Identity theft has been on the rise for decades, as technology designed to make our lives more convenient makes us increasingly vulnerable. Stealing someone’s identity is easier, cheaper, and faster than it’s ever been, and the chance of getting caught is minimal, so it’s no wonder identity theft is so often the average cybercriminal’s crime of choice. As identity theft continues to rise, IT security software developers are saturating the market with identity monitoring solutions to protect people and businesses.
Identity theft takes a massive financial, emotional, social, and physical toll on its victims. In a 2016 Identity Theft Resource Center survey of people who have been victims of identity theft, 8% even reported feeling suicidal. The same survey reported among identity theft victims, 55% missed work, 44% lost out on an employment opportunity, and 23% feared for their physical safety. Since the consequences of identity theft for the victim can be so extreme, investing in the best identity monitoring service is very important.
But with so many tools on the market, choosing between them can be difficult. I’ve put together this identity monitoring comparison to help you make the right choice for your situation.
For companies searching for a solution to improve corporate credentials account security, I consider SolarWinds® Identity Monitor to be the best data breach leakage monitoring system available today. It offers an advanced and sophisticated solution to identity theft, without compromising on user-friendliness by combining automation with human intelligence to minimize the risk of identity theft as much as possible.
Feel free to jump ahead to each tool review:
To find out more about the basics of identity monitoring and how top identity theft products on the market compare, read on.
Best Data Breach and Identity Monitoring Services
The following list ranks the best identity monitoring services on the market today. Data breach protection and identity monitoring should be a priority for everyone, but we all have different requirements. I’ve considered varying needs when creating this identity monitoring comparison, to help you with choosing the best identity monitoring protection solution for you.
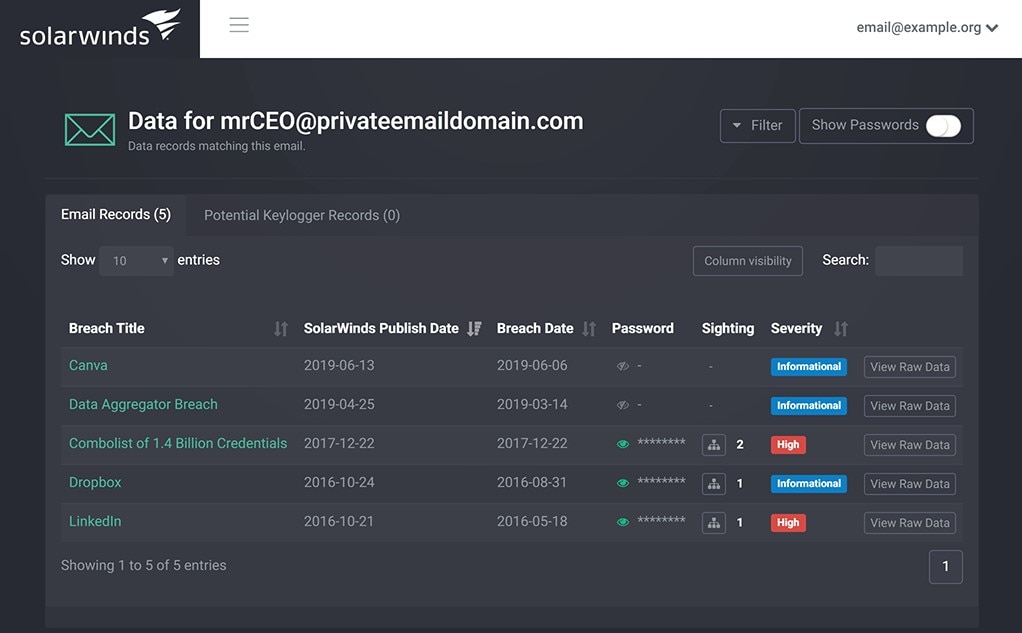
I could fill an entire guide with everything there is to love about SolarWinds Identity Monitor. To keep things brief, I’ll focus on my favorite features and benefits. I’ll start with the user interface: Identity Monitor boasts a simple dashboard with an easy navigation menu. The layout makes navigating between views, dashboards, and settings easy. You won’t need to spend hours learning how to find everything, which means you can get started right away. This contributes massively to the overall user-friendliness of the program. It has clearly been designed in an intuitive and informed way, because every button is located exactly where you’d want it to be.
Identity Monitor monitors your email domains for any exposure, protecting your credentials. Because reacting quickly to a potential leak is of critical importance, Identity Monitor will notify you instantly if your credentials appear in a data leak. This means you can reset passwords and inspect recent logins as quickly as possible, before any damage can be done. When you’re alerted to monitored domains appearing in a data leak, you can force a password reset for the affected accounts, which will make the leaked credentials effectively useless. The data collected by Identity Monitor comes in from multiple sources and will have varying levels of severity. To help you understand the right course of action to take, each record is accompanied by contextual details.
With Identity Monitor, you can monitor IP addresses for potential malware. Add an IPv4 address or an IPv4 network CIDR to your watchlist, and it will be monitored for breaches and botnets. If an IP address is matched from a botnet, this could mean an employee has active malware on their device stealing credentials. Having this information enables you to take rapid action.
This tool allows you to monitor the private email credentials of key and high-ranking employees, which can help you prevent your employees from falling into the hands of scammers. Identity Monitor also facilitates multiple domain monitoring, to afford you complete visibility and coverage. You can monitor all your domains for exposure in a data breach, and you’ll be notified if one of your domains appears as having associated credentials in a breach. This way, you can act before an account takeover attempt is made.
All in all, SolarWinds Identity Monitor is a simple but extremely effective tool. It monitors data for breaches with the utmost diligence, affording you a reliable and robust solution. It’s the best identity monitoring tool, in my view, because it’s beginner-friendly, effective, and scalable. You can check the exposure associated with an email address here, and you’ll then be able to view how many personal records have been exposed and when personal records were last exposed.
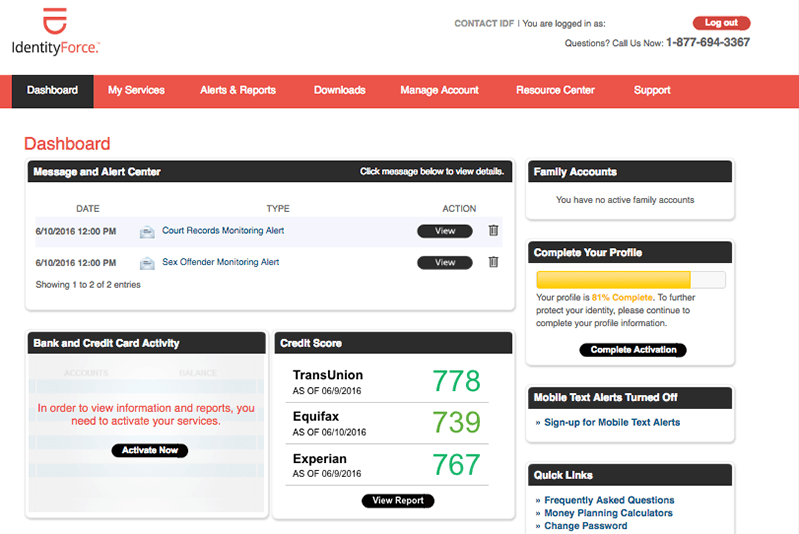
Soniq IdentityForce is an obvious contender for the highest-ranking tool on this list, but it comes second because it’s not as cost-effective as it could be. It is, however, a proven privacy, identity, and credit security solution, with advanced detection technology. IdentityForce offers 24/7 support with round-the-clock threat monitoring and alerting, and it’s backed by 40 years of industry experience. This product has managed to keep pace with the evolving threat of identity theft, to create a highly durable and evergreen identity theft monitoring service.
One of the best things about IdentityForce is how it delivers complete coverage of your personal information, using innovative identity theft protection technology to execute a proactive approach to potential threats. This is combined with an early warning system, which notifies you instantly if your personal data is at risk. Alerts can be sent to your tablet, smartphone, or computer, which means you don’t need to be at your desk to remain informed.
IdentityForce helps you increase your power over your own data by giving you valuable insights into your credit score and how your information is being used online. It enables you to proactively protect your PINs, your credit card information, and even your keystrokes. Knowledge of what’s at risk helps you achieve optimal protection over your data—this is a key selling point of IdentityForce, which prioritizes the improvement of user knowledge.
The tool includes fully comprehensive 24/7 recovery services. If something goes wrong, IdentityForce can save you hundreds of hours by making calls and filling out paperwork on your behalf, diligently going over even the smallest of details until your identity is fully restored. The program also covers you with a nationwide $1 million identity theft insurance policy.
Identity Force takes a five-pronged approach to identity theft monitoring: Monitor, Alert, Control, Recover, and Credit. Each aspect encompasses an array of features designed to boost the effectiveness of the program.
- Monitor
-
- Advanced fraud monitoring
- Court records monitoring
- Change of address monitoring
- Dark web monitoring
- Sex offender monitoring
- Payday loan monitoring
- Alert
-
- Smart SSN tracker
- Bank and credit card activity alerts
- Junk mail opt-out
- Fraud alert reminders
- Identity threat alerts
- Control
-
- Medical ID fraud protection
- Two-factor authentication
- Lost wallet assistance
- Mobile application
- Online PC protection tools
- Recover
-
- Identity theft insurance
- Fully managed restoration
- Toll-free customer service
- Credit
-
- Three-bureau credit monitoring
- Credit score tracker
- Credit score simulator
This is a comprehensive and sophisticated program. It does, unfortunately, come at a high price—and, at times, at the cost of user-friendliness. A 14-day free trial is available.
IdentityIQ is another identity theft monitoring program good at offering all-around protection. It combines credit reporting and score delivery, credit monitoring, dark web monitoring, identity protection, application monitoring, identity restoration, and family protection utilities to provide a suite of protection tools designed to give you peace of mind. It comes with up to $1 million in identity theft insurance, covering lost wages, legal expert services, and the reimbursement of stolen funds.
IdentityIQ’s enhanced credit monitoring capabilities are among its most notable features. They allow you to monitor your credit on an entirely new level. You’ll be alerted to changes when users are added to your credit cards and when your TransUnion score has changed by 10 or more points, giving you the opportunity to act quickly if something doesn’t seem right. Enhanced credit protection through IdentityIQ notifies you of paid collections, new foreclosures, paid trade lines, retail cards going over the limit, new authorized card users, bank cards going over the limit, closed trade lines, collections (excluding medical), a decrease or increase in collection balances, lost or stolen cards, and any new charge-offs. This wonderfully comprehensive range of features is something few other products can offer.
The dark web monitoring utilities are also noteworthy. IdentityIQ will keep an eye on the dark web, scanning it for any information possibly related to your identity. The search is global, scanning for any trace of your name, social security number, mailing address, or other information you’ve designated as sensitive. And it conducts this search in more than 25 languages. If anything unusual or suspicious is discovered, you’ll be notified immediately.
Discovering your identity has been stolen is only half the battle. Restoring your identity is just as grueling, if not more, and can lead to serious stress. IdentityIQ personally assists with the restoration of your identity, assigning a case manager who will help you devise a plan of action and support you throughout the process.
I particularly like the family protection component to this program. IdentityIQ recognizes children are also vulnerable to synthetic identity theft. Often, child identity theft goes unnoticed until they’re adults. To help protect your family, the IdentityIQ Secure Max plan gives you up to $25,000 of identity theft insurance for your children. Unfortunately, family protection doesn’t include parents or spouse, only children.
IdentityIQ features a selection of plans. The higher-paid plans don’t add much value, except for the family protection offered by Secure Max. Nonetheless, IdentityIQ is a comprehensive and effective identity theft monitoring solution. No free trial is available.
Identity Protect is provided by Intelius, which also offers background check services. Identity Protect includes a range of protections, including credit and debit card monitoring, social security number monitoring, bank account protection, phone number monitoring, and address monitoring. It also comes with up to $1 million of insurance to cover any damages incurred from identity theft, like legal fees and reimbursement of stolen funds.
I like Intelius because their specialism in background checks means you get more extensive access to public records monitoring than most identity monitoring tools can provide. This means you could access the records of your relatives and associates, their addresses, and sex offender and property reports.
Like IdentityIQ, Intelius offers 24/7 assistance from restoration experts who will help you restore your identity if it’s been stolen. They’ll assist you with canceling cards, resolving fraud disputes, and contacting the police. However, Intelius has an unfortunate reputation for offering poor customer service, which is a shame because the Identity Protect product itself is very effective. A 7-day free trial is available.
Understanding Personal Data Risks
The internet poses a major threat to privacy, especially if we don’t take measures to protect ourselves. Our health records, banking details, and social security numbers are all stored online. There’s the location data we allow search engines and other programs to use, the information we haphazardly give away in social media posts—like our location and date of birth—and search engine queries revealing more than we might like about us. Search queries can be monetized, allowing companies to target you with tailored advertisements. Some companies even analyze the way you use your smartphone, from the keys you use to the way you navigate between applications.
You may be wondering about consent. Consent is important, of course, but there’s some gray area around it in many cases, especially when it comes to personal data. Sometimes we sign up to fork over our data unknowingly. Maybe we didn’t read the full terms and conditions. When a little pop-up appears asking if we accept our data being used, many of us ignore or overlook it. In most cases, we agree to give up some of our data, but we don’t understand exactly what we’re giving up or what it will be used for.
The specifics of this personal data sharing are usually buried in terms-of-service agreements several pages long, making them hard to access. Being informed in the age of terms and conditions is difficult—after all, most of the services we use were expressly designed to make our lives more convenient. We want rapid gratification, which these applications and services promise. If we were to investigate thoroughly before handing over our personal data, the internet and applications we use would start to feel far less convenient and gratifying. Undoubtedly, certain companies leverage this fact to legally access our personal data and sell it off.
Here are some examples of how your data might be being used:
- You want to use an ancestry service for insight into your genetics. You send a vial of your saliva to an organization providing this service, believing all you’re doing is giving away your DNA to a genomics company. You don’t realize your DNA will be resold to pharmaceutical firms.
- You’re using an application on your smartphone. In exchange for use of the app, your location data is taken and used to tailor custom advertisements to you. You’re aware of this, but you don’t know a hedge fund may purchase your location data from the application developer to analyze which shops you regularly visit.
- A specific advertisement seems to be following you around the web, wherever you go. You understand your location has been revealed to a company that’s customizing this advertisement specifically to you. What you do not know is companies may be recording not just the clicks of the mouse, but its precise movements.
In each of these examples, the user is aware some of their personal data is being shared, but they don’t know how much, or how it’s being used. They’ve received something—knowledge of their ancestry, use of a mobile application, or the ability to browse products from the comfort of their home desktop—but they weren’t aware of the actual cost of these activities: their personal data. Social media and communication platforms are the most popular example of this exchange. Instagram, Facebook, and Gmail don’t cost you money, but that doesn’t mean they’re free. You pay with your personal data, which is used to tailor advertisements to you.
Our data is everywhere. It’s being bought, sold, and bartered. This is why identity theft has become so much easier in recent years. Finding personal information isn’t like looking for a needle in a haystack. It’s widely available. Hackers just have to know where to look.
How Are You Being Tracked?
There are two main categories of online trackers: cross-site, which tend to be invasive, and same-site, which are mostly benign. The main tracking methods are as follows:
- Traditional cookies. These are used by companies like Google and Facebook. They’re cross-site trackers, which follow users between websites. They deposit a piece of code into the browser, and users then carry this code with them as they move from web page to web page.
- Super cookies. These are inserted into HTTP headers to uniquely identify devices and are designed to be difficult to remove. They were used by Verizon, which had to pay a fine of $1.35 million to the Federal Communications Commission.
- Fingerprinting uses cross-site trackers to follow users by establishing a unique profile on the device being used. This collects IP address, screen resolution, and type of computer.
- Identity trackers. These aren’t common, but they substitute for cookies. They follow users by using personally identifiable data, like an email address. An identity tracker hides on login pages and collects credentials when they’re entered.
- Session cookies. These same-site scripts keep you logged in to websites and preserve your shopping cart, even if you close your browser. These cookies aren’t malicious.
- Session replay scripts. These same-site scripts are invasive. They record everything done on a website, like what products you look at, and sometimes they even record your password.
Basics of Identity Monitoring
Are you at risk of identity theft? There’s a simple answer: yes. Almost anyone can fall victim to having their identity stolen. However, this doesn’t mean you can’t significantly reduce the chances of it occurring. If you’re vigilant about protecting your personal data and take measures to prevent it being easily accessible, you have a good chance of avoiding identity theft.
Unfortunately, you’re not the only person holding your information. Your employer, insurers, internet provider, and tax officials have access to some of your most valuable personal information. Large-scale data breaches do happen, meaning even major databases are not invulnerable. In 2017, the Equifax hack meant 143 million Americans were at high risk of identity theft after a huge quantity of sensitive data—like social security numbers—was leaked.
There are a few key ways to protect your identity. You can use credit reports to identify any suspicious activity, analyze your bank and credit card statements for unfamiliar purchases, lock up important documents in multiple secure locations, and shred paperwork with personal information on it. But the most effective way to prevent identity theft is to invest in the best identity monitoring system you can.
Best Identity Monitoring Service
Identity theft is a serious concern. One in two consumers has been notified of a data breach, and almost one in four people has experienced identity theft. Putting a freeze on your credit card may not be enough, because identity theft extends well beyond credit fraud. With data like your social security number and birthdate potentially accessible to criminals, tax returns can be filed in your name, investment accounts stolen from, and medical bills pushed through the roof.
And just because you have resolved one breach doesn’t mean there won’t be more to come. Data breaches usually expose information that doesn’t change, like your birth date or social security number. This means breaches can occur years after the initial breach. Given the severity of the consequences when identity theft does occur, ensuring you have access to the best identity monitoring service available is of critical importance.
SolarWinds Identity Monitor tops my list of data breach monitoring solutions. This tool manages to combine simplicity with highly advanced technology to deliver a solution that’s easy to use, beginner-friendly, and cost-effective. It’s also scalable, meaning it’s suitable for anyone and any business, big or small. So, if your organization grows, you won’t have to worry about switching to a new tool. SolarWinds Identity Monitor was built to cope with growth and bear the weight of your identity monitoring concerns. You can check to see if your email credentials have been leaked on the Identity Monitor page.
