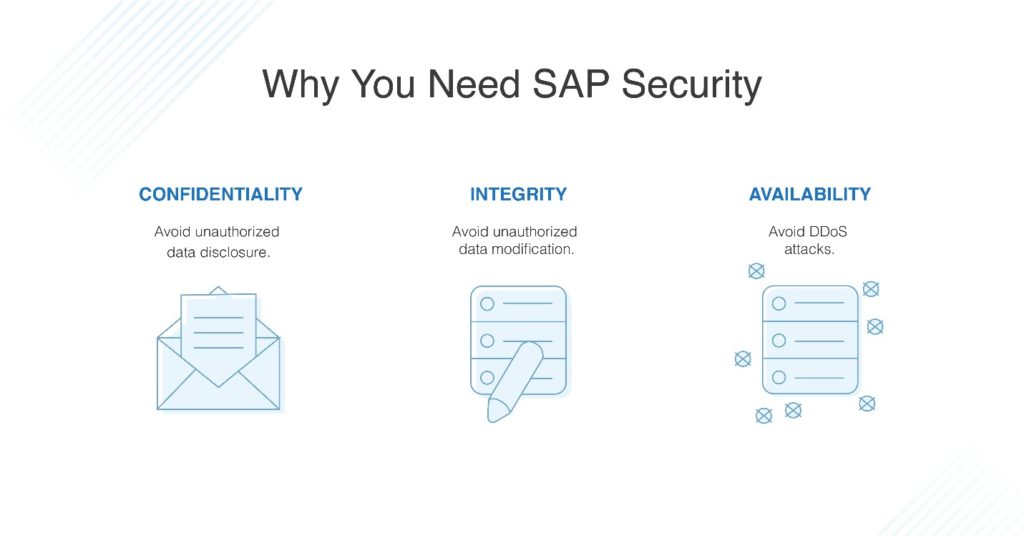
Once the SAP system is set up, SAP security is there to help ensure that the system works as intended, without any problems with security or data access. There are three areas that SAP security deals with:
- Confidentiality. This means no data should be disclosed in an unauthorized manner.
- Integrity. No data should be modified in an unauthorized way.
- Availability. Distributed denial-of-service (DDoS) attacks should not occur.
How to Set Up SAP Security?
When using SAP systems, access to both application servers and database servers has to be controlled. User accounts that are set up in an SAP system should be clearly defined as roles with specific permissions (or lack thereof) to prevent unauthorized access to data. This helps prevent unauthorized modification of data and protects the system, as a whole, from damage or data losses.
Security should be spread over multiple different layers and aspects of the system, such as using a firewall, controlling access, encrypting data, and using digital certificates, as well as antivirus and security management software. With that in mind, here are the key steps to securing your SAP system:
-
Align Settings
SAP security settings should be aligned with organizational policies on who has access to which data, and which data needs to be carefully protected or kept confidential. You should also ensure that your organization follows basic security protocols, such as requiring users to use passwords that have a minimum length or combination of characters and prevent access to a system or database after a set number of failed password attempts.
Make sure you know who has a sensitive role in your organization, as the most powerful roles (with the most access) are also the ones that carry the most risk.
-
Create Emergency Procedures
In the event that an SAP security problem arises, network administrators need to have the appropriate permissions to be able to change and remove privileges from other users in the SAP system. This is necessary for network administrators to manage the SAP security process, and it all needs to be pre-established and set up so that they can react quickly in the event of an issue.
-
Housekeeping and Review
Always keep tabs on who has access to which data, when they have access, where, and why. Good housekeeping means that you should keep this list updated regularly. When people change roles within an organization, or new people join, security access lists can get out of date quickly.
-
Security Tools
Using security tools that monitor SAP access can more easily highlight any issues or gaps in the processes you have established and reduce the risk of an internal attack or data breach occurring. This also frees up your IT team to focus on other tasks.
There are several different tools that you can use to help establish SAP security, including access management software and other types of security tools.
1. Access Rights Manager
My recommended tool for managing access security is the SolarWinds Access Rights Manager (ARM). ARM also now includes support for SAP R/3. This lets you search for security-critical transaction codes, and simultaneously recognize multiple authorizations. You can also see which Active Directory users are assigned to each SAP account through the ARM interface, and can create, modify, or delete user access to different files or types of files as you desire.
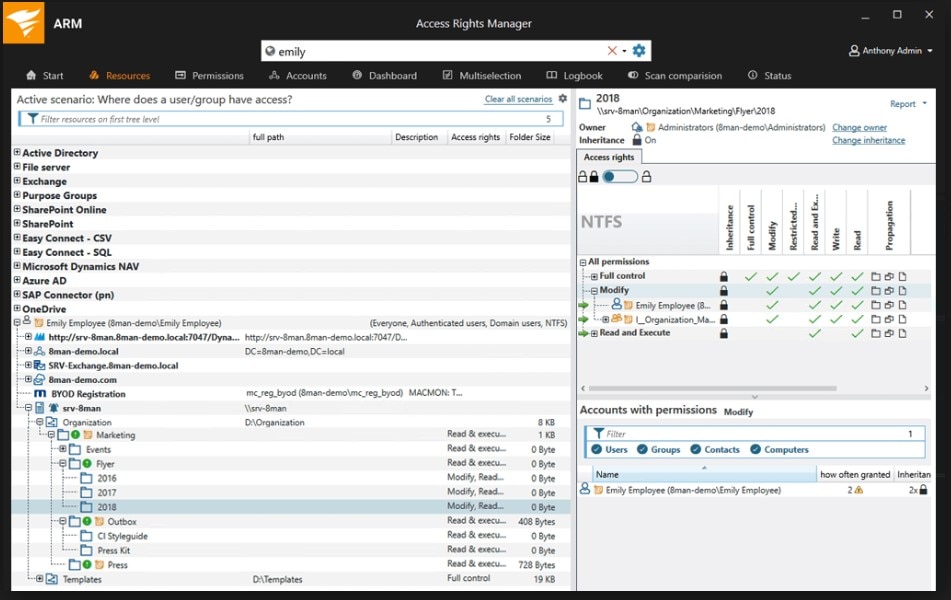
ARM can monitor and audit changes to both the Active Directory and Group Policy, which helps you keep track of potentially unauthorized users as well as malicious or accidental data damage. The alerting system also works well, and it can quickly flag file changes and permission changes that are not expected, which can help the network administrator quickly see that a potential issue has arisen.
ARM allows you to essentially automate the task of access rights management and build auditor-ready user access reports for compliance purposes, which can save a huge amount of time for IT professionals. Overall it is easy to use and is an excellent all-around tool to help your business stay abreast of internal security risks.
2. Symmetry SAP Access Control Suite
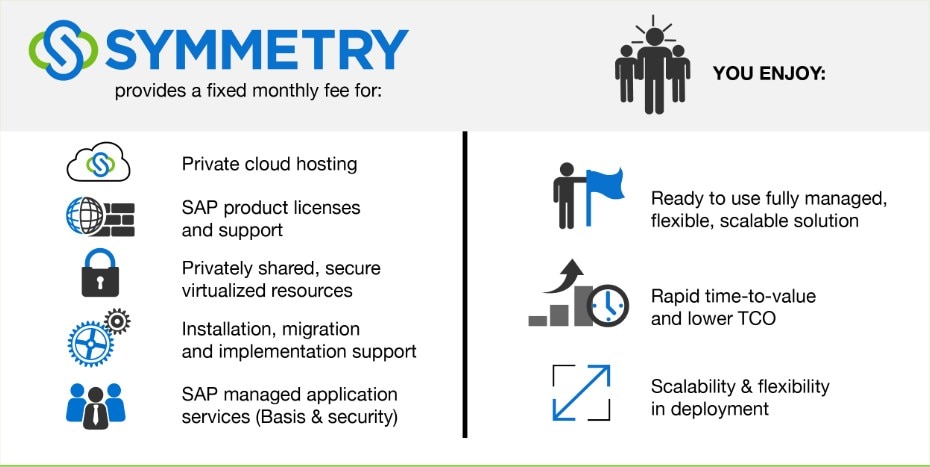
The Symmetry Access Control Suite works to provide SAP risk analysis and sensitive data determination so that you can avoid compliance failures or unauthorized data breaches. It also allows you to easily remediate segregation of duties (SOD) conflicts and control access to your SAP software. It includes SAP emergency access procedures and can log and track everything a user does within a particular session.
3. Netwrix Auditor
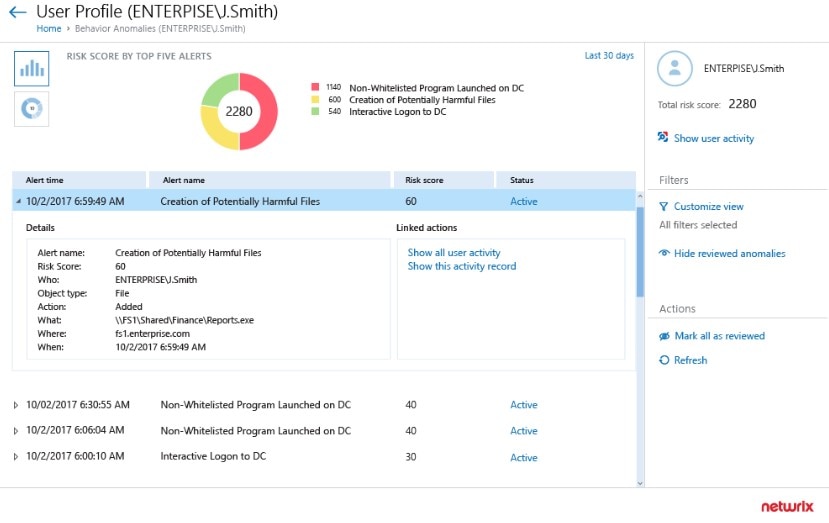
The Netwrix Auditor works to identify and classify sensitive or regulated information consistently and accurately, whether it’s stored on-premises or in the cloud. It delivers security intelligence to keep track of who has access to what, and when and how users access data on your servers. It also produces reports that can meet a wide range of security standards, including PCI DSS, HIPAA, SOX, GDPR, GLBA, FISMA/NIST, and CJIS. You can try a free trial or purchase the software on a per-user basis.
SAP Security Solutions
While SAP security processes can be handled by your internal IT team, they may also need additional skills or support to manage all the risks. One of the best solutions is to outsource some of your SAP security monitoring needs to an external security tool like Access Rights Manager, which you can try the full product out free for 30 days to see if it meets your SAP security needs.
Recommended Reading
What is HIPAA Compliance?: Health data is sensitive, and it’s important to follow HIPAA compliance procedures to keep it protected. If your business has a HIPAA violation, you can be subject to huge fines. Read up on how to comply with HIPAA requirements and keep patient health data safe.
