As businesses expand, they typically need to scale up their IT networks, so they can access a more extensive range of capabilities. Unfortunately, some businesses overlook appropriate management activities, security needs, and performance optimization requirements. Understanding network audit steps, taking advantage of a comprehensive network audit checklist, and using network audit tools can help your business gain visibility into potential issues. This means the issues can be rectified before they cause downtime and impact business performance.
Network audit tools and network audit software can help you streamline and automate the network audit steps, assist with network compliance management and network compliance monitoring, and increase overall productivity. This guide will answer the question: What is network auditing? It includes an overview of the process and a network audit checklist, followed by a ranking of the best network audit tools currently on the market. Overall, SolarWinds® Network Configuration Manager (NCM) tops the ranks as the most advanced and user-friendly solution.
Skip to Best Network Audit Tools List >>>
What Is Network Auditing?
Network auditing refers to the collective measures involved in gathering, analyzing, and studying data on a network, to determine its health in relation to regulatory compliance standards. Network auditing gives businesses insight into how effective their network control and management practices are, especially internal and external network compliance policies and regulations.
Network Auditing Components
Network auditing is conducted through a systematic process, which involves analyzing the following network components:
- Control Implementation
- Management
- Availability
- Security
- Performance
Network Audit Steps
A network audit entails gathering data, identifying threats and vulnerability, and compiling a formal audit report, which is then sent on to network administrators. Audits are usually performed by an information system auditor, a network analyst, or another individual with a background in network management and IT security. Both manual and automated techniques are used to gather data and review overall network health.
Here are common network audit steps required to perform a comprehensive network audit:
- Record audit details
- Ensure procedures are documented
- Review the procedure management system
- Assess training logs and operations
- Review security patches for network software
- Review the penetration testing policy and process
- Test software
- Identify firewall holes
- Ensure sensitive data is stored separately
- Encrypt company laptop hard disks
- Confirm wireless networks are secured
- Scan for unauthorized access points
- Review the event log monitoring process
- Compile a report
- Send a report to appropriate stakeholders
It’s worth bearing in mind, although a network audit prioritizes network control and security, it also reviews the operations and measures contributing to network quality of service, network performance, and network availability.
Network Audit Checklist
Conducting a network audit is an essential part of ensuring the functionality and reliability of your business network. If this isn’t made a priority, your network is likely to underperform. The following network audit checklist guides you through the key considerations of an audit. When creating a network audit template, it’s important you include these processes.
✔ Review Your Bring-Your-Own-Device (BYOD) Policy
Your employees will almost certainly bring their personal devices into the workplace and connect them to the network, which causes slower speeds, increases bandwidth demands, and exposes your network to potential security risks. It’s crucial for this practice to be managed carefully, starting with establishing clear and considered policies.
There are challenges associated with developing a robust BYOD policy; these include the use of unapproved third-party applications, exposure to unsecured networks, and the presence of unknown hardware. By reviewing your BYOD policy, you’ll gain insight into which devices are connecting to your network, the vulnerabilities associated with and created by each of them, and who’s responsible for managing the devices. This awareness can help you minimize network exposure as much as possible.
✔ Review Network Cybersecurity Vulnerabilities
Cybersecurity vulnerabilities are weaknesses likely to be exploited by hackers attempting to gain access to your network. These vulnerabilities can exist in many places, including hardware, software, and your physical surroundings. Some vulnerabilities can be resolved with minimal time and effort but identifying and fixing most weaknesses begins with a professional network audit.
Prominent vulnerabilities include outdated security patches, poor password management, and personal devices connecting to your enterprise network.
✔ Review Bandwidth Demands
Bandwidth is’t unlimited, and it must be shared among your users. Bandwidth usage and distribution monitoring can help you determine whether your network needs to be expanded, and whether any individual devices and applications are experiencing bandwidth issues needing to be addressed.
When you have a clear view of bandwidth usage, you’ll gain an understanding of which applications should and shouldn’t be prioritized, and where congestion is happening. Managing traffic flow effectively can even help you improve performance.
To assess bandwidth demand correctly, it’s important you compare wired and wireless connections, as this helps you identify bottlenecks. To gain a complete understanding of which network components you should prioritize, it’s recommended you employ network audit tools.
✔ Review Infrastructure Problems
Your network infrastructure includes both software and hardware components. Hardware includes access points, switches, and cables. Software includes applications, operating systems, and firewalls. Infrastructure doesn’t, however, usually include endpoints like servers and personal devices.
It’s key you examine bandwidth patterns and update patches, as this contributes to the maintenance of a healthy infrastructure. Keep in mind, there are several other notable and common infrastructure problems, like forgotten firewalls and load balancers. Issues of this nature can result in major disruptions within your IT department. A network map can help you diagnose and rectify these issues quickly and efficiently.
✔ Plan Network Upgrades
The most important part of a network audit is what you learn from it. Having a network audit checklist and network audit template is useless unless you rectify any issues. Businesses shouldn’t consider their work done once the network audit report has been compiled. This is the time to determine whether hardware and network upgrades might boost performance.
A network upgrade could involve updating cabling, creating clearer policies, adding more access points, or updating your firewall. Remember, one of the most common reasons behind poor network performance is your hardware needs an upgrade. When a network upgrade is planned and implemented carefully, it can assist your company with resolving connectivity issues and improving the overall user experience.
Best Network Audit Software
In a business environment, dependable network performance is a crucial factor in streamlining operations and maintaining productivity. This can only be achieved when you’re afforded access to clear and complete data regarding your network capacity.

A network audit can be highly valuable for IT departments, giving them the knowledge necessary to effectively implement targeted upgrades while maintaining optimal cost-efficiency. Network audit tools and network audit software can help your business succeed in this endeavor in the most resourceful and timely manner. Many network audit tools allow you to take advantage of advanced utilities you wouldn’t otherwise have access to.
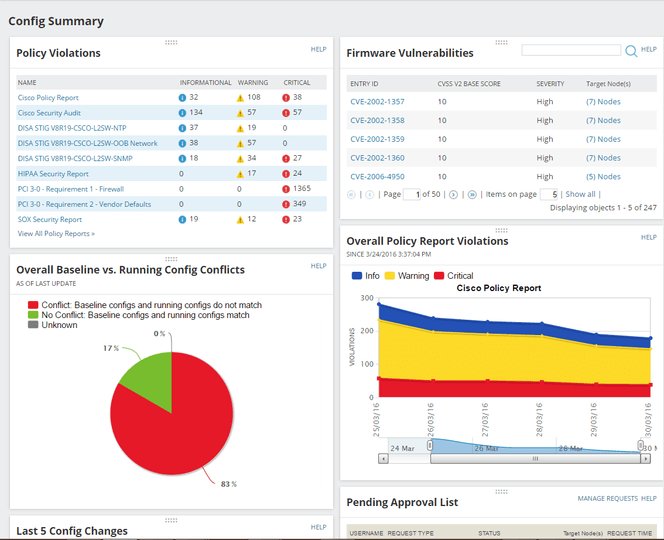
SolarWinds NCM is a highly versatile and powerful network audit software offering network vulnerability assessment, network compliance, network automation, configuration backup, network insights for Cisco Nexus and Cisco ASA, and much more. This network audit tool can be integrated with SolarWinds Network Performance Monitor (NPM), significantly extending its functionalities. These two tools together give users an all-in-one network monitoring and management solution (download a bundle with both NCM and NPM free trials here).
NCM integrates with the National Vulnerability Database, ensuring its vulnerability assessment capabilities are highly dependable. It also has access to the most recent CVEs, or Common Vulnerabilities and Exposures, which allows it to identify Cisco device vulnerabilities.
With NCM, maintaining up-to-date network inventory on all your devices is easy, saving you time otherwise spent compiling and updating device details. This network audit software automatically discovers and imports your devices, populating your network inventory report with the relevant details.
NCM scans network devices for weaknesses, identifies devices approaching end-of-life status, and gathers key device data. It’s a one-stop solution for multi-vendor device management needs, with the capacity to generate comprehensive vulnerability scanning and device data inventory reports. This tool lets you manage device data for routers, switches, and other network devices from vendors including Dell, Juniper, HP, Cisco, and Aruba.
SolarWinds NCM can help you improve network security by performing proactive automated compliance network assessments. Reports can be created for NIST FISMA, STIG, PCI DSS, and DISA, assisting with the identification of security threats and gaps. This information facilitates violation remediations, creating a script whenever a violation is detected and running it automatically.
This tool offers an impressive range of sophisticated capabilities but remains easy to use and highly intuitive. A 30-day free trial is available for download.
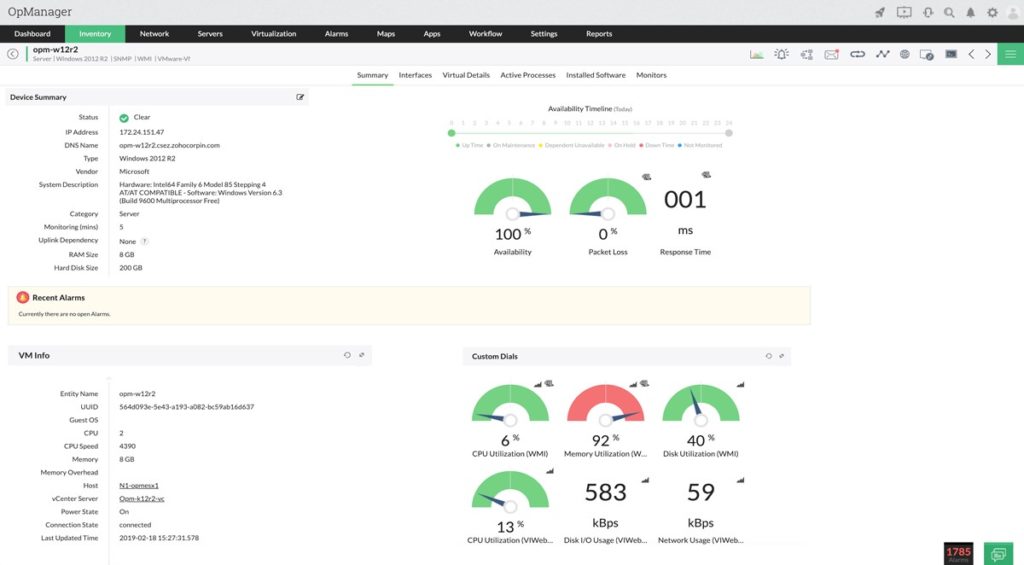
ManageEngine OpManager is another popular network audit tool, which helps you identify performance bottlenecks, configuration violations, and security breaches in real time. This tool uses automated network scanning to discover all devices on your network, and maintains a comprehensive, up-to-date device inventory. Key information—like IP address, system description, vendor, OS version, device health, and traffic counter—is included in the inventory.
OpManager monitors the performance, health, and availability of network devices. It can monitor more than 2,000 metrics, giving you critical insights into device performance. This tool also features bandwidth monitoring capabilities, which let you monitor packet loss and bandwidth usage by top N applications, top N users, and top N devices using flow technologies.
This network audit software comes with over 100 pre-built reports on performance, availability, health, and more. Reports can be customized to suit your needs and exported as PDFs or Excel sheets.
Although OpManager is a popular advanced solution, it could be more user-friendly. To give it a try, risk-free, you can download a 30-day free trial.
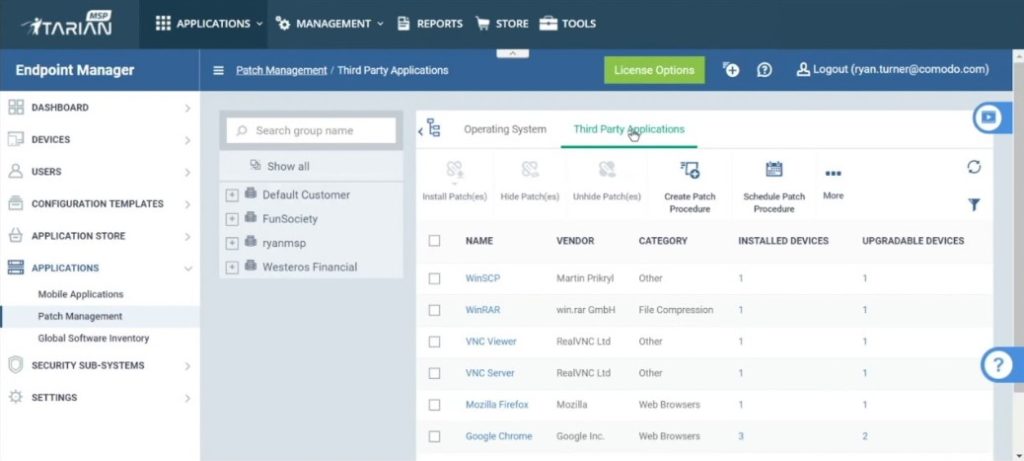
ITarian’s free Network Assessment tool was designed to make the job of network administrators easier. One of its best features is the easy setup wizard, which lets you import networks via Active Directory, IP range, or workgroup.
This network audit tool lets you perform in-depth scans, identifying an array of network, server, and endpoint vulnerabilities. ITarian prepares risk reports for scanned networks automatically, in addition to compiling a risk mitigation plan with actionable advice. This helps you address each problem in an informed and considered way.
This cleverly designed tool is especially suited to managed service providers. It’s comprehensive, and its reporting capabilities are especially extensive, including the ability to customize your reports according to your business needs. You can create client risk summary reports, XP migration readiness reports, change management reports, full detail reports, Excel export reports, and asset detail reports.
You can sign up for this network audit software here.
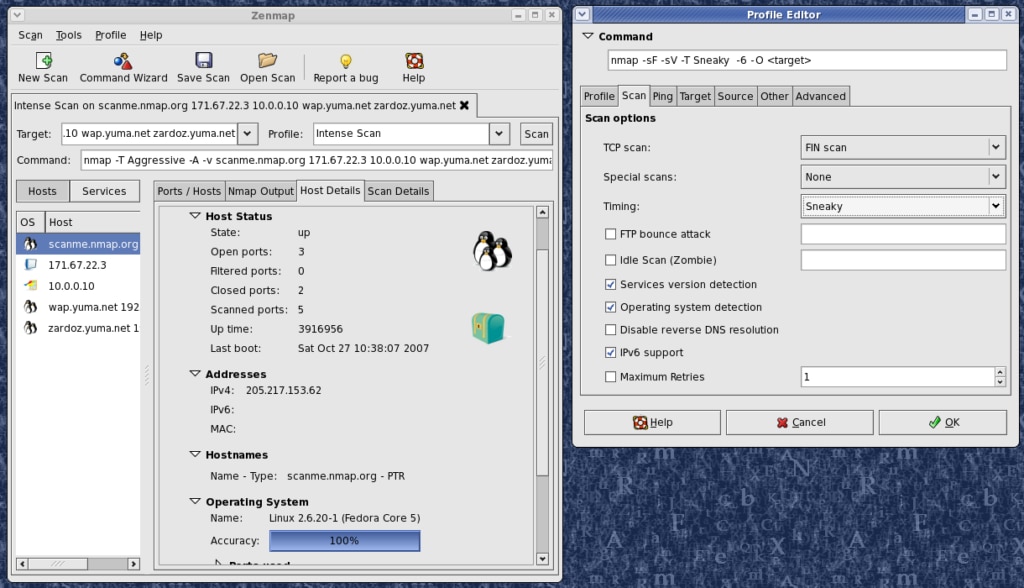
Nmap, also known as Network Mapper, is an open-source security auditing and network discovery tool. It has a flexible design and an array of features, making it ideal for creating a network inventory, managing upgrade schedules, and monitoring server uptimes.
Nmap uses raw IP packets to discern device information at a specific IP address. It can identify what type of packet filters and firewalls are being used, what services are offered by hosts, what hosts are available, what operating systems are being run, and more. It can also scan multiple IP addresses simultaneously, saving users a significant amount of time.
Nmap was designed to scan large networks in a short time, but it can also scan single hosts. It can be run on all major operating systems, and official binary packages are available for Linux, Windows, and Mac OS X. The Nmap suite of tools includes:
- An advanced GUI and results viewer
- A flexible data transfer, debugging, and redirection utility
- A utility for comparing scan results
- A packet generation response analysis utility
Although some IT professionals prefer open-source tools because they offer greater flexibility, they’re not especially suited for business use. You can download Nmap here.
Getting Started With Network Audit Software
If you’re experiencing regular network failure, or you believe your network isn’t performing as it should be, then there’s no better time to undertake a network audit. This will help you refine your network compliance management and network compliance monitoring strategy and streamline your IT infrastructure’s functionality. Network audit software like SolarWinds NCM can help you do this.
NCM offers an impressive array of sophisticated capabilities, in addition to a user-friendly experience. This network audit software is ahead of the market curve, with unique utilities you aren’t likely to find anywhere else. For reliable network audit software, it comes highly recommended. You can download a free trial here.
